Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Crab File Virus Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
— “GANDCRAB V2.1 “—
Attention!
All your files documents, photos, databases and other important files are encrypted and have the extension: .CRAB
The only method of recovering files is to purchase a private key. It is on our server and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
0. Download Tor browser – https://www.torproject.org/
1. Install Tor browser
2. Open Tor browser
3. Open link in TOR browser: http://gandcrab2pie73et.onion/95???????????
4. Follow the instructions on this page
If Tor/Tor browser is locked in your country or you can not install it, open one of the following links in your regular browser:
0. https://gandcrab2pie73et.onion.rip/95?????????????
1. https://gandcrab2pie73et.onion.plus/95?????????????
2. https://gandcrab2pie73et.onion.to/95?????????????
ATTENTION! Use regular browser only to contact us. Buy decryptor only through TOR browser link or Jabber Bot!
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
The alternative way to contact us to use Habber messanger. Read how to:
0. Download Psi-Plus Jabber Client: https://psi-im.org/download/
1. Register new account: https://sj.ms/register.php
0) Enter “username”: 95???????????
1) Enter “password”: your password
2. Add new account in Psi
3. Add and write Jabber ID: ransomware@sj.ms any message
4. Follow instruction bot
It is a bot! It’s fully automated artificial system without human control!
To contact us use TOR links. We can provide you all required proofs of decryption availability anytime. We are open to conversations.
You can read instructions how to install and use jabber here http://www.sfu.ca/jabber/Psi_Jabber_PC.pdf
DANGEROUS!
Do not try to modify files or use your own private key – this will result in the loss of your data forever!
Gandcrab v3.0 is a variant of the GandCrab ransomware family. Once your computer gets infected with it, the encryption of various file types begins. Those files receive the .crab extension. After the encryption is done, this malware restarts the computer and shows an unpleasant page on Windows startup saying the victim must open a file with instructions. In this text file, Gandcrab v3.0 extorts the user for money in the form of cryptocoin. This virus is probably the first malicious software so far that accepts Dash coins. Once the text file with instructions is opened, there is a specific time frame in which the victim can operate and pay the ransom. The asked amount is around $1000 and can be paid in either BitCoin or Dash cryptocoin.
How did I get infected with?
Often the infection has taken place by one of the following ways: through spam emails, attachments and executable files, from installation of repackaged and infected software bundles, fake updates, etc. According to malware researchers, Gandcrab v3.0 ransomware can also be distributed via the Magnitude exploit kit. Every user is advised to think twice before opening letters from unknown senders. Using spam filters is also recommended in order to prevent opening emails that may potentially carry dangerous content. If you notice the .crab extension added to your personal files, it is a clear indication that your computer carries the Gandcrab v3.0 infection.
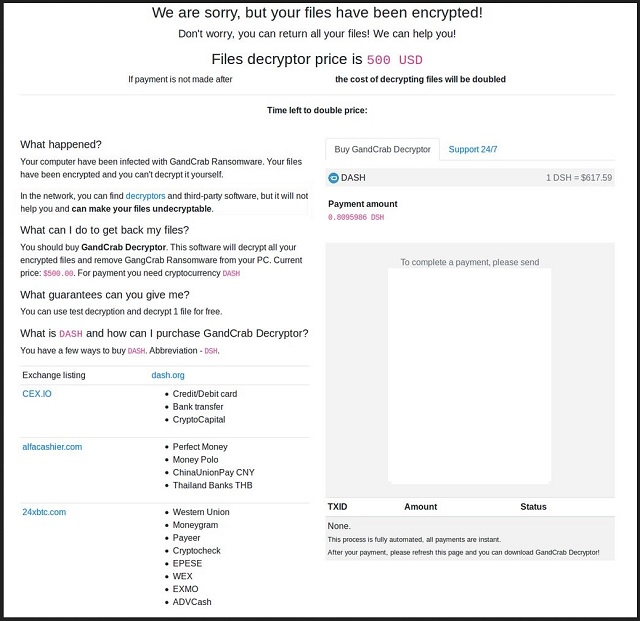
Why is Crab File Virus dangerous?
The thing with ransomware is that even if the victim follows through with the cyber criminal’s demands and pays the ransom, it still doesn’t necessary mean that their encrypted data will be restored. So don’t be too quick to open your wallet because your diligence will mean nothing to those hackers. After all, they are called criminals for a reason, which is why they do not feel the obligation to fulfill their promises. That being said, making sure that you backup your important data would be the smart thing to do. You never know what might happen. Even the most cautious users can fall victims to malicious software. However, if you notice that your computer is infected with the Gandcrab v3.0 ransomware, there are things you can do to decrypt your files and remove the infection from your computer.
Crab File Virus Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Crab File Virus Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Crab File Virus encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Crab File Virus encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


