Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Fenrir Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
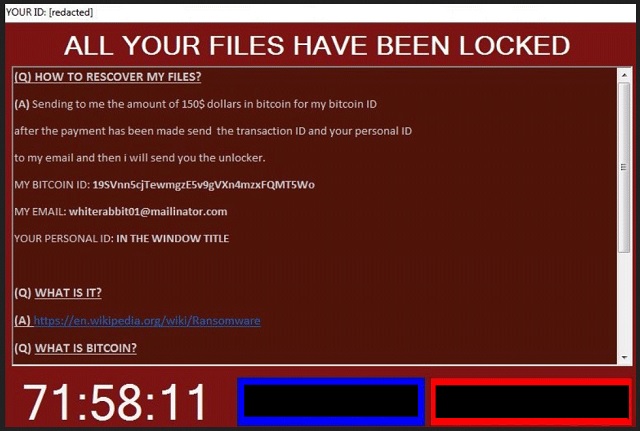
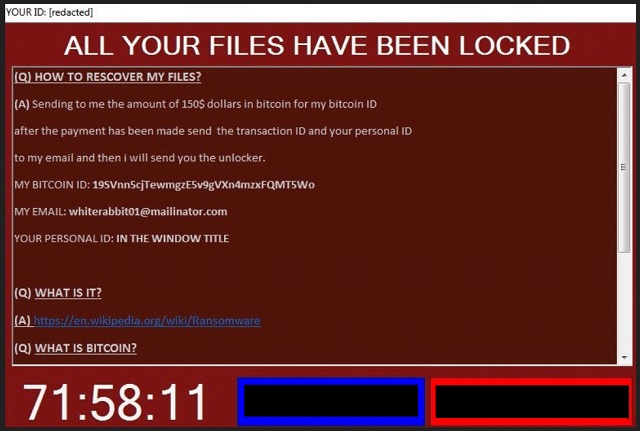
ALL YOUR FILES HAVE BEEN LOCKED
(Q) HOW TO RESCOVER MY FILES?
(A) Sending to me the amount of 150$ dollars in bitcoin for my bitcoin ID after the payment has been made send the transaction ID and your personal ID to my email and then i will send you the unlocker.
MY BITCOIN ID: 19SVnn5cjTewmgzE5v9gVXn4mzxFQMT5Wo
MY EMAIL: whiterabbit01@mailinator.com
YOUR PERSONAL ID: IN THE WINDOW TITLE
(Q) WHAT IS IT?
(A) https://en.wikipedia.org/wiki/Ransomware
(Q) WHAT IS BITCOIN?
(A) https://en.wikipedia.org/wiki/Bitcoin
(Q) WHERE TO BUY BITCOIN?
(A) https://localbitcoins.com/
Yet again, we come across a ransomware that was inspired by Norse mythology. Infections called Locky, Thor and Odin gained immense popularity in 2016. So far it seems the Fenrir Ransomware is about to follow their footsteps. This program uses the AES encrypting algorithm to lock your private files. As you could imagine, nobody wants to have their personal data encrypted. The ransomware goes after your files in silence and encrypts them out of the blue. Many PC users would panic seeing that their data gets suddenly locked. Anything that ransomware modifies becomes unreadable. Being a typical infection, Fenrir doesn’t deviate from the classic rules. It gets activated behind you back and firstly scans your PC. By scanning your machine, Fenrir Ransomware locates all its target files. That includes your photos, music files, your documents, your videos. Every single piece of information stored on board falls victim to the parasite. Now that this pest has successfully found your files, it starts encrypting them. That’s your chance to spot the parasite and stop the encryption process. While the virus is locking your data, your computer underperforms. It might begin crashing or freezing and is slowed to a crawl. Pay attention to the PC speed in order to spot the intruder before it’s too late. However, ransomware usually manages to complete the encrypting process undisturbed. What’s rather curious about this program is that it adds a unique file extension. Unlike most ransomware infections, Fenrir uses the IP of your computer to create an extension. That is how you receive a tailored 10-character file appendix which appears at the end of your files. As you could imagine, seeing the extension means it’s game over. There’s no more using your data, there’s no more opening your files. The ransomware is messing with your favorite, precious data. Hackers hold it hostage. Can you already see the scam? There is only one reason why crooks would encrypt your files. You see, they assume you want your files back. Conveniently enough, the Fenrir Ransomware also drops detailed payment instructions (Ransom.rtf). This is the part where hackers try to convince you to buy a special decryptor. The problem is that you’d be making a deal with greedy cyber criminals why have no intentions to free your files. Their only interest is to steal your Bitcoins.
How did I get infected with?
This program usually travels the Web pretending to be an Adobe Acrobat Reader. Next time you download any software updates, watch out for potential parasites. You might accidentally agree to give green light to all sorts of viruses. In this case, you have nobody to blame but yourself. Malware uses the old but gold distribution techniques. It relies on your distraction online and only needs a single moment of haste. Another famous infiltration technique involves fake messages or email-attachments. If you receive some emails you don’t trust, restrain yourself from clicking them open. Those could turn out to be filled with parasites and cause you cyber trouble. In addition, many infections use exploit kits and freeware bundles to get spread online. It is your job to be constantly attentive and cautious so your machine remains virus-free. Be careful what you download. Ransomware could use some help from a Trojan horse as well. Hence, you should make a thorough check of your computer. Make sure the Fenrir Ransomware has no company on your device.
Why is Fenrir dangerous?
The Fenrir Ransomware locks all your files. It uses a complicated cipher and turns your data into unusable gibberish. Unless you have backup copies of your information, these modifications might get you to panic. Note that giving into your anxiety is the worst move you could make right now. Hackers are stubbornly trying to trick you into paying a ransom. As mentioned already, Fenrir Ransomware creates ransom notes which inform you on the situation. Just to make you feel even more uneasy, the parasite adds a timer. You are supposed to make the payment and contact hackers at whiterabbit01@mailinator.com. Instead of giving crooks your money, stay away from this email address. Cyber criminals demand 150 USD in Bitcoin so you could receive a decryption key. However, you may receive absolutely nothing. You have no reason whatsoever to trust hackers nor to give them your Bitcoins. Even though you’re supposed to regain access to your encrypted data, there is no guarantee that you will. On the other hand, you could be more than positive hackers will use your money to develop more and more infections. Don’t let them involve you in this aggravating fraud. To delete the ransomware manually, please follow our removal guide down below.
Fenrir Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Fenrir Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Fenrir encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Fenrir encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.