Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Trojan.Shelma.cmj Virus. The step by step removal works for every version of Microsoft Windows.
Trojan.Shelma.cmj falls under the dreaded Trojan umbrella. It’s a menacing cyber threat that causes quite the damages. As soon as it slithers into your system, it proceeds to wreck it. The infection spreads corruption. And, throws you into a whirlwind of headaches and frustration. The infection doesn’t only mess with your system’s well-being. It also jeopardizes your privacy. The Trojan follows instructions to spy on you. As soon as it invades, it starts to track your online activities. It monitors everything you do, while browsing. Pages you visit, links you click, what holds your attention. Also, logins, passwords, credit card and bank account details. It keeps an eye on everything. But it doesn’t only observe, it records, as well. Yes, the nasty cyber threat collects information on your activities. And, when it deems it has gathered enough, proceeds to send it. Let that sink in. Trojan.Shelma.cmj steals sensitive information from you, and then exposes it. It hands it over to the cyber criminals behind it. That means, unknown third parties get their hands on your personal and financial data. Do you think you can trust these strangers with it? Don’t be naive. No matter how you look at it, it won’t end well for you. Protect yourself, and your system, from the clutches of the Trojan. Avoid the whirl of unpleasantness, it throws you in. Get rid of the atrocious infection the first chance you get. Remove Trojan.Shelma.cmj ASAP.

How did I get infected with?
The Trojan managed to slither past you, unnoticed. How? Well, it preys on your carelessness. Yes, you ease the tool’s infiltration by not paying attention, when it’s crucial to do so. For example, freeware is a common invasive method, used by Trojans. They use it to conceal their presence. And, if you’re not careful enough to pot them, attempting their trickery, that’s it. They slip by, undetected. Caution helps you to catch cyber threats in the act. And, deny them entry. Keep that in mind, every time you allow anything off the web, into your PC. Other common methods include the following. Hiding behind spam emails, corrupted links or torrents. Pretending to be a system or program update, like Java, for example. The Trojan has a plethora of ways to attempt invasion. It’s up to you to manage to spot it, and prevent its success. To do so, you must be vigilant. Take the time to read terms and conditions, and look for the fine print. Even a little extra attention can save you countless issues. Remember that caution keeps threats, like Trojan.Shelma.cmj, out. But carelessness invites them in. Make the right choice.
Why is this dangerous?
Trojan.Shelma.cmj is hazardous. It has the power to force changes on you. It can alter important settings, as well as files. It can even download cyber threats, and fill your PC to the brim with malware. That can cause you to see blue quite often. Yes, The Blue Screen of Death is a valid possibility. Granted, it’s a pretty minute one. But ‘minute’ isn’t the same as ‘non-existent.’ So, don’t dismiss the danger! The infection modifies browser preferences. It can switch your default homepage and search engine. It leads to constant redirects to suspicious sites. As well as, a full-on bombardment of op-up, in-text, and banner ads. It eats up space and resources. All that doesn’t go unnoticed. Your system starts to suffer frequent crashes. And, your computer’s performance slows down to a crawl. Trojan.Shelma.cmj also uses scare tactics to get you to act against your better judgment. It displays error messages and warnings, alerting you of threats that don’t exist. It urges you to call bogus support lines. And, contact technical experts that are utter impostors. Or, download fake programs, and purchase fraudulent tools that claim to be helpful. Don’t follow that advice. The presence of Trojan.Shelma.cmj leads to a horrendous experience. Your system suffers, and your privacy is in danger. Don’t take such unnecessary risks. Get rid of the harmful infection at once.
Manual Trojan.Shelma.cmj Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The Trojan.Shelma.cmj infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Trojan.Shelma.cmj infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down Trojan.Shelma.cmj related processes in the computer memory
STEP 2: Locate Trojan.Shelma.cmj startup location
STEP 3: Delete Trojan.Shelma.cmj traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down Trojan.Shelma.cmj related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Trojan.Shelma.cmj startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Trojan.Shelma.cmj virus from the windows registry
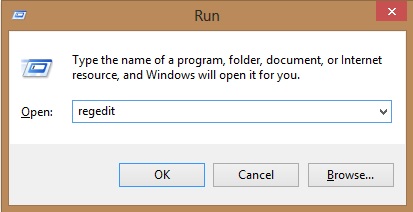
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
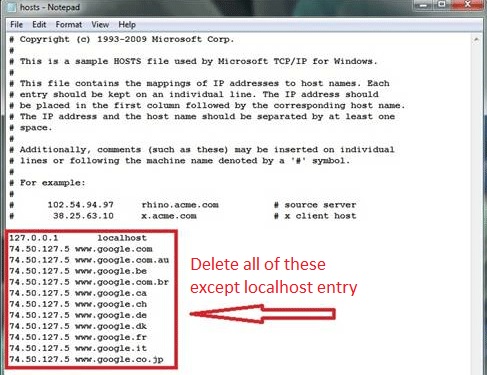
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by Trojan.Shelma.cmj
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Trojan.Shelma.cmj, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Trojan.Shelma.cmj Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.