Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Gandcrab v4 Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
–= GANDCRAB V4 =—
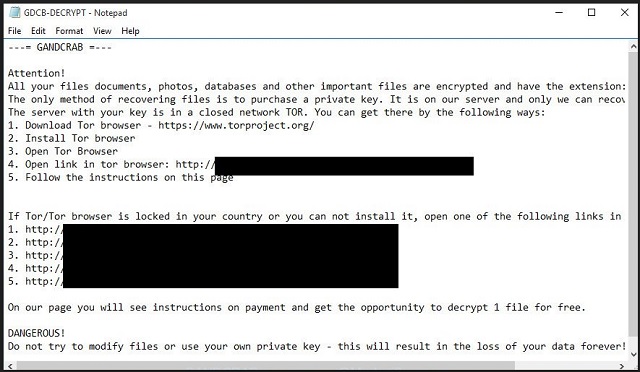
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension: .KRAB
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
—————————————————————————————-
| 0. Download Tor browser – https://www.torproject.org/
| 1. Install Tor browser
| 2. Open Tor Browser
| 3. Open link in TOR browser: ***
| 4. Follow the instructions on this page
—————————————————————————————-
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
—BEGIN GANDCRAB KEY—
lAQAADcGuK2O86SjorV5S***2252_chars***3xoPSX/TrEnwTiQ76HdztGYuXZ4KO7rogc=
—END GANDCRAB KEY—
—BEGIN PC DATA—
wfKD6iudumBkmpL8IRr4U7***76_chars***mMngioqtOiJtTit2DjRIuBtNYA==
—END PC DATA—
The Gandcrab ransomware is nothing new in the cyber crime field. So far, there have been three separate versions of it, plaguing users. And, now, it’s making yet another comeback. The Gandcrab version 4 is out and about, and users are crying out. The ransomware slithers its way into your system, and doesn’t waste time. It runs a full system scan, in search of files to encrypt. It proceeds to lock every single file you have, and doesn’t let you access anything. The only exceptions are files that are essential for your operating system. Everything else gets locked, and becomes unreachable. Photos, documents, videos, music. It all falls under the infection’s control. Gandcrab v4 uses a complex combination of encryption algorithms. That includes AES-256 (CBC-mode), Salsa20 and RSA-2048. It adds the specific ‘krab‘ extension at the end of each file. Thus, solidifying its hold over your data. Once the extension gets added, that’s it. You can longer reach your own files. After the encryption is complete, the infection leaves you a note. It’s called KRAB-DECRYPT.txt, and it contains its demands. The ransom note explains your situation, and lists several requests. They include the following. The ransom must get paid in Bitcoin. The exact amount may vary. But it tends to stay in the range from 200 to 1000 US Dollars. You must purchase a unique decryption key to unlock your data. To do so, you must reach out to the cyber kidnappers ASAP. Every minute you waste may end up costing your files. The cyber criminals may threaten to delete some of your files, if you delay payment. Heed experts’ advice, and do NOT pay a dime! Don’t contact these people. Don’t call, don’t write, don’t do a thing. The best course of action is to cut your losses, and say goodbye to your data. It’s a tough call to make, but it’s the right one.
How did I get infected with?
The nasty infection slithers its way in via deception. It resorts t slyness and finesse, and invades undetected. Yes, it gains access to your PC, without you even realizing it. You only become aware of its stay, once you get greeted with your data locked. But how? How does Gandcrab v4 sneak in unnoticed? Well, it preys on your carelessness. That’s right. The tool only pulls off its deception, because you allow it. You give into naivety, and rush. You throw caution to the wind, and skip doing due diligence. And, that opens the door to the horrendous cyber threat. The tool uses spam email attachments, corrupted links or sites. Of course, freeware is always an option. It can also pose as a bogus update. Like, Adobe Flash player or Java. There’s a multitude of methods, it can turn to. It’s up to you to look through its deceit. And, spot it attempting infiltration. You’re the last line of defense! Choose caution over carelessness. Take the time to be thorough, and remember that vigilance keeps threats out. The lack thereof invites them in.
Why is Gandcrab v4 dangerous?
Here’s why, saying goodbye to your files, is the right thing to do. Don’t forget that you’re dealing with cyber criminals. The people, behind Gandcrab v4, are malicious third-parties. They’re unknown individuals with questionable intentions. Do you expect these strangers to keep their word? To follow through on their promises? Don’t be naive! These people only want your money. They don’t care about your files. Once you pay, and they get your money, that’s it. They have reached their end-game. With or without making payment, the result is the same. You will NOT get your files back. The only safe and proper way to get a hold of them is through backups. Either cloud services, or external storage. Otherwise, they’re as good as lost. The ransomware may promise to sell you a decryption key, but can you expect it to? What if it gets your money, and doesn’t send a key? Or, sends the wrong one? And, even in the off-chance that it gives you the right one, what then? You may decrypt your data, but the reason it got encrypted, still lurks on your PC. What if it acts up again, and locks everything once more? Will you continue to throw money at the cyber criminals behind Gandcrab v4? Make the right call. Forget about your encrypted files. Gandcrab v4 forces you into a game that’s set up for you to lose. Accept that, and move on.
Gandcrab v4 Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Gandcrab v4 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Gandcrab v4 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Gandcrab v4 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


