Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Samsam Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
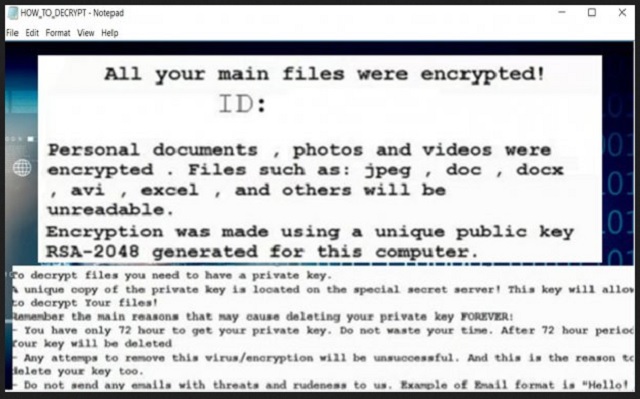
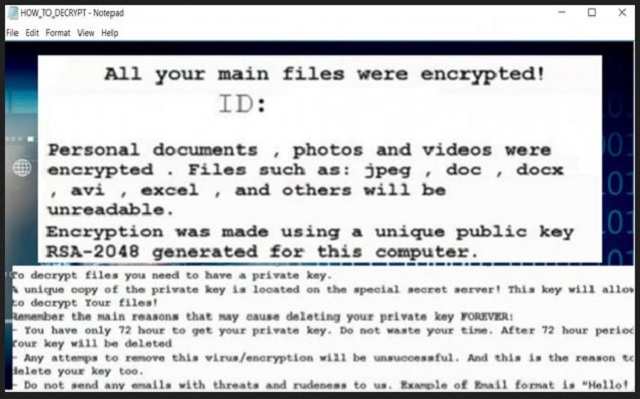
#What happened to your files?
All of your important files were encrypted with RSA-2048, RSA-2048 is a powerful cryptography algorithm. For more information you can use Wikipedia.
Attention. Don’t rename or edit encrypted files because it will be impossible to decrypt your files.
#How to recover files?
RSA is a asymmetric cryptography algorithm, You need two key
1-Public key: you need it from encryption
2-Private key: you need it for decryption
So you need Private key to recover your files. It’s not possible to recover your files without private key.
#How to get private key?
You can receive your Private Key in 3 easy steps:
Step1: You must send us One Bitcoin for each affected PC to receive Private Key.
Step 2: After you send us one Bitcoin, Leave a comment on our blog with these detail: Your Bitcoin transaction reference + Your computer name.
#What is Bitcoin?
Bitcoin is an innovative payment network and a new kind of money. You can create a Bitcoin account at hxxp://blockchain.info and deposit money into your account and then send us.
#How to buy Bitcoin?
There are many way ti buy Bitcoin and deposit it into your account, You can buy it with WesternUnion, Bank Wire, International Bank transfer, Cash deposit and etc. If you want to pay with your Bussiness bank account you should create a business account in exchangers they don’t accept payment from third party.
#How to find the Bitcoin transaction reference?
Login into your blockchain account -> go to “My transactions” tab -> Click on your transaction -> In “Transaction Summary” page, You will find a “hash” with 64 characters long. Send us this hash with your comment on our blog + you computer name.
Samsam belongs to the ransomware family. And, in case you were wondering, that’s not good. Ransomware applications are nothing but trouble. They invade your computer, and throw you into a world of trouble. Samsam is no exception. Once it sneaks into your system, it wastes no time. It gets down to business. The tool encrypts everything you keep on your computer. Every single file gets locked. Pictures, videos, music, documents. Nothing escapes the infection. And, once Samsam gets a hold of your data, the only release is via key. If you apply the right decryption key, you free your files. And, to get it, you have to. pay up. That’s how ransomware work. They slither into your PC, corrupt it, and extort you. Once the tool completes the encryption, it lays out its demands. It shows you a ransom note, which contains an explanation. And, of course, instructions. Mos ransomware tools also include a passage of threats, so to speak. They let you know that there are repercussions to your inaction. The ransom may increase in amount. Or, your unique decryption key gets deleted. They expect you to be swift and decisive. In other words, careless and naive. Don’t let Samsam, and other such tools, trick you into doing something, you’ll regret. And, if you pay the ransom, you WILL regret it! Don’t give into the extortionists’ demands! It may seem like the worst thing to do, but forsake your files. Think about the consequences of paying the cyber kidnappers. And, remember, data is replaceable.
How did I get infected with?
One day, Samsam is just on your PC. And, its note is on your screen. You had no idea the infection was even there, and yet! Here it is. It’s taking over your PC. But how did it get there? It may seem that way to you, but infections don’t just pop up out of the blue. They need user’s permission. You have to give your consent to the tool’s installment. And, it uses a myriad of tricks to get it. Its arsenal involves freeware, spam email attachments, corrupted links. And, it can also pretend to be a bogus update. Like, Java. So, while you think you’re installing a Java update, you’re wrong. In actuality, you’re giving the green light to a dangerous cyber threat. An, you don’t even know it because you’re not attentive enough. Most users throw caution to the wind when installing such updates or tools. Don’t be that type of user! Don’t be careless! Infections prey on carelessness. Instead, be more cautious. Always take your time to do your due diligence. After all, even a little extra attention today can save you a ton of troubles tomorrow.
Why is Samsam dangerous?
After Samsam settles into your system, the encryption begins. The tool locks all your data. And, when it’s done, it makes demands. It lays out its requirements in a ransom note, it creates after encryption. Let’s elaborate. The infection uses the RSA-2048 asymmetric encryption algorithm to take over your files. And, when everything gets locked, it displays the note. The ransom note is an HTML file on your Desktop. It’s either named ‘HELP_DECRYPT_YOUR_FILES.HTML,’ or ‘001-HELP_FOR_DECRYPT_FILE.html.’ The ransom amount is pretty standard. Samsam asks 1 Bitcoin of you. If you don’t know much about Bitcoins, don’t think one is an acceptable or small amount. It’s not. Converted to US dollars, 1 Bitcoin equals about 600 US dollars. But it’s not the size of the ransom that should make you NOT pay. You shouldn’t pay because of the severe privacy risk that entails. If you comply with Samsam’s demands, you only worsen your predicament. And, it’s not worth it. Your data is not worth it. Consider this. Let’s examine your best case scenario. You follow the tool’s instructions, and all goes according to plan. You get the decryption key you need, and free your files. And, then what? The ransomware’s still there. The key does not remove the infection. It just releases your data from its hold. So, what’s to stop the cyber menace from striking back tomorrow? Or next week? Or an hour after decryption? Nothing. You have no guarantees that the ransomware will leave you alone. Not to mention, that by paying, you exposed your privacy. Oh, yes. When you transfer the ransom, you let strangers peek into your private life. The people behind Samsam now have access to your personal and financial details. And, once they get their hands on it, they can use it as they wish. Do you think that will end well for you? Don’t be naive. Don’t give into the ransomware’s demands. Say goodbye to your data, so you don’t have to say goodbye to your privacy.
Samsam Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Samsam Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Samsam encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Samsam encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.