Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Nemesis Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
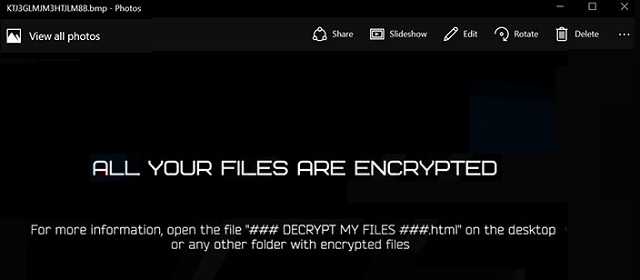
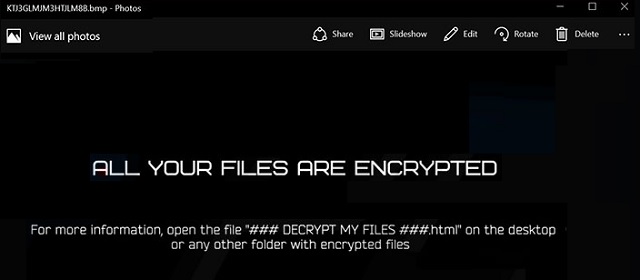
ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED
Nemesis Ransomware
To decrypt your files you need to buy the special software – «Nemesis decryptor»
To recover data, follow the instructions!
You can find out the details/ask questions in the chat:
hxxps://qg6m5wo7h3id55ym.onion.to (not need Tor)
If the resource is not available for a long time, install and use the Tor-browser:
1. Run your Internet-browser
2. Enter or copy the address hxxps://www.torproject.org/download/download-easy.html in the address bar of your browser and press key ENTER
3. On the site will be offered to download the Tor-browser, download and install it. Run.
4. Connect with the button “Connect” (if you use the English version)
5. After connection, the usual Tor-browser window will open
6. Enter or copy the address hxxp://qg6m5wo7h3id55ym.onion in the address bar of Tor-browser and press key ENTER
7. Wait for the site to load
// If you have any problems installing or using, please visit the video tutorial hxxps://www.youtube.com/watch?v=gOgh3ABju6Q
Nemesis is the rather appropriate name of a ransomware infection. If you have the fortune of not coming across such a tool, you’re quite lucky! They are an utter plague. Ransomware programs are quite possibly the worst type of cyber threat out there. Why? Well, because they target your files. They take your data hostage, and demand payment for their release. And, even if you comply to the fullest, chances are, you still lose. The game against a ransomware is a rigged one. The odds are stacked against you from the start. Here’s why. Take the Nemesis tool. It invades your PC, takes over, and encrypts your data. It leaves a ransom note that states if you pay a ransom, you can get your data back. It varies anywhere between $500 and $1500, and you have to pay it in Bitcoin. So, now you have a choice to make. To pay or not to pay? If you don’t pay, you lose your data. But it’s the preferable alternative to paying. Think about it. You don’t only lose money. When you transfer the sum, you provide private details. You leave your personal and financial information, where cyber criminals can find it. And, exploit it for malicious purposes. Not to mention, compliance guarantees you nothing. You can send the money, and still get left sucking your thumb. Do you honestly trust cyber extortionists to keep their word? There are people, who will double-cross you. They will take your money, and give you nothing. Don’t be naive to think they’ll go through with their end of the bargain. They won’t. So, don’t bother trying. Don’t participate in the game, they’ve set up. You WILL lose. Either your money and privacy. Or, your data. And, losing your data is the lesser evil. Wouldn’t you agree?
How did I get infected with?
The Nemesis tool isn’t particularly innovative when it comes to invading your system. It turns to the old but gold methods of invasion. Perhaps, the most common one, is freeware. How come? Well, for reasons unknown, users are NOT attentive during installs. Instead of being extra thorough when allowing freeware into their system, they’re careless. They throw caution to the wind, and rush. They give into naivety. They don’t bother to read the terms and conditions, but say YES to everything. They rely on luck and chance instead of on due diligence. And, that’s a detrimental mistake! As they come to realize after the ransomware takes over. Carelessness leads to infections, while caution keeps them out. Wouldn’t rather spend a few extra moment on research, and make sure all checks out? Be certain that you’re not giving the green light to a cyber threat on accident? Don’t leave your, and your system’s fate, to luck. Always choose caution. Vigilance goes a long way. Remember that next time you’re dealing with freeware. Or, spam email attachments. Or, supposed updates. Like, Java or Adobe Flash Player ones. Even a little extra attention today can save you a ton of issues tomorrow.
Why is Nemesis dangerous?
Nemesis doesn’t much differ from other recently-discovered threats of the ransomware variety. Like, Salsa and Cryptobyte. Or, the Mole and Onion extension tools. Once Nemesis slithers in, it proceeds with a rather familiar scheme. It locks every file you keep on your computer. Your pictures, videos, music, documents. All fall victim under the program’s control. The infection encrypts them via a special algorithm. And, attaches a particular extension at the end of each file to further solidify its keep. Say, you have a photo called ‘me.jpg.’ After the ransomware gets done with it, it turns into: ‘me.jpgid-3057868259_[qg6m5wo7h3id55ym.onion.to].63vc4.’ Once the extension is in place, you can no longer open any of your files. Your data becomes unreachable. You can try to move or rename it, but it doesn’t work. It remains locked. The only way to release it is via a special key. But, to get it, you have to pay up. And, Nemesis makes sure to explain that in the ransom note, it leaves you. You’ll find it as an HTML file on your Desktop, as well as in every affected folder. It’s called ‘### DECRYPT MY FILES ###.html.’ It shares a pretty standard message. Pay us to get the key, or don’t, and lose your data. It seems a straightforward choice but, as was explained, it’s not that simple. Do NOT pay these extortionists a single dime. It’s a tough choice to make, but forsake your files. Discard your data in the name of your privacy. Next time, create back-ups to everything. So, if you have to go through it all again, it won’t be as difficult choice to make.
Nemesis Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Nemesis Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Nemesis encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Nemesis encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.