Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Imsorry Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
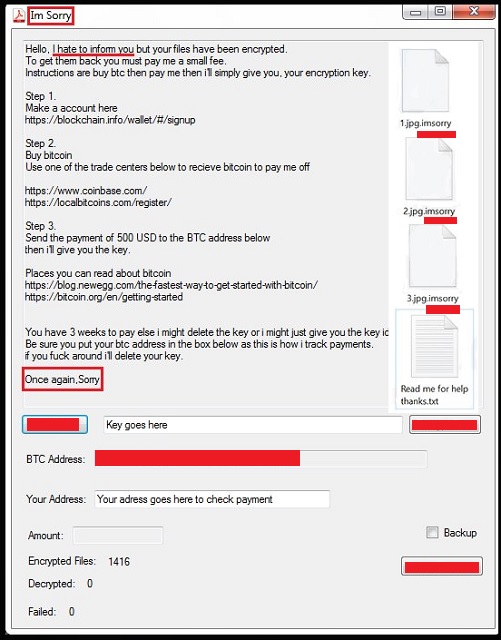
Hello, I hate to inform you but your files have been encrypted.
To get them back you must pay me a small fee.
Instructions are buy btc then pay me then i’ll simply give you, your encryption key.
Step 1.
Make a account here
hxxps://blockchain.info/wallet/#/signup
Step 2.
Buy bitcoin
Use one of the trade centers below to recieve bitcoin to pay me off
hxxps://www.coinbase.com/
hxxps://localbitcoins.com/register/
Step 3.
Send the payment of 500 USD to the BTC address below
then i’ll give you the key.
Places you can read about bitcoin
hxxps://blog.newegg.com/the-fastest-way-to-get-started-with-bitcoin/
hxxps://bitcoin.org/en/getting-started
You have 3 weeks to pay else i might delete the key or i might just give you the key idk
Be sure you put your btc address in the box below as this is how i track payments.
if you f*** around i’ll delete your key.
Once again,Sorry.
What if, you come to find your data encrypted, one day? You turn on your PC, and get greeted with a message saying that your files are no longer yours to control. But, what if the infection is really cordial about the whole situation? Does that make a difference? Probably not, but the Imsorry ransomware, still tries. You’d think the cyber criminals behind it are pretty conflicted about their actions. The message, you see, after they strike begins with “Hello, I hate to inform you but your files have been encrypted.” And, it keeps that polite tone throughout the whole note. By the end of it, it makes a rapid shift with the words “if you f*** around i’ll delete your key.” But then, as if they felt remorseful, it ends with “Once again,Sorry.” Conflicted cyber criminals aside, you’re in grave trouble. Once the Imsorry infection invades, it takes over. It locks every file you keep on your PC with a special encryption. Then, demands payment for their release. If you’re too see your files again, you must pay 500 USD to the BTC address, provided. If you fail to do so, you lose your data. The cyber kidnappers delete them. Put like that, it seems a simple enough choice. Transfer 500 USD for the return of every picture, video, document, et cetera. But life is rarely that simple. Neither is the conundrum, you face with Imsorry. Above all else, you must realize, ransomware tools are not reliable. They are not trustworthy. They are governed by malicious cyber criminals with wicked agendas. Despite the cordial front, so is the Imsorry threat, and the people behind it. Do not fall for their fake promises. They fall through. As harsh as it may seem, do not pay. Say goodbye to your files, and move on. Next time, make backups to avoid getting faced with such a difficult decision.
How did I get infected with?
The Imsorry used the old but gold means of invasion to infiltrate your PC. The most common one is, by far, freeware. That’s because it provides the easiest access. For reasons unknown, users are quite careless when installing freeware. They don’t bother to read the terms and conditions. But opt to head straight for the YES at the bottom. That’s a colossal mistake, you’ll come to regret. Infections lurk behind freeeware. That’s why it’s crucial to always know what you agree to install alongside it. Vigilance can save you a ton of troubles. Don’t discard its importance. Always take the time to be thorough, and do your due diligence. Sometimes even a little extra attention can save you a plethora of problems. Distraction, naivety, and haste, however, have a tendency of inviting them in.
Why is Imsorry dangerous?
Do not believe a single promise the Imsorry tool makes! It’s all lies. Look past the sugary layers of deception, and you’ll see. Nothing a ransomware claims can be counted on. Question everything. And, above all, do not pay these people! They are extortionist, who will say and do anything to get your money. These people created a malicious cyber infection, and unleashed it onto web users. They invaded your system, and encrypted your data. Then, were brazen enough to demand payment for their release. Even if it were a ransom of a single dollar, you still shouldn’t pay. And, that’s because it’s not about the money. It’s about so much more than that. Let’s play it out. Say, you transfer the ransom to these people. Then, what? You wait for them to keep their word, and send you the promised decryption key. But, will they? They already got your money. Why would they bother with you any more? They can choose to double-cross you, and leave you with nothing. And, even if they send you a decryption key, don’t rejoice just yet. It can be the wrong one, and not work. And, what’s your best-case scenario? You pay up, get the right key, apply it, decrypt your data. But decryption doesn’t solve your problem. You still have an infection on your computer! The decryption key, you pay for, removes the encryption. Not the ransomware itself. It remains, lurking somewhere on your computer, ready to strike again at any moment. Then, you’re back to square one. Only tis time, you have less money, and an exposed privacy. Oh, yes. By paying the ransom, you provide private information. You leave your personal and financial details for the cyber criminals to find and exploit. Don’t get fooled by their cordial facade. They will do it. So, the question is, will you leave your privacy in their hands? What are your files worth to you? Are you willing to pay 500 dollars and your private life for the mere prospect of getting them back? Think long and hard before you answer. There’s a lot resting on your decision.
Imsorry Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Imsorry Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Imsorry encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Imsorry encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.