Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove DMOSK Virus. The step by step removal works for every version of Microsoft Windows.
DMOSK is a recently-discovered Trojan menace. In case, you’re unfamiliar, these are atrocious cyber threats. Trojans are a hazard to your system’s well-being. The DMOSK tool is no exception. The Trojan is written in the Java language of programming. It follows specific instructions, when it comes to attacking users. The end-game is the theft and usage of saved emails, and email credentials. Once your PC gets compromised, the tool collects every email-related detail from you. The Trojan tends to target companies more so than the average home user. In fact, the cyber criminals behind the threat limit their campaign. They target certain companies. They manage that by blacklisting IP addresses, and Internet-connected services. The Trojan’s targets receive spam emails. They contain a file with the name ‘doc.php.’ If that file makes its way onto your computer, brace yourself! It downloads a payload in the form of ‘scan.jse.’ And, you will not enjoy its content. The presence of ‘scan.jse’ on your PC, leads to the appearance of yet another nasty file. That third file, you end up with, is called 38781520.scr. You may find this boring, or confusing, but it’s important. That’s the process of how your computer gets riddled with infected files. Don’t think it ends with 38781520.scr. No. The chain of infection continues, and you get stuck with far more than three mere files. The SCR file drops another file, then another one, and another one, and so on. Don’t let the dreadful threat spread its nastiness and corruption throughout your system. Protect yourself from its hazardous influences. Do your best to get rid of the nasty infection as soon as the opportunity presents itself. If you don’t, you’re in for a horrendous experience. Trojans have NO place on your computer. Get rid of DMOSK ASAP.

How did I get infected with?
Trojans are masterful in the art of deception. They have an array of methods, they can turn to, when it comes to invasion. Most threats resort to the old but gold means of infiltration. They present a clear path that leads straight to your system. The usual antics involve the following. Freeware, fake updates, corrupted sites or links. And, of course, spam email attachments. As already explained, that’s the preferred means of invasion of the DMOSK threat. But here’s the thing. Regardless of the method, it uses, the Trojan can’t succeed without you. It needs you, if it’s to sneak into your system undetected. Or, rather, your carelessness. The infection’s successful invasion rests on your distraction, naivety, and haste. It needs you to throw caution to the wind, and rely on luck. To rush, and skip doing due diligence. Don’t oblige! Do your best to always be attentive! Even a little extra attention can save you countless issues. Choose caution over the lack thereof. It provides the far better alternative.
Why is this dangerous?
As stated, the DMOSK Trojan’s end goal is to get a hold of, any and all, email-related information. Among other things, that includes your logins, passwords, saved emails you may keep. Everything, the infection may later find useful. After it gets a hold of that data, it proceeds to use it for nefarious purposes. Think about it. If it has your login details, it can access your email account, and send emails from your behalf. Emails, which contain the DMOSK threat. Thus, spreading the dreadful infection to unsuspecting victims. Do your best to avoid that dreadful scenario. Contain the hazardous influences of the nasty Trojan. Don’t let it spread its clutches throughout your system. And, then, to countless more. DMOSK has no place on your system. Cut its stay as short as possible. For every additional moment, it spends on your PC, you face a myriad of repercussions. None of which, you’ll enjoy. Remove the hazardous cyber threat the first chance you get. It’s the best course of action, you can take. And, your future self will thank you for it. Do it now.
Manual DMOSK Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The DMOSK infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the DMOSK infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down DMOSK related processes in the computer memory
STEP 2: Locate DMOSK startup location
STEP 3: Delete DMOSK traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down DMOSK related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate DMOSK startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean DMOSK virus from the windows registry
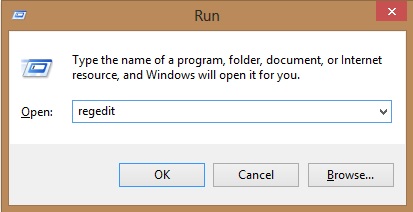
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
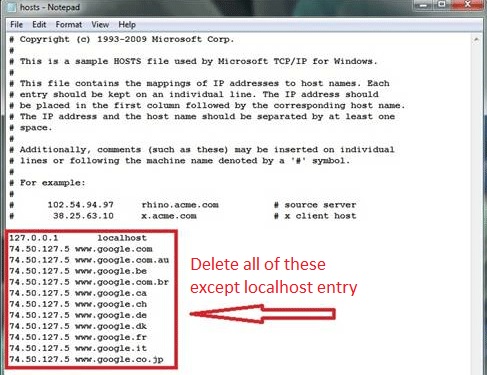
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by DMOSK
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for DMOSK, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove DMOSK Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.