Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove RDM File Extension Ransomware?
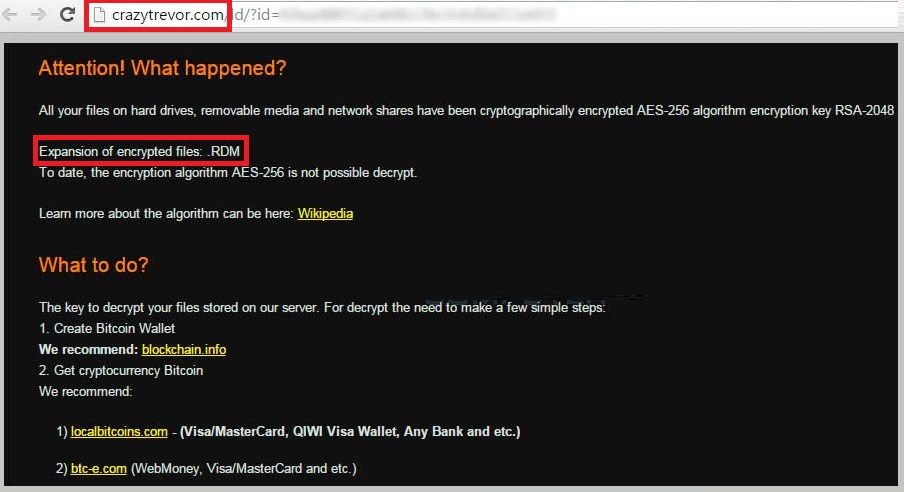
RDM File Extension is the file extension that a newly discovered malicious software called Radamant Ransomware Kit will encrypt all your personal files. It’s not something you’d ever want to see on your computer. Ever. That’s because after it slithers its way into your system, it corrupts it entirely. The infection completely takes over and encrypts the files with the following extensions:
1cd, dbf, dt, cf, cfu, mxl, epf, kdbx, erf, vrp, grs, geo, st, pff, mft, efd, 3dm, 3ds, rib, ma, sldasm, sldprt, max, blend, lwo, lws, m3d, mb, obj, x, x3d, movie.byu, c4d, fbx, dgn, dwg, 4db, 4dl, 4mp, abs, accdb, accdc, accde, accdr, accdt, accdw, accft, adn, a3d, adp, aft, ahd, alf, ask, awdb, azz, bdb, bib, bnd, bok, btr, bak, backup, cdb, ckp, clkw, cma, crd, daconnections, dacpac, dad, dadiagrams, daf, daschema, db, db-shm, db-wal, db2, db3, dbc, dbk, dbs, dbt, dbv, dbx, dcb, dct, dcx, ddl, df1, dmo, dnc, dp1, dqy, dsk, dsn, dta, dtsx, dxl, eco, ecx, edb, emd, eql, fcd, fdb, fic, fid, fil, fm5, fmp, fmp12, fmpsl, fol, fp3, fp4, fp5, fp7, fpt, fpt, fzb, fzv, gdb, gwi, hdb, his, ib, idc, ihx, itdb, itw, jtx, kdb, lgc, maq, mdb, mdbhtml, mdf, mdn, mdt, mrg, mud, mwb, s3m, myd, ndf, ns2, ns3, ns4, nsf, nsf, nv2, nyf, oce, odb, oqy, ora, orx, owc, owg, oyx, p96, p97, pan, pdb, pdb, pdb, pdm, phm, pnz, pth, pwa, qpx, qry, qvd, rctd, rdb, rpd, rsd, sbf, sdb, sdb, sdb, sdf, spq, sqb, stp, sql, sqlite, sqlite3, sqlitedb, str, tcx, tdt, te, teacher, tmd, trm, udb, usr, v12, vdb, vpd, wdb, wmdb, xdb, xld, xlgc, zdb, zdc, cdr, cdr3, ppt, pptx, 1st, abw, act, aim, ans, apt, asc, ascii, ase, aty, awp, awt, aww, bad, bbs, bdp, bdr, bean, bib, bna, boc, btd, bzabw, chart, chord, cnm, crd, crwl, cyi, dca, dgs, diz, dne, doc, doc, docm, docx, docxml, docz, dot, dotm, dotx, dsv, dvi, dx, eio, eit, email, emlx, epp, err, err, etf, etx, euc, fadein, faq, fb2, fbl, fcf, fdf, fdr, fds, fdt, fdx, fdxt, fes, fft, flr, fodt, fountain, gtp, frt, fwdn, fxc, gdoc, gio, gio, gpn, gsd, gthr, gv, hbk, hht, hs, htc, hwp, hz, idx, iil, ipf, jarvis, jis, joe, jp1, jrtf, kes, klg, klg, knt, kon, kwd, latex, lbt, lis, lit, lnt, lp2, lrc, lst, lst, ltr, ltx, lue, luf, lwp, lxfml, lyt, lyx, man, map, mbox, md5txt, me, mell, min, mnt, msg, mwp, nfo, njx, notes, now, nwctxt, nzb, ocr, odm, odo, odt, ofl, oft, openbsd, ort, ott, p7s, pages, pfs, pfx, pjt, plantuml, prt, psw, pu, pvj, pvm, pwi, pwr, qdl, rad, readme, rft, ris, rng, rpt, rst, rt, rtd, rtf, rtx, run, rzk, rzn, saf, safetext, sam, scc, scm, scriv, scrivx, sct, scw, sdm, sdoc, sdw, sgm, sig, skcard, sla, slagz, sls, smf, sms, ssa, strings, stw, sty, sub, sxg, sxw, tab, tdf, tdf, tex, text, thp, tlb, tm, tmd, tmv, tmx, tpc, trelby, tvj, txt, u3d, u3i, unauth, unx, uof, uot, upd, utf8, unity, utxt, vct, vnt, vw, wbk, wbk, wcf, webdoc, wgz, wn, wp, wp4, wp5, wp6, wp7, wpa, wpd, wpd, wpl, wps, wps, wpt, wpw, wri, wsc, wsd, wsh, wtx, xbdoc, xbplate, xdl, xdl, xlf, xps, xwp, xwp, xwp, xy3, xyp, xyw, ybk, yml, zabw, zw, 