Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Resurrection Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
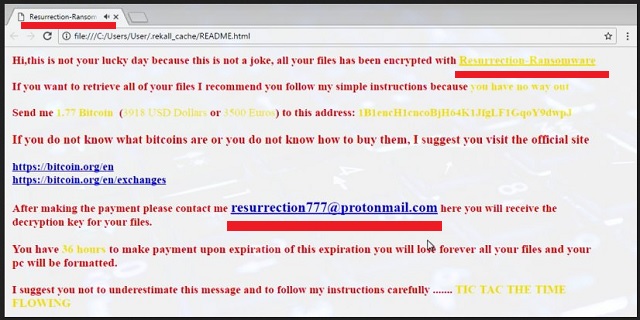
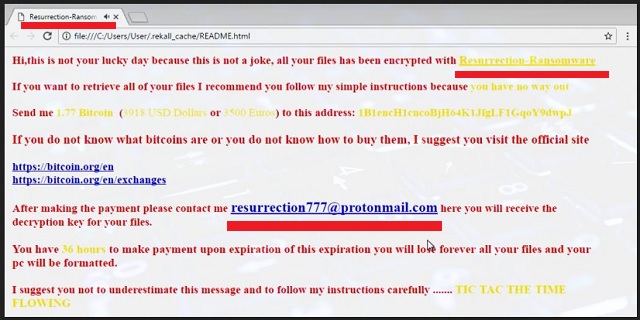
Hi, this is not your luck day because this is not a joke, all your files has been encrypted with Resurrection-Ransomware
If you waut to retrieve all of your files I recommend you follow my simple instructions because you have no way out
Send me 1.77 Bitcoin (3918 USD Dollars or 3500 Euros) to this address: 1B1encH1cncoBjH64K1JfgLF1GqoY9dwpJ
If you do not know what bitcoins are or you do not know how to buy them, I suggest you visit the official site
https://bitcoin.org/en
https://bitcoin.org/en/exclianges
After making the payment please contact me resurrection777@protonmail.com here you will receive the decryption key for your files.
You have to make payment upon expiration of this expiration you will lose forever all your files and your pc will be formatted.
I suggest you not to underestimate this message and to follow my instructions carefully……. TIC TAC THE TIME FLOWING
It’s safe to say this program was inspired by the HiddenTear ransomware project. The Internet is pretty much full of vicious file-encrypting parasites so Resurrection Ransomware is just one of many. This pest uses the AES-256 encrypting algorithm to cause you trouble. Unfortunately, it succeeds. You’ll quickly see for yourself why ransomware is so immensely dreaded. These parasites have a totally well-deserved malicious glory. Being a classic member of its malware family, Resurrection Ransomware follows the classic pattern. Its shenanigans start with a thorough scan of your PC. By scanning your computer, this nuisance locates its target files. In other words, the virus finds all files that it is about to encrypt. That includes pictures, videos, music, MS Office documents. A huge variety of formats falls victim to the parasite’s trickery. It goes without saying that seeing all your files get encrypted out of the blue is nerve-wracking. And that is exactly what hackers want. You’ve been involved in a pesky attempt for a cyber scam so be careful. Giving into your panic could cost you a hefty sum of money. 4635 dollars, to be more specific. The Resurrection Ransomware starts locking your files as soon as it locates them. As mentioned, this program uses a strong cipher and completely denies you access to your precious data. It changes the original format of your information. You’ll notice a brand new .resurrection file extension added to your data. Did you agree to have your data modified? No? We have never come across a ransomware that takes care of the victim’s preferences. The Resurrection Ransomware effectively locks every single bit of information you have. It also drops README.html files in all folders that contain encrypted data. This is where it gets interesting. According to these ransom messages, you’re supposed to pay 1.77 Bitcoins to receive a decryption key. That equals 4635 USD at the moment which is a lot of money to open your own files. Ransomware is nothing but a tricky, deceptive infection. It attempts to convince you that you must make the payment ASAP. One curious detail is the music that this .html file plays. It reminds a lot of the Harry Potter theme song and adds up to the dramatic effect ransomware aims for. However, you should never allow hackers to scam you. Ignore their sound effects, empty promises and bogus threats. Get rid of the ransomware.
How did I get infected with?
Ransomware usually gets spread online via bogus email-attachments and messages. This is also the oldest malware infiltration technique online. Hackers don’t seem to be giving it up anytime soon, though. Next time you receive something unreliable in your inbox, delete it. Clicking open a fake email might let loose a whole bouquet of malicious infections. Instead of compromising your own security, make sure you prevent installation. Always watch out for fake emails even though crooks make an effort to present them as legitimate. For example, they often attach logos and symbols to a corrupted and utterly fake email-attachment. It is your responsibility and yours only to delete it on time thus protecting your PC from malware. Other popular tricks involve torrents, third-party pop-ups, unverified program updates and illegitimate websites. It’s clear that infections have various distribution methods to choose from. Watch out for potential viruses and don’t overlook any cyber threat. Also, we’d recommend that you check out your computer for more infections. The ransomware may have used some help from a Trojan. Now that you’ve seen just how troublesome these parasites are, be careful when surfing the Web.
Why is Resurrection dangerous?
The Resurrection Ransomware provides you an email address (resurrection777@protonmail.com). On theory, you have to contact its developers and make the payment. On practice, though, this is how you get scammed. Instead of falling straight into hackers’ trap, ignore their irritating ransom notes. It is key for your further safety that you keep your Bitcoins. Why give your money away to greedy cyber criminals? After all, those are the very people who locked your personal files in the first place. Hackers shouldn’t be rewarded for messing with your data. Do not become a sponsor of their malicious business and do not believe their promises. You may not get a decryptor but you will certainly lose your Bitcoins. To make sure hackers don’t succeed in scamming you, uninstall their ransomware. You have absolutely no reason to negotiate with hackers nor follow their instructions. To delete the virus manually, please follow our detailed removal guide down below.
Resurrection Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Resurrection Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Resurrection encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Resurrection encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.