Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Buhtrap Virus. The step by step removal works for every version of Microsoft Windows.
Buhtrap is a dangerous Trojan Horse. This havoc-wreaking virus infects your entire OS. It messes with your system settings, modifies the registry, drops malicious files, and starts dangerous processes. These operations, of course, have no noticeable symptoms. You cannot catch the virus in time to prevent its infiltration. Once it gets your OS under control, however, you might experience annoying malfunctions, freezing, and unexpected crashes. Buhtrap messes with essential system directories and may cause various errors. This, however, is not very likely as this Trojan follows programming to be stealthy. Its main purpose of existence is to open an unnoticeable backdoor to your OS. The news is very bad! The Trojan helps other malware and viruses corrupt your operating system. Buhtrap downloads and installs parasites, as well as malicious updates. Security researchers add that it also installs/removes hidden extensions that compromise legitimate apps such as anti-virus utilities, web browsers, and others. Do not waste time in debates. The more time this virus spends on your computer, the worse your predicament gets. Your best and only course of action is the immediate removal of the virus.
How did I get infected with?
Buhtrap travels the Web through malvertising, corrupted links, and malicious websites. The crooks post malicious ads that usually target specific business sectors. They spread ads that promote free downloads of various software, documents, templates, applications, and contracts. The landing websites look professional and legitimate. They, however, offer malicious downloads. As soon as you open their files, the Trojan’s payload infects your OS. Do not give into naivety! The Internet is a dangerous place. You can never know where a virus might strike from. Don’t download files from unknown sources. Take the time to do your due diligence. Do your research. Find reputable, preferably official sources. Even a little extra attention can spare you an avalanche of problems. Bear in mind that a malicious file may make its way to your computer via email as well. Although Buhtrap seems to be spread mainly through malvertising, this virus may also reach your PC through spam messages. Be very careful with your inbox. Whether it’s an instant message or an email, treat all unexpected messages as potential threats. Always verify the senders. If, for example, you receive an email from an organization, go to their official website. Compare the email addresses listed there to the questionable one. If they don’t match, delete the pretender. You can also enter the suspicious addresses into a search engine. If they were used for questionable activities, someone might have complained online!
Why is this dangerous?
Buhtrap is a nightmare. It slithers into your computer through deception, infects every component of your OS and opens a backdoor. No one can tell you what the future holds for your device. Buhtrap is an unpredictable virus that affects its individual victims differently. The virus, of course, won’t do you a favor. This Trojan has only one purpose of existence: to help its criminal creators cause harm. From annoying adware to destructive ransomware, the Trojan floods its victims’ OS with various malware. And it doesn’t stop just here. Buhtrap also spies for its operators. This virus knows your system properties, where your files are located, what apps you have installed, your IP and MAC addresses. If its owners desire, the virus installs spyware and keyloggers, and thus, monitors even more data points. This intruder threatens to steal personal information, financial details, and login credentials. And that’s just the top of the iceberg! The hackers can use this Trojan to command your computer remotely. Do you think that ends well? The Trojan has unrestricted control over your computer. Its operators can use it to steal, corrupt or delete your files; to spy on you; to wreck your device. Do not wait to see what these criminals plan for your computer. As soon as you become aware of the Trojan’s presence, take action. Find where this virus hides and delete it upon detection. The sooner you clean your OS, the better!
Manual Buhtrap Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The Buhtrap infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Buhtrap infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down Buhtrap related processes in the computer memory
STEP 2: Locate Buhtrap startup location
STEP 3: Undo the damage done by the virus
STEP 1: Track down Buhtrap related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Buhtrap startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Buhtrap virus from the windows registry
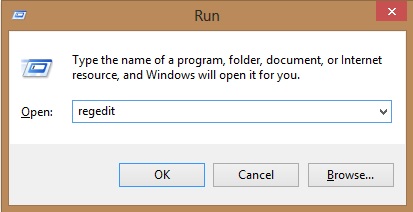
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
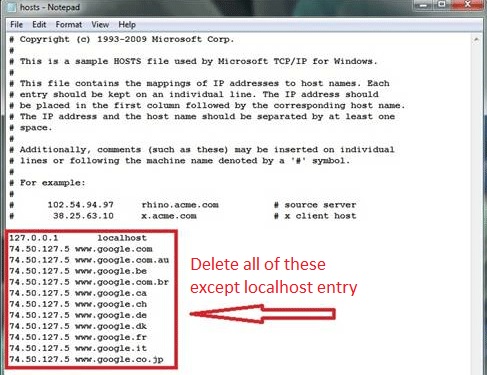
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 3: Undo the possible damage done by Buhtrap
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Buhtrap, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Buhtrap Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.