Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Wacatac Virus. The step by step removal works for every version of Microsoft Windows.
Wacatac, also known as Trojan:Win32/Wacatac, belongs to the Trojan family. It’s a dangerous and damaging cyber threat. One that invades via trickery and deceit. Then, spreads corruption throughout, and makes a mess. The sooner you get rid of the threat, the better. Its extended stay earns you nothing but grievances and regret. Do yourself a favor, and follow experts’ advice. Remove the atrocious infection as soon as you get the chance. That way, you’ll avoid a plethora of problems. You see, the Trojan wastes no time to wreak havoc. Once it settles on your system, its mess-making begins. The Trojan meddles with your Task Manager, Registry, and system settings. It may cause your computer to restart, on its own accord. And, you may discover a variety of files have disappeared, or gotten corrupted. Your screen often gets covered in error messages, alerts and warnings. You experience trouble going online as it may restrict your Internet access. Or, block it altogether. And, when you do go online, you face continuous interference. The tool redirects you to suspicious third-party pages. And, floods your screen with ads. Your computer’s performance slows down to a crawl. Your system starts to suffer frequent crashes. Certain applications may open with difficulty, or even refuse to run. The Trojan ears up space and resources from day one. The more you extend its stay, the worse your situation gets. That’s why, it’s best to get rid of the cyber threat as soon as you get the chance. That way, you’ll ensure your system’s well-being. As well as, prevent your private information from getting stolen and exposed. Yes, that’s yet another hazard from having a Trojan on board. Do yourself a favor, and remove the Wacatac menace ASAP.

How did I get infected with?
How do you suppose you end up with Wacatac? Trojans may seem to pop up out of the blue, but that’s not the case. These infections infiltrate your system via trickery and finesse. They prey on your carelessness. They dupe you into permitting their admission. All, while keeping you oblivious. How? Well, they turn to the old but gold invasive methods. And, above all, rely on you to choose carelessness over caution. You see, caution allows you to spot the tool in the act of attempting invasion. You can catch it, and deny it entry. Carelessness, however, has the opposite outcome. So, Trojans like Wacatac, need you to leave your fate to chance. To rush, skip doing due diligence, and give into naivety. Your carelessness eases its covert infiltration. So, don’t provide it. Instead, take the opposite approach, and be extra thorough. Always be vigilant! Click nothing and agree to nothing, without a careful examination first. Take the time to be thorough. Even a little extra attention goes a long way, and it can save you countless troubles. Remember. Caution allows you to keep trouble out. Carelessness invites it in. Choose wisely.
Why is this dangerous?
The Trojan places your PC in grave danger. It threatens to fill it to the brim with malware. Yes, the infection can allow the installment of as many malicious tools as it chooses. And, what if your computer gets too overwhelmed? What if it can’t take the presence of so many infections? Well, in that case, you get stuck with the dreaded blue. Yes, The Blue Screen of Death is a valid possibility. Sure, it’s a rather minute one. But ‘minute’ is not the same as ‘non-existent.’ So, don’t risk it. Remove the Wacatac threat as soon as you can, and avoid all that trouble. But even the malware risk pales in comparison to the privacy threat. The Wacatac program jeopardizes your personal and financial details. It has instructions to spy on you, from day one. Once it settles, it starts to track your browsing habits. It monitors every move you make, and records it, too. The Trojan has access to all manner of private data. After it deems it has stolen enough information, it exposes it. It hands it over to the cyber criminals, responsible for its release. Unknown individuals with malicious intentions. Not people, you can or should trust with such sensitive data. Don’t let them have it. Protect yourself, and your system. Find and delete the Wacatac Trojan at once. The sooner it leaves your PC, the better.
Manual Wacatac Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The Wacatac infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Wacatac infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down Wacatac related processes in the computer memory
STEP 2: Locate Wacatac startup location
STEP 3: Delete Wacatac traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down Wacatac related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Wacatac startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Wacatac virus from the windows registry
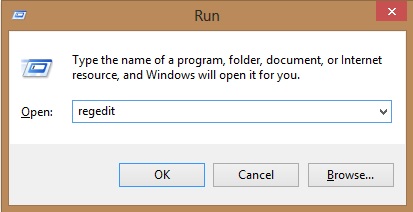
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
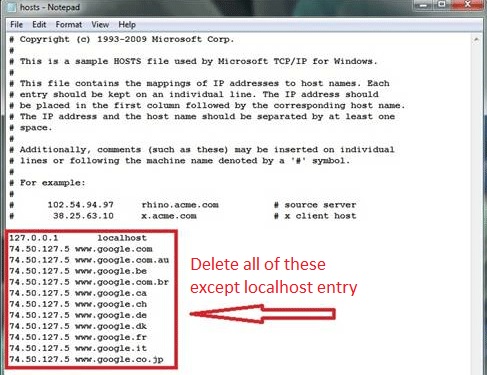
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by Wacatac
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Wacatac, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Wacatac Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.