Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove TrumpLocker Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
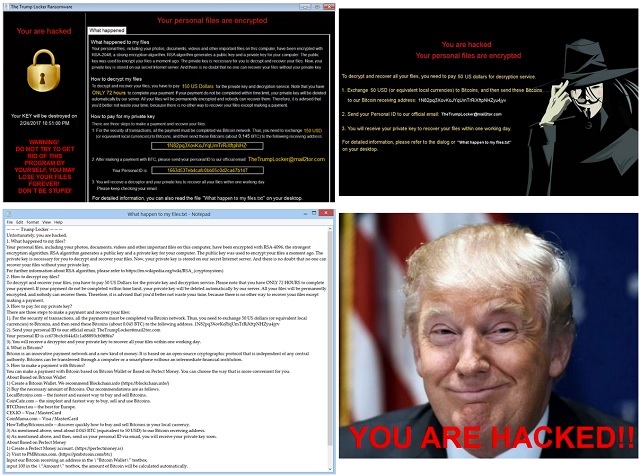
You are hacked
Your personal files are encrypted
To decrypt and recover all your files, you need to pay 50 US dollars for decryption service.
1. Exchange 50 USD (or equivalent local currencies) to Bitcoins, and then send these Bitcoins to our Bitcoin receiving address: 1N82pq3XovKoJYqUmTrRiXftpNHZyu4jyv
2. Send your Personal ID to our official email: TheTrumpLocker@mail2tor.com
3. You will receive your private key to recover your files within one working day.
For detailed information, please refer to the dialog or “What happen to myfiies.txt” on your desktop.
To say that Donald Trump is a popular name right now would be an understatement. The problem is, hackers didn’t miss that. They obviously got inspired by America’s controversial president. Hence, a brand new file-encrypting virus was born. Today’s article is all about the vicious TrumpLocker Ransomware. If you’ve ended up stuck with this pest, it’s time to take measures. Ransomware is one of the most destructive, aggressive and dangerous types of infections out there. Unfortunately, its title is well-deserved. The TrumpLocker Virus is actually identical to another ransomware named VenusLocker. Most file-encrypting programs follow the same pattern. That means if you’ve seen one ransomware nuisance, you’re pretty much seen them all. TrumpLocker is no exception. It utilizes a strong encrypting algorithm to lock your private files. What’s curious about this program is that it uses a 1024-byte encryption as well as a full one. As a result, your files receive one of two extensions – .TheTrumpLockerp or .TheTrumpLockerf. In addition, the target data gets renamed with a random combination of symbols. As mentioned, this virus uses a complicated cipher. The RSA-2048 cryptography turns all your private files into unreadable gibberish. You see, that is what hackers aim for. By locking your data, crooks are attempting to involve you in their nasty scam. That’s all that ransomware is – a cyber fraud. However, many people end up getting scammed and losing money. No wonder crooks constantly develop new file-encrypting viruses. Every hackers’ dream is gaining effortless revenue. Therefore, you cannot afford any wrong moves. TrumpLocker also replaces your desktop wallpaper with the picture of Donald Trump himself. It then starts demanding money from you. You will find the parasite’s ransom note in all folders that contain encrypted information. As you can probably tell, those are indeed a lot of folders. The virus takes down a huge variety of file formats. That includes pictures and photos, videos, documents, music, etc. Ransomware locks every single bit of data you’ve stored on your machine. According to its nasty notes (What happen to files.txt), you can regain access to your data by paying a ransom. Does making a deal with hackers sound like a great move, though? They promise you a unique decryption key in exchange for your money. And yet, they don’t deliver. The sole reason why TrumpLocker exists is to extort money from gullible PC users. In order not the fall right into hackers’ trap, tackle the ransomware on the spot. Restrain yourself from paying anything and know that crooks will not keep their end of the bargain.
How did I get infected with?
The parasite didn’t ask for your permission. That’s given. Hackers are aware that nobody would download such a harmful parasite voluntarily. Malware applies stealthy, secretive techniques instead. Number one method involves spam messages and email-attachments. Next time you receive something questionable in your inbox (RansomNote.exe), delete it ASAP. Remember that some dangerous infection could be hiding there. The key to your safety is caution. If you click open a corrupted email/message, you have nobody to blame but yourself. This is both an easy and effective way for crooks to compromise your device. Another thing to watch out for are unverified websites. Only download software that you trust and pay attention in the process. You may accidentally agree to install a virus when installing deceptive bundles. Also, ransomware travels the Web via malicious torrents, fake program updates and exploit kits. To top it all, this program may have used some help from a Trojan horse. It is definitely worth it to check out your PC for further parasites. The TrumpLocker ransomware may be having company.
Why is TrumpLocker dangerous?
You’re supposed to pay 150 USD in Bitcoins if you want to receive a decryptor. However, negotiating with hackers wouldn’t be your brightest idea. The TrumpLocker virus is trying to scare you into giving your money away. That means your panic and anxiety could cost you quite a lot of money. Do not contact crooks as they have no intention to free your data. Your files could remain encrypted and inaccessible even if you comply. Therefore, don’t even consider paying the ransom. If anything, that would only make your situation worse. To delete the ransomware manually, please follow our detailed removal guide. You will find it down below.
TrumpLocker Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover TrumpLocker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with TrumpLocker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate TrumpLocker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.