Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Writehere@qq.com Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
all your data has Been a locked us
You want to return statement?
write email writehere@qq.com
There’s another ransomware, roaming the web, and plaguing users. It goes by the name Writehere@qq.com. And, that has to do with the extension you get stuck with, after it strikes. Let’s explain. The ransomware is a new Dharma variant. It invades via trickery, then, corruption ensues. It uses cryptography algorithms to lock your files. Yes, it locks every single file, you have. Pictures, videos, music, documents. Everything falls under its grip. After the tool’s done with the encryption process, you find your files renamed. The tool attaches the ‘.id-.[writehere@qq.com].btc’ extension at the end of each one. After that’s in place, you can no longer open them. They get rendered inaccessible. You can try to rename or move them, but it’s futile. They’re beyond your reach. The only way to change that, and unlock them, is compliance. Here’s the thing. The ransomware blackmails you. It targets your data, then extorts you for monetary gain. It demands you pay a ransom for the decryption of your files. Supposedly, if you do, you’ll remove the encryption. The key word here is ‘supposedly.’ You cannot trust the promises of cyber criminals. So, don’t. They will break their word, and double-cross you. Don’t place your faith onto extortionists. You’ll get disappointed.
How did I get infected with?
Ransomware tools are sneaky. So, is the Writehere@qq.com one. It slips by you, unnoticed. Then, wreaks havoc on your PC. The infection preys on your carelessness, and invades undetected. That’s why, it’s imperative you NOT provide it. Don’t rush, and rely on luck. Don’t give into distraction and gullibility. Don’t leave your fate to chance! Always take the time to do your due diligence. Vigilance can save you a ton of troubles. The lack thereof does the opposite. Make the right choice. When allowing anything, off the web, into your PC, be thorough. Read terms and conditions. Double-check everything. Look for the fine print. Know what you say YES to. Attention helps to catch infections in the act of attempting invasion. Attention helps you to keep them out. Be extra attentive, and don’t allow threats, like ransomware to slip by you. The invasive methods, the tool tends to turn to, include the usual. Hiding behind spam emails, freeware, fake updates, corrupted links, or torrents. The list is extensive. But remember! Choose caution over carelessness. One helps to keep a PC free of threats. The other invites them in.
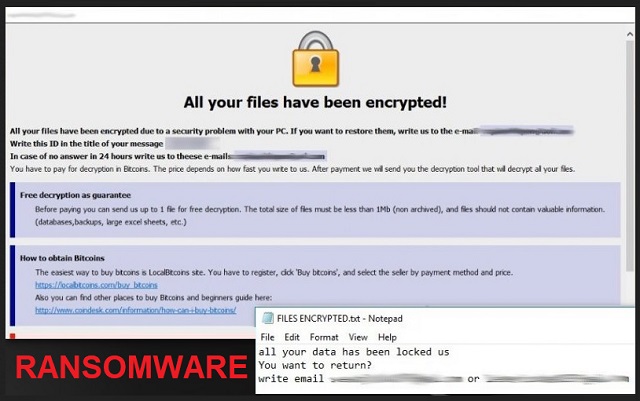
Why is Writehere@qq.com dangerous?
After the Writehere@qq.com ransomware, strikes, you face a choice. To comply or not. Heed experts’ advice, and don’t! Compliance only furthers your grievances. It leads you to lose money, and has the same outcome as not complying. Confused? Let’s explain. Once the encryption process finishes, the tool leaves you a note. A ransom note. It’s a text file that appears on your Desktop. And, it goes by the name FILES ENCRYPTED.txt. It’s brief, and it urges you to contact the cyber criminals via email. The one, you find appended at the end of each encrypted file. After you reach you to them, they’ll give you further instructions. Do not follow them! Don’t even reach out in the first place. Understand that compliance brings no positives your way. Let’s examine your possibilities, shall we? Say, you choose to everything, the infection asks of you. You write the email, pay the ransom, and then what? Well, you wait for these people to fulfill their promise. You wait to get the decryption key that unlocks your files. But what if you don’t get it? What if they don’t send you one? Your data remains locked, and you have less money at your disposal. And, even if you do get a decryption key, don’t rejoice just yet. It can prove to be the wrong one. The extortionists can send you one that doesn’t work. And, again, you have less money, and encrypted files. What’s your best-case scenario? Pay up, get the key, apply it, and free your files? Well, even if that does happen, you’re not in the clear. Think about it. You paid money to remove a symptom. The infection, that forces it on you, remains. The ransomware is free to strike again. And, put you back to square one, with less money and locked files. No matter how you look at it, the risk isn’t justified. Don’t take chances. Not to mention, the ransom amount is formidable. It’s usually in Bitcoin. And, 1 Bitcoin fluctuates around 1000 US Dollars. And, you can get charged up to 5 Bitcoins. Sometimes, it’s even more than that. Remember! Don’t pay these people. Don’t reach to them. Don’t take chances. It’s a tough call to make, but it’s the right one.
Writehere@qq.com Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Writehere@qq.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Writehere@qq.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Writehere@qq.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


