Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Lambda Locker Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
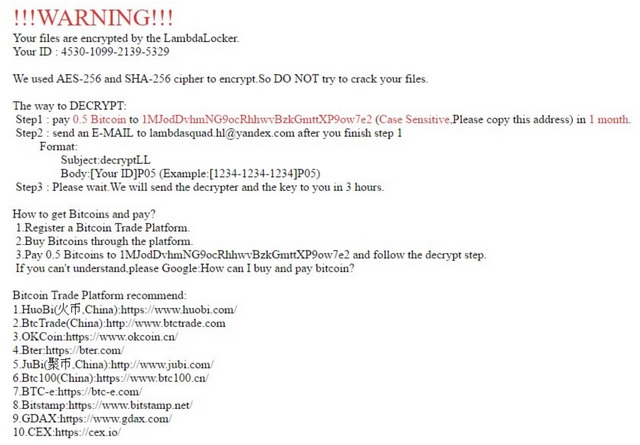
!!!WARNING!!!
Your files are encrypted by the LambdaLocker.
Your ID: 4530-1xxx-2xxx-5xxx
We used AES-256 and SHA-256 cipher to encrypt. So DO NOT try to crack your files.
The way to DECRYPT:
Step1: pay 0.5 Bitcoin to 1MJod*** (Case Sensitive, Please copy this address) in 1 month.
Step2: send an E-MAIL to lambdasquad.hl@yandex.com after you finish step 1
Format:
Subject: decryptLL
Body: [Your ID]P05 (Example:[1234-1234-1234]P05)
Step3: Please wait. We will send the decrypter and the key to you in 3 hours.
How to get Bitcoins and pay?
1. Register a Bitcoin Trade Platform.
2. Buy Bitcoins through the platform.
3. Pay 0.5 Bitcoins to 1MJodDvhmNG9ocRhhwvBzkGmttXP9ow7e2 and follow the decrypt step.
If you can’t understand, please Google: How can I buy and pay bitcoin?
Bitcoin Trade Platform recommend:
1. HuoBi (火币,China): https://www.huobi.com/
2. BtcTrade (China): http://www.btctrade.com
3. OKCoin: https://www.okcoin.cn/
4. Bter: https://bter.com/
5. JuBi (聚币,China): http://www.jubi.com/
6. Btc100 (China): https://www.btc100.cn/
7. BTC-e: https://btc-e.com/
8. Bitstamp: https://www.bitstamp.net/
9. GDAX: https://www.gdax.com/
10. CEX: https://cex.io/
Or you can use others.
If you have any questions, please e-mail lambdasquad.hl@yandex.com.
There’s a new ransomware tool, roaming the web and plaguing users. It goes by the name Lambda Locker and, like all others of its kind, it’s a menace. The tool exploits your carelessness to slither into your system. And, once it’s in, corrupts it. The infection uses asymmetrical AES and RSA algorithms to encrypt all your data. Yes, all of it. Your documents, pictures, videos, music, etc. Everything falls under the Lambda Locker’s control. The tool places everything you keep on your PC under lock down. You cannot open it or access it in any way. Not unless you apply the right decryption key to free it. But that key costs you. This is where the ‘ransom’ part of the ransomware kicks in. After it encrypts your data, it demands you pay up for its release. Do NOT pay the ransom! Do NOT follow the requests of cyber extortionists! If you do, you only bury yourself in deeper troubles. Cut your losses. Say goodbye to your files to protect yourself from an even bigger mess. It may seem like an impossible choice to make but it truly is the best course of action to take. Discard your data. It’s the lesser evil.
How did I get infected with?
The Lambda Locker ransomware used deception and finesse to invade your system. The tool turned to the old but gold methods of infiltration, and snuck in undetected. That’s why your suddenly locked data took you by surprise. You had no idea of the infection’s presence. And, that was no accident. This type of programs use slyness to slither in under the radar. And, make sure you’re oblivious to their existence until they act up. But back to their invasion methods. How do you suppose they manage to slip past you? Well, more often than not, they lurk behind freeware. It’s one of the easiest ways in since most users don’t even read the terms and conditions. They just agree to everything, and end up with “surprises.” Don’t be one of those users! Go the opposite route! Do your due diligence. Always take the time to read what you get asked to agree to. Don’t rush and give into distraction. Carelessness tends to lead one way – to infections. If you wish to avoid them, turn to vigilance. Other sneaky means of infiltration involve bogus updates, corrupted links, and spam email attachments.
Why is Lambda Locker dangerous?
If you’re careless enough for Lambda Locker to slither past you, brace yourself. You’re about to get thrown into a whirl of unpleasantness. As soon as the infection invades your PC, it proceeds with encryption. It doesn’t waste time but locks every file you have. One day, you find all your data renamed with a peculiar extension. The tool placed it at the end of each of your files to solidify its grip over them. For example, if you have a picture called ‘me.jpg,’ you’ll find it as ‘me.jpg.lambda_l0cked.’ Once your files get renamed, that’s it. They’re no longer under your control. They’re under the control of Lambda Locker. And, it will remain that way until you pay the ransom, which the tool requests. After the encryption’s done, it leaves you specific instructions to follow. You’ll find them as an HTML file on your Desktop, and each infected folder. It’s hard to miss a file called READ_IT.hTmL. The infection asks for payment of 0.5 Bitcoin. It’s no small sum since 1 Bitcoin is between 500-600 US Dollars. But, here’s the thing. Even if the request were for one single dollar, payment is still ill-advised. Do NOT contact these people in any way, and do NOT give them money! If you transfer the sum, you open a door you can’t close. You give them access to your personal and financial information. And, is that something you’re willing to do? Provide cyber extortionists with access to your private life? Are your pictures really worth that risk? Accept the loss of your data, so you don’t lose your privacy. Besides, these are so many ways the exchange with the kidnappers can go wrong. They can and, likely, will double-cross you. They can send you the wrong decryption key or no key at all. And, even if they send you the right one, you’re still screwed. Why? Well, the key only removes the encryption, not the ransomware. So, the infection remains somewhere on your PC, ready to strike again. Either way you look at it, compliance leads to trouble. Don’t comply. Forsake your files.
Lambda Locker Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Lambda Locker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Lambda Locker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Lambda Locker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.