Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Razy Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
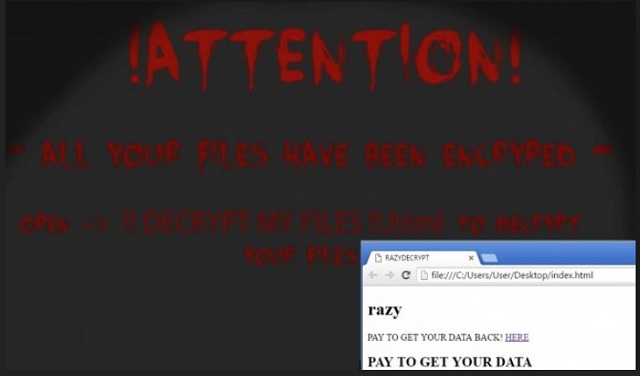
!ATTENTION!
ALL YOUR FILES HAVE BEEN ENCRYPTED –
OPEN -> ll DECRYPT MY FILES ll html TO DECRYPT
YOUR FILES
Razy is the name of a new player in the cyber infection game. It’s a relatively new ransomware infection. But it’s plaguing users in the same old manner. Ransomware tools are arguably the worst type of cyber threat out there. And, don’t think the title’s given lightly. They’ve earned it. These applications slither into your system undetected, and wreak chaos. They target the data you keep on your computer. All of it! Every picture, document, video, song, etc. After the infection sneaks in, it goes to work. Once it gains access to your PC, it locks your files. It encrypts them with the help of an added extension (.razy). And, all of a sudden, your data is no longer accessible. It’s beyond your reach. And, the ransomware has complete control. And, you better be sure it takes advantage of that. It’s designed that way. Once the ransomware encrypts everything, it offers you a way out. Supposedly, if you pay a ransom for the release of your data, you’ll get it back. After you complete the payment, the people behind the infection, send you a decryption key. You apply it, and voila! Your files are no longer locked. But, here’s the thing. That’s a hypothetical scenario with way too many variables. So much can go wrong. But, above all else, ask yourself this. Can you trust strangers, who unleashed a dangerous cyber threat onto web users, to keep their promise? Don’t be naive. Even if you ignore all else (and there’s a lot), there’s no way past the unreliability of these people. Instead of burying your head in the sand, and praying for the best possible outcome, act in your best interest! Don’t pay the ransom! Don’t contact the kidnappers! Just say goodbye to your data. Don’t be a puppet to a malicious program. That’s how ransomware tools tend to work. But not Razy. It’s an entirely different kind of ransomware. One, might even say, a worse one. Why? Well, because once it’s done with the files’ encryption, it doesn’t ask for money on their return. It just keeps them, and offers no way for decryption. And, that’s it. There’s no way you get your files back.
How did I get infected with?
Razy invades your PC the same way most cyber threats do. It preys on your carelessness, and gets you to install it yourself. Let’s elaborate. Ransomware tools sneak in with the assistance of the old but gold ways of infiltration. More often than not, they hide behind freeware as it’s possibly the easiest entry point. That’s because users, in general, are not as careful as they should be during its install. They don’t pay attention to the terms and conditions, but agree to all of them. That’s a mistake. If you automatically say ‘Yes’ to everything, don’t be surprised to find malware on your PC. But that’s not the only method, ransomware uses. Such tools can also pretend to be fake updates. Like, Adobe Flash Player or Java. Or, hitch a ride with spam email attachments, or corrupted links. Did you manage to spot the pattern? As was already stated, infections prey on carelessness. As does ransomware. As does Razy. If you wish to increase your chances of having an infection-free PC, be more careful. Attention and vigilance are crucial. Be more thorough, and don’t underestimate the importance of doing your due diligence.
Why is Razy dangerous?
Razy follows the programming of all ransomware tools. It works in pretty much the same manner, with a few major differences. It uses an asymmetric encryption algorithm to lock your data. It sticks the .razy extension at the end of each of your pictures, songs, videos, etc. And, thus, ‘seals the deal’ and renders them inaccessible. Once the extension gets added, there’s no opening these files. You can try to rename or move them, but it’s futile. The only way to release them from Razy’s captivity is with the decryption key. But more on that later. When the encryption is complete, it creates three files. They’re “css.vbs,” “index.html,” and “razy.jpg.” They’re placed on your desktop, and give you instructions and clarification. But, here’s the thing. Most ransomware shower you with details. They explain the encryption, your situation, the ransom request, payment method, everything. They provide you with all the information you might need. But not Razy. It’s as if it gives you a CliffsNotes version. But, here’s the stranger part of it all. It’s like Razy doesn’t even want your money. And, that’s peculiar, to say the least. Ransomware usually demands between 0.5 and 1.5 Bitcoin, and 1 Bitcoin is about $600. But if you click Razy’s ‘PAY HERE’ link in the ransom note, it takes you nowhere. So, if it’s not money, what does this ransomware want? Well, some online users claim that Razy wasn’t created for profit. But, instead, for educational purposes. To educate people on the dangers of getting stuck with ransomware. That is if you believe the Twitter account of one of its developers. Educational or not, it’s an infection. It’s a ransomware tool. Remove it from your PC ASAP.
Razy Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Razy Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Razy encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Razy encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.