Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove LockerGoga Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
Greetings!
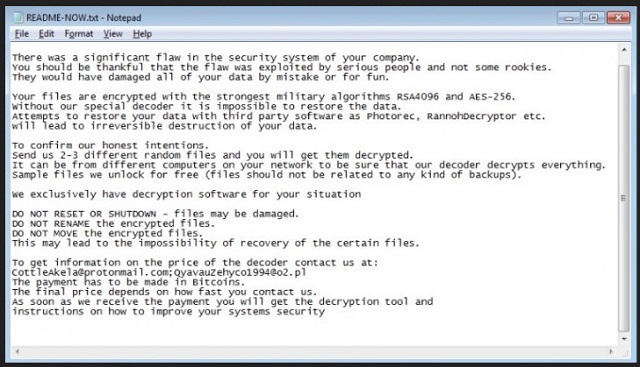
There was a significant flaw in the security system of your company.
You should be thankful that the flaw was exploited by serious people and not some rookies.
They would have damaged all of your data by mistake or for fun.
Your files are encrypted with the strongest military algorithms RSA4096 and AES-256.
Without our special decoder it is impossible to restore the data.
Attempts to restore your data with third party software as Photorec, RannohDecryptor etc.
will lead to irreversible destruction of your data.
To confirm our honest intentions.
Send us 2-3 different random files and you will get them decrypted.
It can be from different computers on your network to be sure that our decoder decrypts everything.
Sample files we unlock for free (files should not be related to any kind of backups).
We exclusively have decryption software for your situation
DO NOT RESET OR SHUTDOWN – files may be damaged.
DO NOT RENAME the encrypted files.
DO NOT MOVE the encrypted files.
This may lead to the impossibility of recovery of the certain files.
To get information on the price of the decoder contact us at:
CottleAkela@protonmail.com;QyavauZehyco1994@o2.pl
The payment has to be made in Bitcoins.
The final price depends on how fast you contact us.
As soon as we receive the payment you will get the decryption tool and
instructions on how to improve your systems security
LockerGoga is the name of a nasty ransomware threat. It sneaks into your system via trickery. Then, corrupts it! The infection locks your data, and demands you pay ransom, if you wish to change that. Let’s elaborate. LockerGoga uses RSA-4096 and AES-256 cryptography algorithms to encrypt your data. And, it targets all your data! Nothing escapes its touch. Pictures, documents, archives, music, videos. It all falls under the tool’s encryption. To solidify its grip over your files, LockerGoga appends a special extension. Say, you have a photo called ‘yes.jpg.’ After the ransomware’s done with it, it gets renamed. It becomes ‘yes.jpg.locked!?’ or ‘yes.jpg.locked.’ Once the extension is in place, that’s it. Your files are no longer accessible. You can’t open them, and moving or renaming them doesn’t help. The only way to regain control over them is to decrypt them. And, to do that, you must pay a ransom. The ransomware makes that quite clear in the ransom note, it leaves for you. After the encryption, you can find it on your Desktop. As well as, in every folder containing locked files. It goes by the name “README-NOW.txt.” And, it’s pretty standard. The note clues you into your predicament, and gives you a way out. Supposedly, if you comply, and pay the ransom, you’ll unlock your data. The cyber criminals claim that, once they receive payment, they’ll send you the key. The decryption key, you need to apply, and free your files. The amount you have to pay, “depends on how fast you contact us.” And, “the payment has to be made in Bitcoins.” Here’s the thing. Even if the price is a single dollar, do NOT pay! Compliance guarantees you nothing. Save your money.
How did I get infected with?
How did LockerGoga end up on your computer? Well, it’s there, because of you. You got careless at a most inopportune moment. And, the ransomware is the price you pay for that carelessness. Here’s the thing. Ransomware tools prey on users’ distraction, haste, and naivety, to invade. They need you to throw caution to the wind, rush, and rely on luck. Your carelessness eases their infiltration. So, don’t provide it! Do the opposite, and be extra thorough. The usual methods, the infection uses, include the following. Freeware, fake updates, corrupted sites, links, or torrents. And, of course, spam emails. You get an email that claims to come from a reputable source. More often than not, Amazon, or some other well-known company. It reads that you must download an attachment, or click a link. So, you can verify a receipt or order. The email feeds you lies to get you to act against your best interest. Don’t fall for its trickery. Do your due diligence. Be thorough enough to spot the deception. Even a little extra attention can save you a ton of problems. Vigilance goes a long way. The lack thereof tends to result in tools, like LockerGoga, ending up on your PC.
Why is LockerGoga dangerous?
After LockerGoga strikes, you have a choice to make. You must decide whether to believe the promises of cyber criminals. Or, not. It seems a simple choice to make, doesn’t it? You must realize that you’re dealing with unknown individuals with malicious intentions. Strangers, who locked your data, and demanded you pay them money. Don’t waste your money, time, and energy dealing with them. In case, you’re not convinced, let’s examine your options. Say, you choose to believe the cyber kidnappers’ word. You pay the ransom. Then, what happens? Well, you wait to receive the decryption key, they promised you. But what if you don’t get one? That’s quite a common development. The extortionists may double-cross you, and send you nothing. Then, you’ve lost money, and your data stays locked. But even if you do get a key, don’t rejoice just yet. It’s also a common occurrence that you get a key that doesn’t work. So, again. You’re left with locked files, and less money. And, even getting the proper key, is no cause for celebration. If the cyber criminals keep their word, and you get the right key, what then? Think about it. You paid money to remove a symptom. Not the infection, causing it. So, you may get rid of the encryption, but the ransomware remains. And, it’s ready to strike again. If it does, you’re back to square one, with locked data, and less money. The odds are not in your favor. Don’t take chances. Make the tough, but right call, and don’t pay the cyber criminals, behind LockerGoga.
LockerGoga Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover LockerGoga Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with LockerGoga encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate LockerGoga encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


