Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Osiris Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
From: “Marina”
To: [REDACTED]
Subject: Emailing: _0828817_36073220
Date: Mon, 05 Dec 2016 15:24:01 +0530
Your message is ready to be sent with the following file or link
attachments:
_0828817_36073220
Note: To protect against computer viruses, e-mail programs may prevent
sending or receiving certain types of file attachments. Check your e-mail
security settings to determine how attachments are handled.
Attachment: _0828817_36073220.xls
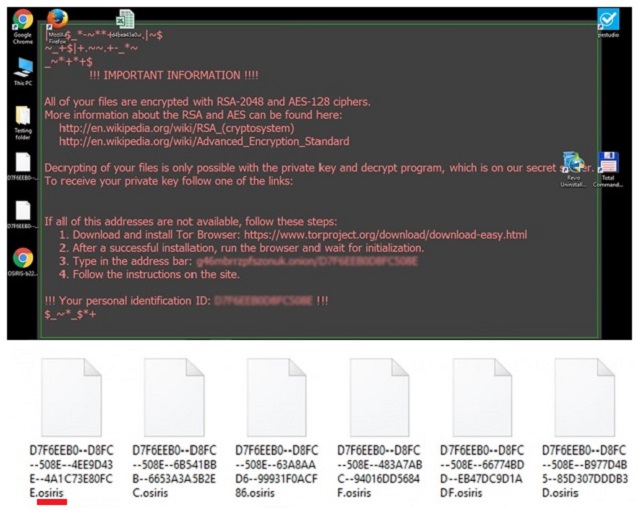
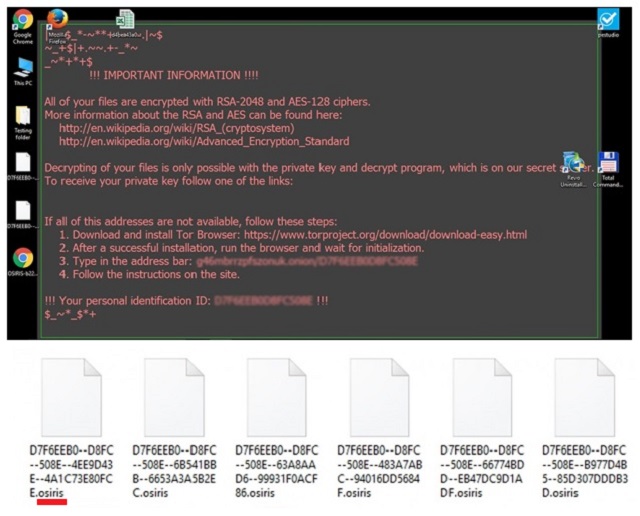
Osiris is the latest member of one particularly harmful malware family. Unfortunately, the Locky Ransomware is back – even stronger than before. Hackers constantly make major improvements of the original Locky virus. This is how we came across Thor, Odin and Aesir. It seems like crooks are running out of Norse Gods to name their ransomware programs after. As you know, Osiris is an Egyptian God of the underworld and the dead. Just like him, the Osiris Ransomware is incredibly dangerous and frightening. You’re now stuck with a file-encrypting infection. There’s a reason why those are considered to be among the worst types of malware out there. Osiris pretty much follows the classic ransomware pattern. For starters, it gets installed in silence. Then the virus performs a thorough scan on your computer. Why? Because Osiris is searching for your private files. Your pictures, music files, documents, videos, etc. Once your data is located, the parasite starts encryption. It locks every single bit of information it has found on your machine. Yes, all your files get encrypted. Ransomware takes down a huge variety of file formats. It will inevitably cause you damage. The Osiris Ransomware uses RSA-2048 and AES-128 ciphers. Thanks to this strong algorithm, it effectively locks your information. Your files actually get renamed. You will notice that a bizarre extension has been added to them behind your back. This is how the infection locks your files. The extension is [8 random symbols]-[4 random symbols]-[8 random symbols]-[12 random symbols].Osiris. Seeing it only means one thing. It means Osiris has successfully encrypted all your precious data. The symbols added by the virus form your ID. Ransomware copies the target files and deletes the originals. What you’re left with are the unreadable copies. You see, your computer won’t be able to recognize the brand new format of your data. Even though your files aren’t deleted, they are being held hostage. And that’s not even the worst part. While encrypting the data, Osiris creates payment instructions. Yes, payment instructions. You read it correctly. You’ll come across OSIRIS.html, OSIRIS_[4_digit_number].html and OSIRIS.bmp. The ransom notes appear in all folders that contain encrypted data. Those are indeed quite a lot of folders. Osiris puts its ransom instructions on your PC desktop as well. Hackers are trying to force these notes on you as much as possible. What is their goal, you may ask? To steal your money. Ransomware is aiming directly at your bank account. One single careless move might cost you a hefty sum of money.
How did I get infected with?
Osiris travels the Web just like all other ransomware-type viruses do. Via deceit. Nobody would download such pests voluntarily. Therefore, hackers need to think of sneaky and stealthy tactics to spread malware online. The most efficient method involves spam messages/emails. This is also the oldest trick in the books. Next time you receive something suspicious in your inbox, delete it. If you underestimate the threat, you may let loose all sorts of infections. Crooks could attach a whole bouquet of viruses to some fake email. Watch out for the messages in your social media too. Another technique includes the help of Trojan horses. Many ransomware infections also get attached to freeware and shareware bundles. In addition, beware of exploit kits, malicious torrents and illegitimate websites. Remember that your caution will pay off in the long run. Never overlook hackers’ creativity because the Web is infested with malware. Having to uninstall a virus is more of a hassle than preventing infiltration.
Why is Osiris dangerous?
The Osiris Virus locks your private information. It turns your files into inaccessible gibberish. As we mentioned already, seeing the .Osiris extension means it’s game over. Ransomware is, without a doubt, an infection you wouldn’t want to deal with. Make sure you tackle this intruder as soon as possible. Also, make sure you never have to uninstall ransomware ever again. Having this experience once is more than enough. In the future, keep backups of your important data so you could restore it yourself. Osiris promises to free your data in exchange for some money. It usually demands between 1 and 4 Bitcoins. That equals a sum between 758 and over 3000 USD. Crooks are supposed to provide a decryptor once you pay. It goes without saying that’s a scam. Are you willing to let hackers involve you in their nasty attempt for a fraud? They will not deliver the decryption key you need. On the other hand, they will use your money to develop more and more infections. To delete Osiris manually, please follow our detailed removal guide down below.
Osiris Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Osiris Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Osiris encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Osiris encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.