Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove CoreSync Virus. The step by step removal works for every version of Microsoft Windows.
Trojans are known to impersonate legitimate processes and CoreSync.exe (a legitimate Adobe process) is their latest victim. A coin-mining Trojan uses this name to camouflage its malicious processes. If this process runs in the background and slows your PC down, if issues pop up out of the blue, the news is bad! Your computer harbors a virus. You are stuck with a resource thief! The CoreSync Trojan is a menace that corrupts your computer and uses its resources for coin mining. The parasite forces your machine to run heavy processes that burden your CPU and GPU. These operations can be quite profitable. The revenue, however, is not for you but for the Trojan’s operators. You are left only with the side effects and the potential risks! CoreSync takes everything your computer has to offer and spares nothing for you and your programs. The parasite makes your operating system sluggish and unresponsive. It causes your apps to load slowly and crash frequently. It is behind countless odd errors and crashes. The Trojan could also force you to reboot your computer repeatedly. A simple restart, however, won’t fix your problems! CoreSync loads together with your OS and always runs in the background. Don’t put up with this invader. Your best course of action is its immediate removal.

How did I get infected with?
CoreSync Trojan sneaks into your computer and wrecks your OS. Don’t, however, imagine cyber-attacks. This Trojan spreads through mass-distribution tricks, not through targeted attacks! It travels the web hidden in malicious bundles, spam messages, corrupted links, and, of course, pirated software. The parasite relies on trickery and prays on naive users. CoreSync Trojan lurks in the shadows and infects your PC when you throw caution to the wind. Don’t give into naivety! No anti-virus app can protect you if you act that recklessly. Your diligence is the key to a secure and infection-free computer. Only your actions can prevent infections, so don’t be lazy. Always take the time to do your part. Don’t visit dodgy websites. Download software and updates from reputable (preferably official) sources only. And, of course, be very wary of your inbox. Whether it’s an instant message or email, treat all unexpected messages as potential threats. Always verify their senders. If, for example, a company or organization unexpectedly contacts you via email, go to their official website. Compare the email addresses listed there to the questionable one. If they don’t match, delete the pretender immediately. You can also double-check the suspicious senders by entering their handles or addresses into a search engine. If they were involved in shady activities, someone might have complained online.
Why is this dangerous?
CoreSync Trojan is a complete and utter menace. It sneaks into your computer and wrecks everything. It alters settings, modifies the registry, drops files, starts malicious processes. This, of course, happens in complete silence. The virus corrupts your OS without triggering any alarms. You can’t catch it in time to limit its corruption. Everything, however, changes once the virus gets your device under control. CoreSync affects every aspect of your user experience. It makes your operating system sluggish and unresponsive, causes your apps to malfunction, triggers errors and crashes. You can’t so much as browse your favorite websites without encountering problems. Don’t, however, mistake these performance issues for the essence of the problem. These are just symptoms of the infection. You risk ending up with a wrecked machine and an expensive electricity bill! CoreSync doesn’t limit its resources consumption but exploits your CPU. It doesn’t pause its mining processes even when your CPU’s temperature reaches dangerously high levels. Such prolonged mining leads to irreparable hardware damage. Not to mention that it affects your electricity bill. The coin mining operations are profitable only if you don’t use your own resources. CoreSync uses yours! The Trojan’s operators make a mint at your expense. Don’t become their sponsor. Remove their parasite ASAP! Find where CoreSync lurks and delete it for good!
Manual CoreSync Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The CoreSync infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the CoreSync infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down CoreSync related processes in the computer memory
STEP 2: Locate CoreSync startup location
STEP 3: Delete CoreSync traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down CoreSync related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate CoreSync startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean CoreSync virus from the windows registry
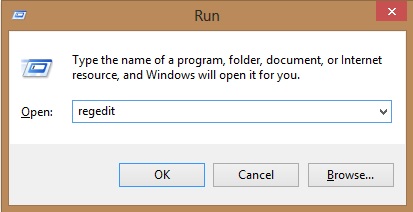
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
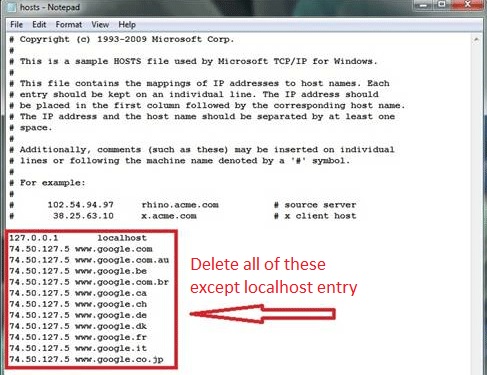
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by CoreSync
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for CoreSync, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove CoreSync Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.