Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove xRat Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
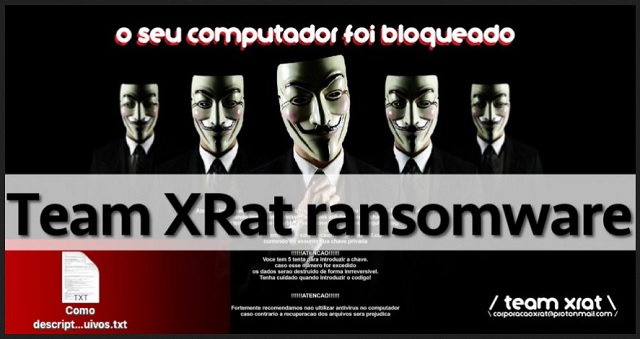
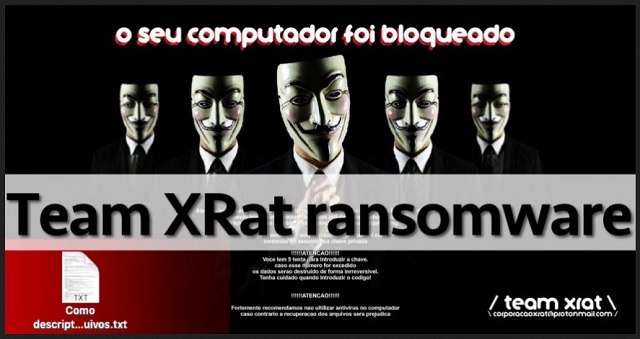
Atenção todos seus arquivos foram criptografados.
Utilizando criptografia RSA de 2048 bits.
tornando impossível a recuperação dos arquivos sem a chave
correta.
Caso tenha interesse em obter está chave, e recuperar seus
arquivos,
envie um email para corporacaoxrat@protonmail.com
Contendo no assunto sua chave privada
Chave Privada:
8nxs1yncowvwl52v8bay25q846761n0jilkod5px3y2enj
When someone mentions the term “PC virus,” most of us imagine Trojan horses. And there is a good reason for that. These parasites are stealthy, invasive and deadly. xRat Virus is one such Trojan. It falls into the ransomware category. It is, in fact, a ransomware with history. xRat Ransomware is the newest version of the infamous Xorist Ransomware. Just like its predecessors, this parasite is deadly. Upon infiltration, xRat modifies your System’s settings, particularly your Registry. It roots into your system. It corrupts files, alters your settings, and creates hidden files and folders. From this point onwards, the virus is almost unstoppable. It will load together with your OS and will never stop. Once established, xRat scans your HDD. It targets user-generated files, such as your pictures, documents, archives, data bases, etc. The virus uses a RSA-2048 encryption algorithm to lock all target files. The file encrypting process happens in the background. You may notice that your PC is slower than usual, but nothing striking. The virus is programmed to be stealthy. It won’t betray its cover. Only when the encryption process is finished, will the virus display its ransom note. As a classic ransomware, xRat replaces its victims’ backgrounds whit a ransom note. It states that you need to contact the hackers via email. We strongly recommend against such actions. You are dealing with criminals. Do not get in touch with them. These people will double-cross you for sure. Unfortunately, there are no decryption tools for this ransomware. xRat Ransomware is an untrustworthy, dangerous parasite. Don’t be naive. Stay away from it and the hackers behind it. Consider discarding your files. Clean your machine with a powerful anti-virus program and start backing up your files regularly. This way you will be prepared if a ransomware strikes again!
How did I get infected with?
To reach its victims, xRat Ransomware relies on spam email attachments. Yes, even today, the good old spam emails are the main cause of virus infections. The hackers are imaginative. Your spam filters cannot catch all unwanted messages. Your caution, however, can keep your machine clean. Do not open emails from strangers. Verify the sender first. You can simply enter the questionable email address into some search engine. If it was used for shady business, someone might have complained online. Yet, this technique is not flawless. If you are a part of the first wave of spam messages, there might be no evidence yet. So, double-check the sender. The crooks tend to write on behalf of well-known companies. If you receive such a letter, go to the company’s official website You can find their authorized email addresses there. Compare them with the one you have received a message from. If they don’t match, delete the pretender immediately. If you open an email containing attachments, don’t download them unless you are absolutely sure that they are safe. Just to be on the safe side, scan the downloaded files with a trustworthy anti-virus program.
Why is xRat dangerous?
xRat Ransomware is a classic infection. It sneaks into your computer unnoticed and wreaks havoc. The virus locks your precious files and denies you access to them. You can see the icons of your pictures, videos, music, but you cannot open or use them. The obnoxious parasite demands money to restore your files. Yet, it cannot guarantee you results. The hackers are not famous for their honor. They will tell you what you want to know. Once you pay, they are likely to ignore you. Or worse, they may demand more. Even if they send you a decryption tool, it may not work. Or it may work just partly. We recommend against paying the ransom. Such actions will only drain your banking account. You are dealing with dangerous cyber criminals. They did not hesitate to invade your PC. They will not hesitate to take your money. You cannot ask for a refund. Your best course of action is the removal of the virus. If you skip this essential step, xRat will continue to work in the background. And this means only one thing — you cannot use your PC normally. The ransomware will encrypt every new file you create. Keep in mind that Trojan horses were originally used to spy on their victims. xRat Ransomware is a Trojan. A Trojan Ransomware but a Trojan nonetheless. It can monitor your activities and catalog your actions. If you use your infected PC to pay the ransom, you give the virus a chance to record your paying details. Credit card details, bank account, usernames, passwords, etc. Can you imagine what may happen if the hackers discover that information? The consequences will be devastating! Don’t risk it. Clean your computer ASAP!
xRat Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover xRat Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with xRat encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate xRat encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.