Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Nemucod Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
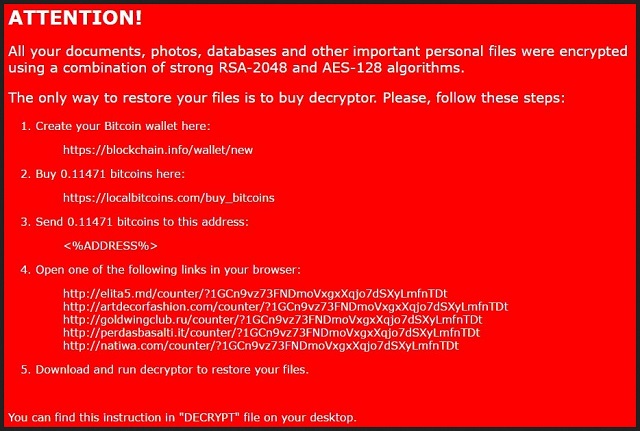
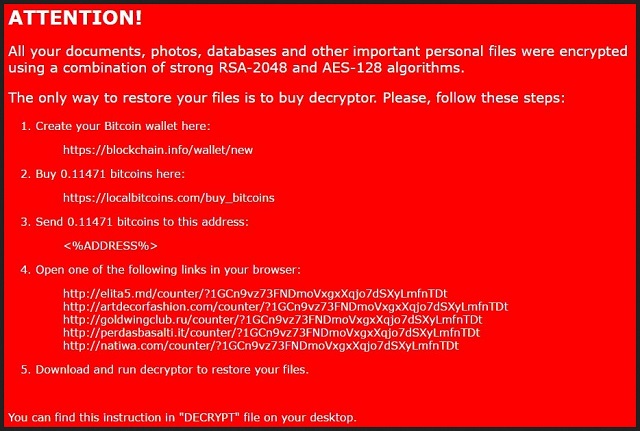
ATTENTION!
All your documents, photos, databases and other important personal files were encrypted using a combination of strong RSA-2048 and AES-128 algorithms.
The only way to restore your files is to buy decryptor. Please, follow these steps:
1. Create your Bitcoin wallet here:
xxxxs://blockchain.info/wallet/new
2. Buy 0.11471 bitcoins here:
https://localbitcoins.com/buy_bitcoins
3. Send 0.11471 bitcoins to this address:
<%ADDRESS%>
4. Open one of the following links in your browser:
xxxx://elita5.md/counter/71GCn9vz73FNDmoVxgxXqjo7dSXyLmfnTDt
xxxx://artdecorfashion.com/counter/71GCn9vz73FNDmoVxgxXqjo7dSXyLmfnTDt
xxxx://goldwingclub.ru/counter/71GCn9vz73FNDmoVxgxXqjo7dSXyLmfnTDt
xxxx://perdasbasalti.it/counter/71GCn9vz73FNDmoVxgxXqjo7dSXyLmfnTDt
xxxx://natiwa.com/counter/71GCn9vz73FNDmoVxgxXqjo7dSXyLmfnTDt
5. Download and run decryptor to restore your files.
You can find this instruction in “DECRYPT” file on your desktop.
One of the worst cyber threats, you can catch, fall under the ransomware umbrella. The category holds the nastiest infections. And, it’s a notoriety well-deserved. These types of programs are an utter plague. They invade your PC, and spread their clutches throughout your system. They’re so prolific that there isn’t a place, left untouched. The Nemucod infection is one such tool, which is extensive in its reach. One day, you turn on your PC, and lo and behold! Each and every file you have is no longer is your control. Your pictures, documents, music, videos, all of it – locked. It got encrypted. Nemucod used special RSA-2048 and AES-128 algorithms for the encryption. And, now it demands a ransom for decryption. If you want your data free of the infection’s keep, you have to pay up. The program requests a payment of 0.11471 BTC. If you’re unfamiliar with Bitcoin currency, that’s about 270.844 USD. It provides you with instructions to follow. You find them in the ransom note on your Desktop. It’s a TXT file with the name Decrypt.txt. You also see it in every folder, containing encrypted files. Do NOT follow these instructions! Compliance takes you down a darker path. It worsens your predicament tenfold. Heed experts’ advice, and do not pay. Do not contact these people. Do nothing! Say goodbye to your files, and move on. Next time, create back-ups. It’s a tough decision to make, but we suggest making it. For your sake.
How did I get infected with?
Nemucod doesn’t appear out of thin air. It’s an infection that needs permission to enter your system. What’s more, it has to ask for it. And, you have to give it. Otherwise, no access. So, the question here is, do you remember giving it? Have you any memory of the exchange, taking place? Odds are, you don’t. And, that’s because you didn’t realize it was happening at the time it did. Confused? It’s rather simple. Let’s elaborate. The ransomware infection doesn’t pop up, and seek access. If it did, you’d reject it. So, it doesn’t choose a straightforward approach at all. Instead, it turns to trickery and deceit, and asks approval in the sneakiest way possible. Freeware, fake system or program updates, corrupted links or sites. There’s a plethora of ways, with which to dupe you. Among the most common, you also find spam email attachments. Try to look at everything you see online with a grain of salt. Due diligence can save you a ton of troubles. Apply extra vigilance every time you install tools or updates. When receiving emails from suspicious senders with attached files, don’t be naive! Naivety, distraction, and haste make for an atrocious combination. Even a little extra attention goes a long way. Always choose caution over carelessness. One helps to keep your system infection-free. The other might lead to you getting stuck with a tool like Nemucod.
Why is Nemucod dangerous?
Here’s why it’s a colossal mistake to pay the ransom to the people behind Nemucod. Let’s examine the situation. What do you have to go on here? A promise that upon payment, all will be well? First off, that’s a lie. And, second, if you pay, you expose yourself. You expose your personal and financial information to cyber criminals. That’s not something, you want. But, we’re getting a bit ahead of ourselves. Let’s start from the top. You see the ransom note, get the instructions, and choose to follow them. The infection promises to send you a decryption key after you transfer the sum. You have no guarantees that will happen. And, all you have to go on is the word of cyber kidnappers. Extortionists, who invaded your PC, and corrupted your data. Can you trust these individuals to keep their end of the bargain? No. The answer is ‘no.’ Even if they were gracious enough to send you a key, what if doesn’t work? And, what do you deem your ‘best-case scenario?’ Pay the ransom, get the right key, decrypt your data, right? Well, what then? The key, you paid for, removes the encryption. Not the infection that did the encrypting. The ransomware remains. Nemucod is free to strike again, and send you back to square one. Only this time, you have less money, and your private life is private no more. That’s because, to go through with the payment process, you provide your information. Your personal and financial information. You leave it right there for the cyber criminals to find. No matter how you look at it, that won’t end well. Time to ask yourself the following. What do you deem more precious: your data or your privacy?
Nemucod Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Nemucod Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Nemucod encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Nemucod encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.