2bp, 0,36, 3fr, 0,411, 73i, 8xi, 9png, abm, afx, agif, agp, aic, albm, apd, apm, apng, aps, apx, art, artwork, arw, arw, asw, avatar, bay, blkrt, bm2, bmp, bmx, bmz, brk, brn, brt, bss, bti, c4, cal, cals, can, cd5, cdc, cdg, cimg, cin, cit, colz, cpc, cpd, cpg, cps, cpx, cr2, ct, dc2, dcr, dds, dgt, dib, dicom, djv, djvu, dm3, dmi, vue, dpx, wire, drz, dt2, dtw, dvl, ecw, eip, erf, exr, fal, fax, fil, fpos, fpx, g3, gcdp, gfb, gfie, ggr, gif, gih, gim, gmbck, gmspr, spr, scad, gpd, gro, grob, hdp, hdr, hpi, i3d, icn, icon, icpr, iiq, info, int, ipx, itc2, iwi, j, j2c, j2k, jas, jb2, jbig, jbig2, jbmp, jbr, jfif, jia, jng, jp2, jpe, jpeg, jpg, jpg2, jps, jpx, jtf, jwl, jxr, kdc, kdi, kdk, kic, kpg, lbm, ljp, mac, mbm, mef, mnr, mos, mpf, mpo, mrxs, myl, ncr, nct, nlm, nrw, oc3, oc4, oc5, oci, omf, oplc, af2, af3, ai, art, asy, cdmm, cdmt, cdmtz, cdmz, cdt, cgm, cmx, cnv, csy, cv5, cvg, cvi, cvs, cvx, cwt, cxf, dcs, ded, design, dhs, dpp, drw, drw, dxb, dxf, egc, emf, ep, eps, epsf, fh10, fh11, fh3, fh4, fh5, fh6, fh7, fh8, fif, fig, fmv, ft10, ft11, ft7, ft8, ft9, ftn, fxg, gdraw, gem, glox, gsd, hpg, hpgl, hpl, idea, igt, igx, imd, ink, lmk, mgcb, mgmf, mgmt, mt9, mgmx, mgtx, mmat, mat, otg, ovp, ovr, pcs, pfd, pfv, pl, plt, pm, vrml, pmg, pobj, ps, psid, rdl, scv, sk1, sk2, slddrt, snagitstamps, snagstyles, ssk, stn, svf, svg, svgz, sxd, tlc, tne, ufr, vbr, vec, vml, vsd, vsdm, vsdx, vstm, stm, vstx, wmf, wpg, vsm, vault, xar, xmind, xmmap, yal, orf, ota, oti, ozb, ozj, ozt, pal, pano, pap, pbm, pc1, pc2, pc3, pcd, pcx, pdd, pdn, pe4, pe4, pef, pfi, pgf, pgm, pi1, pi2, pi3, pic, pict, pix, pjpeg, pjpg, pm, pmg, png, pni, pnm, pntg, pop, pp4, pp5, ppm, prw, psd, psdx, pse, psp, pspbrush, ptg, ptx, ptx, pvr, px, pxr, pz3, pza, pzp, pzs, z3d, qmg, ras, rcu, rgb, rgb, rgf, ric, riff, rix, rle, rli, rpf, rri, rs, rsb, rsr, rw2, rwl, s2mv, sai, sci, sct, sep, sfc, sfera, sfw, skm, sld, sob, spa, spe, sph, spj, spp, sr2, srw, ste, sumo, sva, save, ssfn, t2b, tb0, tbn, tex, tfc, tg4, thm, thumb, tif, tiff, tjp, tm2, tn, tpi, ufo, uga, usertile-ms, vda, vff, vpe, vst, wb1, wbc, wbd, wbm, wbmp, wbz, wdp, webp, wpb, wpe, wvl, x3f, y, ysp, zif, cdr4, cdr6, rtf, cdrw, jpeg, djvu, pdf, ddoc, css, pptm, raw, cpt, gif, jpeg, jpg, jpe, jp2, pcx, pdn, png, psd, tga, tiff, tif, hdp, xpm, ai, cdr, ps, svg, sai, wmf, emf, ani, apng, djv, flc, fb2, fb3, fli, mng, smil, svg, mobi, swf, html, xls, xlsx, csv, xlsm, ods, xhtm
