Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove CryptoHost Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
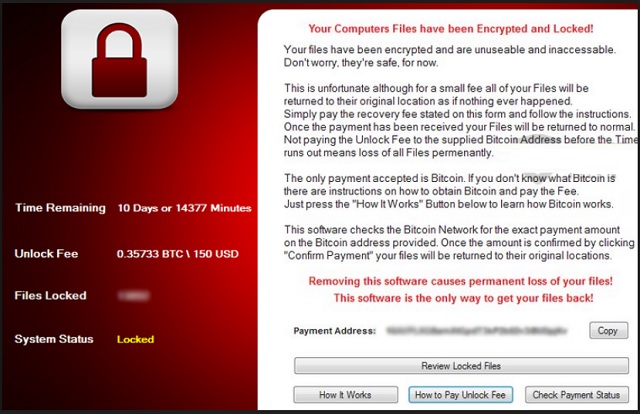
You Computers Files have been Encrypted and Locked!
Your files have been encrypted and are unusable and inaccessible.
Don’t worry, they’re safe, for now.
This is unfortunate although for a small fee all of your Files will be
returned to their original location as if nothing happened.
Simply pay the recovery fee stated on this form and follow the instructions.
Once the payment has been received your Files will be returned to normal.
Not paying the Unlock Fee to the supplied Bitcoin Address before the Timer
runs out means loss of all Files permanently.
The only payment accepted is Bitcoin. If you don’t know what Bitcoin is
there are instructions on how to obtain Bitcoin and pay the Fee.
Just press the “How It Works” Button below to learn how Bitcoin works.
This software checks the Bitcoin Network for the exact payment amount
on the Bitcoin address provided. Once the amount is confirmed by clicking
“Confirm Payment” your files will be returned to their original locations.
Removing this software causes permanent loss of your files!
This software is the only way to get your files back!
CryptoHost is a new ransomware menace, plaguing Internet users. If you come across the CryptoHost name, you’re one of the unlucky ones, who’ve managed to catch the dreaded infection. And, you better brace yourself for trouble as you’re in for a pretty bad time. Ransomware is arguably the worst cyber threat you could ever get stuck with because apart from the usual grievances – causing you a ton of issues and jeopardizing your privacy, it’s also programmed to target your data specifically. Yes, the tool is designed to take hold of every single file you keep on your computer – JPEG, JPG, PNG, GIF, AVI, MOV, WMV, MP4, PDF, DOCX, DOC, ZIP, etc. You get the point. CryptoHost kidnaps all of your pictures, videos, music, documents, everything, and holds it hostage until you meet its demands. Once the tool slithers into your system, it begins a sort of encryption process, which, once complete, renders your files inaccessible. You won’t be able to open them and, as you’ve probably guessed it, the only way to free them from CryptoHost’s grasp would be to go through with its requirements. The tool displays its wishes once the ‘encryption’ is done, and they involve a monetary payment. We say ‘encryption’ because, despite the tool claiming that it encrypts your data, in actuality, it copies it to a password protected RAR file, and then deletes the original version. So, the needed decryption key for your files’ freedom is rather a password. And, all that’s required of you is to comply. If you pay the requested ransom, you receive the key, decrypt your data, and all is well in the world. But is it, though? Think about it. What are your guarantees that these malicious, unknown individuals behind the CryptoHost ransomware will keep their end of the bargain? None! You have no guarantees. After all, we’re talking about wicked people, who invaded your PC and encrypted your files. Do you honestly expect them to keep their promises? Here’s a hint: don’t! They’re far less than trustworthy. There are several possible scenarios of how your situation can go down, and they all end badly for you. So, don’t take any chances! Protect yourself, and your system from future damage, by discarding your data. Yes, it’s a difficult decision to make, but it’s the right one. Let go of your files for the sake of your privacy. They can be replaced. Can you say the same about your personal and financial information?
How did I get infected with?
CryptoHost doesn’t just show up on your computer. Oh, no. If you are to get stuck with the dreaded tool, you have to approve its installment. And, judging from your current predicament, you did. It may seem hard to believe, but the ransomware asked whether you agree to install it and, evidently, you did. Otherwise, you wouldn’t be in this mess. And, we’re betting you probably don’t even remember consenting to its install, and are most likely shaking your head in denial right now. After all, how can you agree to install a tool and not even know about it? Well, unfortunately, you did. And, it’s pretty straightforward. You were duped. Ransomware infections are cunning and positively masterful in the art of deceit. They use slyness and subtlety to trick you into permitting them in while keeping you oblivious to it. More often than not, they succeed with the help of the old but gold means of infiltration. That includes hiding behind corrupted sites or links, hitching a ride with spam email attachments or freeware or pretending to be an update. Oh, yes. You might be positively convinced that you’re updating your Adobe Flash Player or Java, but you’d be wrong. In actuality, you’ll be giving the green light to a dangerous cyber threat. And, here’s where your caution comes in quite handy. Be more attentive! Always do your due diligence and be extra thorough and vigilant. Don’t give into gullibility, haste, and distraction for you WILL regret it. Infections, including CryptoHost, prey on carelessness. So, by throwing caution the wind, you significantly increase your chances of catching an infection. Bear that in mind next time you’re installing a tool or an update.
Why is CryptoHost dangerous?
Once it’s in, the ransomware wastes no time and quickly goes to work and begins the encryption process. CryptoHost targets over thirty-four file extensions, and locks them in your “C:\Users\[username]\AppData\Roaming” folder for safe keeping. It copies your original files to an RAR archive, which is created by combining a custom SHA1 hash and your account name. And, naturally, it’s password-protected. Once the RAR is created and sealed, your original files are destroyed. Now, you need to understand that CryptoHost is not your typical ransomware. It doesn’t employ an encryption algorithm to lock your data but goes through the copy-and-destroy process instead. And, it doesn’t use a C&C server, but rather just checks at various intervals if you’ve completed the ransom payment. That’s not the usual tactics. What is, by far, the very definition of the word is the demands. Like most, if not all, ransomware, CryptoHost asks for money. It displays up to three different messages, which state the same thing – give me money. The requested sum is 0.33 Bitcoin, which is approximately $140. Even if the amount seems small to you, and you’re willing to pay just to make sure you gain back your files, DON’T! It’s not worth paying even one penny! Do you know why? As was already mentioned, you have ZERO guarantees that completing the payment will work. What if the kidnappers don’t give you a decryption key? What if they give you one, which doesn’t work? And, what if it does work? What’s stopping them from kicking the ransomware’s programming right back in the next day and getting you back to square one? Nothing! These are malicious people with malevolent intentions, who do NOT have your best interest in mind. They seek to exploit you for money, and couldn’t care less if you retrieve or lose your data. Ransomware is unpredictable and highly unreliable. Don’t place your trust in strangers with agendas, and don’t let them have their way. If you pay up, you risk strangers having access to your personal and financial details. Do you think that will end well for you? Hardly. So, don’t pay! It should be noted that there is, however, a glimmer of hope for retrieving your files via other means. Experts have come out and stated that there IS indeed a way to find out what the password is, and recover your data without paying the ransom. It’s up to you to decide whether you’re willing to take a risk by paying or by trusting some other method of recovery, or just to cut your losses and forsake your files. Figure out your priorities and act accordingly.
CryptoHost Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover CryptoHost Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with CryptoHost encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate CryptoHost encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.