Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Ryk Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
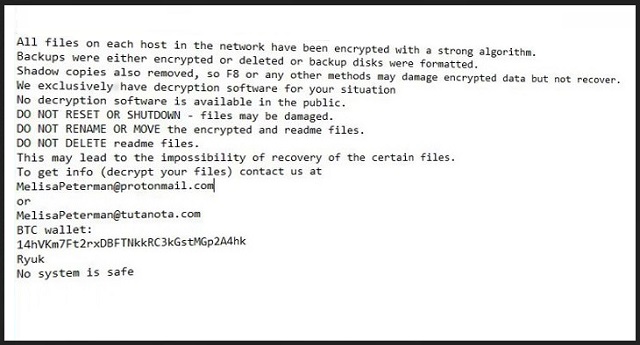
Your network has been penetrated.
All files on each host in the network have been encrypted with a strong algorithm.
Backups were either encrypted
Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.
We exclusively have decryption software for your situation.
More than a year ago, world experts recognized the impossibility of deciphering by any means except the original decoder.
No decryption software is available in the public.
Antiviruse companies, researchers, IT specialists, and no other persons cant help you encrypt the data.
DO NOT RESET OR SHUTDOWN – files may be damaged.
DO NOT DELETE readme files.
To confirm our honest intentions.Send 2 different random files and you will get it decrypted.
It can be from different computers on your network to be sure that one key decrypts everything.
2 files we unlock for free
To get info (decrypt your files) contact us at
CharlstonParkwji@protonmail.com
or
Huntingdonu@tutanota.com
You will receive btc address for payment in the reply letter
Ryuk
No system is safe
Ryk is the name of a ransomware threat. Users have named it so, because of the extension they get stuck with. They find it at the end of each of their locked files. Let’s explain. The Ryk threat is a variant of the RYUK ransomware. It uses slyness to invade your PC, then corrupts it. It uses cryptography algorithms to encrypt your data. All of it! It targets pictures, documents, videos, music, archives. Everything falls under its encryption. To solidify its hold over your files, the tool appends a special extension at the end of each one. That extension is ‘.ryk.’ Hence, the name of the infection. After the encryption process finishes, your data is unusable. The infection renders them inaccessible. You can try to rename or move them, but it’s futile. The only way to decrypt them is via a special decryption key. And, if you wish to get it, you must follow the infection’s demands. It lays them out in the ransom note, it leaves for you. It’s called “RyukReadMe.txt,” and you can find it on your Desktop. The note urges you to comply. It promises that, if you do, you’ll get your files unlocked, and usable again. Don’t buy it! Don’t fall for the deceptive promises! Remember that you’re dealing with cyber criminals, who extort you for monetary gain. You can’t trust them to keep their word. So, don’t.
How did I get infected with?
How does the ransomware find its way on your PC? Well, it’s because of you. You were careless enough to let it slip by you, unnoticed. You didn’t catch it, attempting invasion, so you missed out on denying it access. It may seem a bit confusing, so let’s elaborate. Tools, like Ryk, sneak in due to your carelessness. They prey on your gullibility and haste, and rely on you to throw caution to the wind. Your distraction eases their infiltration. So, make sure not to provide it. And, instead, take the time to be extra thorough. You see, the infection uses the old but gold invasive methods. That means, it hides behind freeware, corrupted links, fake updates. It has its pick of tricks. Of course, it most often uses spam campaigns. One day, you get an email that appears to come from a legitimate source. You open it, and see it contains an attachment or a link. The email urges you to download or click its contents, and if you do, you end up with malware. That’s why, caution is crucial. If you wish to keep an infection-free PC, be cautious! Don’t leave your fate to chance. Read terms and conditions, double-check everything, look for the fine print. Even a little extra attention can save you countless issues. Make sure you know what you allow into your PC. Choose caution over carelessness.
Why is Ryk dangerous?
Ryk’s note is pretty standard. It reads that your files got encrypted “with a strong algorithm.” And, not only that, but your backups are also locked. And, your “shadow copies removed.” The message aims to frighten you into compliance. It’s classic scare tactics. The extortionists try to convince you that your only way out is to pay them. They demand you contact them via email, and they’ve provided two addresses. You can use either one to reach out, and when you do, they’ll send you further instructions. They’ll tell you the exact ransom amount, and a Bitcoin wallet to send the money to. Yes, the ransom is to get paid in Bitcoin. 1 Bitcoin can be anywhere between 500 and 1000 US Dollars, or more. And, the ransom demand can be 2, 3 or even 5 Bitcoin. But even if it weren’t, you still shouldn’t pay. Even if the cyber kidnappers request one single dollar from you, don’t pay it. Don’t play their game, for you can’t win. Think about it. What are your options? You pay them, and then wait for the decryption key. But what if they don’t send one? Or, send the wrong one? And, even if they give you the right one, what then? You paid to receive a key that removes a symptom, not the infection itself. So, the infection remains, ready to strike again. And, if it does, you’re back to square one, with your data locked. Only this time, you have less money. So, you see, you’re left at the mercy of malicious strangers. That won’t end well either way you look at it. Don’t comply. Don’t reach out. Don’t pay.
Ryk Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Ryk Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Ryk encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Ryk encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