Nothing is safe from its reach. Pictures, videos, music, documents, every single piece of data is encrypted, and you can no longer access it. You can see it, but you cannot open it. That’s because everything has been renamed, and now includes some weird .rdm extension. Once it has successfully taken over your data, the tool demands you pay ransom if you wish to regain possession. It requests payment in bitcoins, which is equal to more than $200 USD. That’s a lot of money to pay for something with utterly NO guarantees of success. Oh, yes. Whichever action you choose to take – pay, not pay, ignore, etc., you essentially have no guarantees that you’ll get your files back. Let’s elaborate. There are several ways this little escapade can go down. Say, for example, you decide to pay the ransom. The first scenario is: you pay, and the infection provides you with a decryption key. You use it and get your data decrypted. But then, what’s to stop the ransomware from kicking right back in the very next day? Here’s your answer: nothing. Nothing is keeping the tool from putting you in the same situation, over and over again. How long do you think you’ll be able to keep up with the payments? And, what’s worse than throwing money to the wind, you’ll also be granting access to your private information to strangers with wicked agendas. Do you think that’s wise? Hardly. And, what’s worse, the other scenarios are as equally horrific. Maybe even more so. The most important thing you need to understand is NOT to trust this tool! Nothing about it screams ‘trustworthy’ or ‘reliable.’ It’s not. It’s a hazardous infection, which only seeks to exploit you for profit. Don’t allow it to succeed!
How did I get infected with?
How do you suppose you got stuck with such a nasty infection? After all, id didn’t just magically pop up out of the blue. The RDM File Extension shows up on your PC, in the same manner, all such cyber infections do – deception and finesse. Like all similar viruses, the ransomware preys on your carelessness to slither its way into your system. More often than not, it turns to the old but gold methods of invasion for assistance with the infiltration. That includes hiding behind corrupted links or sites or hitching a ride with freeware or spam email attachments. Also, it can pose as a bogus update. For example, while you’re lead to believe you’re updating your Java or Adobe Flash Player, in actuality, you’re installing a hazardous infection. To prevent that from happening, remember that such tools rely on your distraction and haste. So, don’t provide them! Be extra vigilant and do your due diligence. Don’t rush and don’t leave everything to chance or luck. Be more cautious, and you might be surprised by how much trouble and headaches, even a little extra attention can save you.
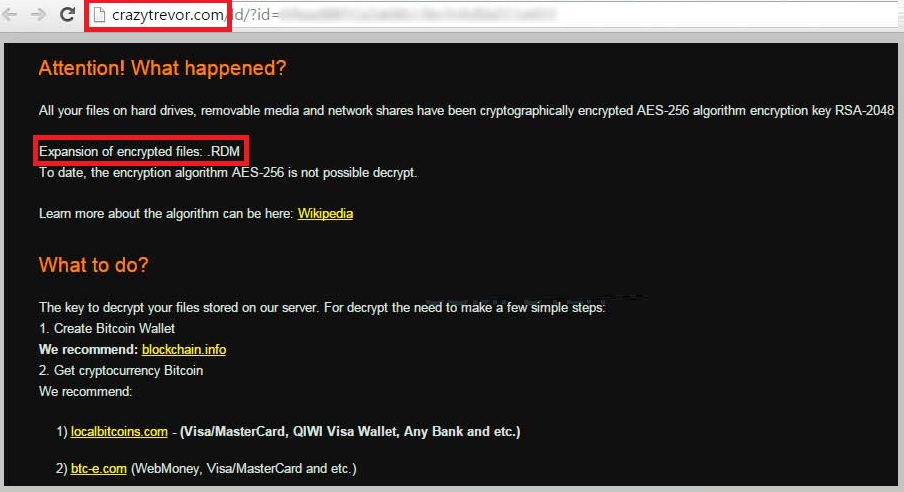
Why is this dangerous?
The RDM File Extension virus operates in a manner, common to all such infections. When it gains access to your PC, it copies itself to C:\Windows\directx.exe, and creates autorun registry keys, thus, ensuring that it starts every single time you log in to Windows. That’s why they’re so hard to get rid of. They do a good job of latching on your system pretty tightly. Once the ransomware infects your system, it proceeds with its havoc-wreaking and takes over. When it’s done encrypting your files, it shows you a website. That site provides you with the information you need to go through with its requested ransom payment. The page, you’ll soon come to hate with all your being, is perceived as the Command & Control server for the ransomware. It’s hosted on the domains crazytrevor.com or crazytrevor.in. As was already stated, the page pops up, it clues you in on what you have to do to get your hands on the decryption key. It displays the ‘joyous’ news that if you wish to take back control of your data, you have to pay some serious cash in bitcoin. That’s a popular strategy among such infections. Don’t go through with the payment! It can only get worse while it’s highly unlikely that it can get better. The RDM File Extension virus is NOT to be trusted! As unpleasant as it may sound, it’s best to cut your losses, and accept that your files are lost to you. But there is a ray of sunshine! To end the article on a more positive note, know that there is an antimalware specialist, who has successfully created a partially working decryptor. So, the fight is not completely lost! There is still hope you can recover your encrypted data without giving into the harassment of a hazardous ransomware.
RDM File Extension Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
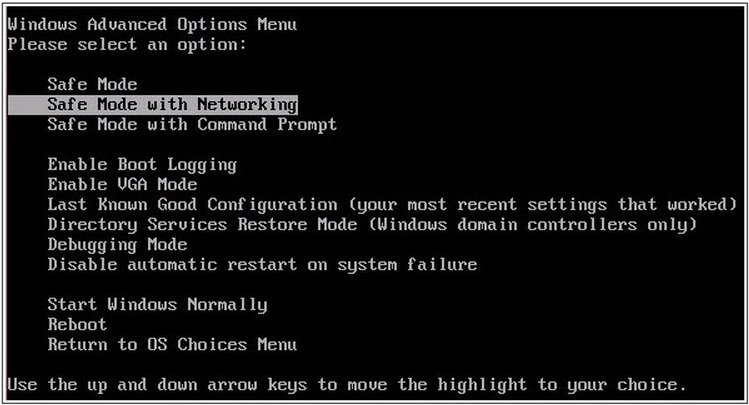
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.
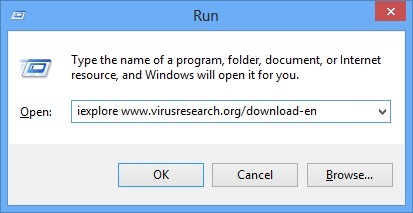
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove RDM File Extension malware Manually
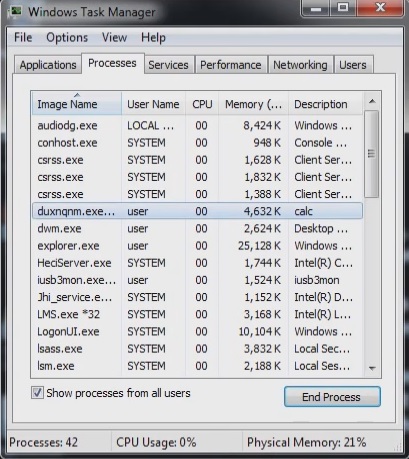
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process named directx.exe. Have in mind that this can also be a random generated file.
Before you kill the process, type the name on a text document for later reference.
- Open your Windows Registry Editor and navigate to
HKCU\Software\Microsoft\Windows\CurrentVersion\Run:svchost
and
HKLM\Software\Microsoft\Windows\CurrentVersion\Run:svchost
- delete the name svchost
if you are using 64 bit operating system the location of the registry entries will be respectively
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run:svchost
HKCU\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run:svchost
- Close the Windows registry editor
- Open your Explorer and navigate to
%Desktop%\YOUR_FILES.url
C:\Windows\directx.exe
- Delete your_files and directx.exe
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
to decrypt RDM File Extension files try to use this decryptor tool
It is always a good idea to use any reputable anti-malware program after manual removal, to prevent this from happening again.