Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
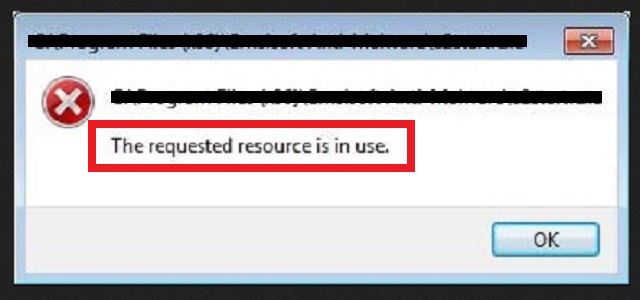
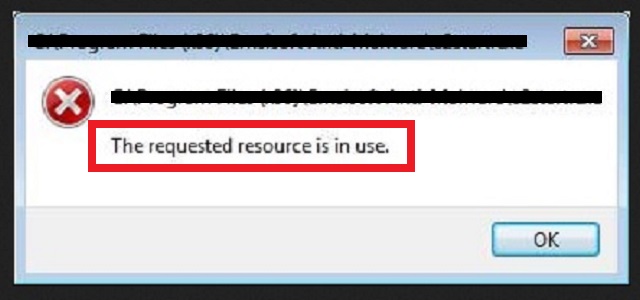
“The requested resource is in use” just keeps popping up and you cannot remove it?
You turn on your PC, and decide to use a certain program. You open that program, and lo and behold. You get greeted with the “The requested resource is in use” error message. You open a different one, and it’s the same thing. Every program you attempt to use cuts you off with the same pop-up alert. Naturally, after the fifth failed attempt to open anything, you begin to panic. That’s exactly what the infection, you’re stuck with, hopes to happen. It does its best to get you into a frenzy. Because it’s easier to exploit you in your panicked state. Don’t make it easier for infections to take advantage of you. If you face such a warning, take a step back, and examine the situation. Take the “The requested resource is in use” alert with a grain of salt. That way, you’ll see that it got forced on you because of a Trojan. Don’t fall for the trap, it lays out for you. Be smart, and keep your cool. Realize that the error pop-up appears only because a Trojan made it so. Then, do your best to locate the Trojan’s hiding place on your computer. And, then, delete it upon discovery. The sooner you remove the infection, the better. Not only will the pop-up alerts cease, but you’ll also avoid a variety of grievances. Find and remove the Trojan menace ASAP. It’s the best course of action you can take after the surprise of the “The requested resource is in use” error.
How did I get infected with?
“The requested resource is in use” alert message appears in case of a Trojan invasion. And, Trojans don’t appear out of thin air. So, how do you imagine one got into your system? If your answer isn’t “Because I agreed to install it,” you’re wrong. These types of tools have to ask the user whether they can install themselves. And, if they don’t receive an affirmative response, no admission. In other words, it sought your permission. And, you gave it. Otherwise, you wouldn’t get shadowed by the pop-up alert every time you attempt to open a program. You may not remember the exchange, but it did take place. Odds are, the Trojan succeeded with its infiltration due to your carelessness. Most, if not all cyber threats, prey on it for success. Think about it. If you’re vigilant and thorough enough, chances are, you’ll catch the tool in the act of sneaking in. And, stop it. But if you throw caution to the wind, and rush, the odds switch. All the methods of invasion, Trojan use, rely on your distraction, haste, and naivety. Spam email attachments, corrupted sites, fake updates, freeware. None can succeed without your carelessness. So, do your best NOT to grant it. Instead, try to be extra attentive. Sometimes, even a little more attention, when installing tools or updates, goes a long way.
Why is this dangerous?
The “The requested resource is in use” pop-up hinders your every move. It trips you every way possible. It doesn’t allow you to open a single program. Especially, a security or antivirus type one. It, thus, ensures its extended stay on your PC. And, you best believe, the more it remains, the worse your predicament gets. The Trojan that’s forcing the warning on you is an utter plague. These types of tools are not to get messed with. They’re a threat to both you, and your system. Don’t make the mistake of underestimating them. Instead, do yourself a favor, and act against them ASAP. The Trojan that throws the alert your way, also throws countless problems at you. It messes up your browsing experience. Each time you open your browser, you get redirected and flooded with pop-up ads. These constant disruptions don’t go unnoticed, and cause consequences of their own. Your computer slows down to a crawl. Your system starts to crash all the time. It’s a nightmarish experience. But, that’s the least of your concerns. Those are the ‘surface issues,’ you encounter. The minor inconveniences, the Trojan causes. There are much worse ones. The absolute worst of which is the security threat. Yes, the infection places your privacy in jeopardy. It’s designed to spy on you from the moment it invades. So, you’re in danger even before the “ The requested resource is in use” pop-ups commence. The tool keeps track of your online activities, and records them. After it deems it has gathered enough data, it sends it. It hands it over to the third parties behind it. Strangers will then have access to your personal and financial details. Do you think that ends well for you? Cyber criminals getting a hold of your private life? Don’t take such unnecessary risks. Do yourself a favor, and act against the Trojan ASAP. Find and delete it as soon as it first displays the error message. “The requested resource is in use” is a warning. It warns you’re in danger if you don’t act immediately. Heed the warning, and act. You won’t regret it. You WILL regret inaction.
Manual “The requested resource is in use” Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 2: Windows 7/XP/Vista Removal
STEP 1: Start Your Computer into Safe Mode with Networking in Windows 8
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Move the mouse to the upper right corner until the windows 8 charm menu appears
- Click on the magnifying glass
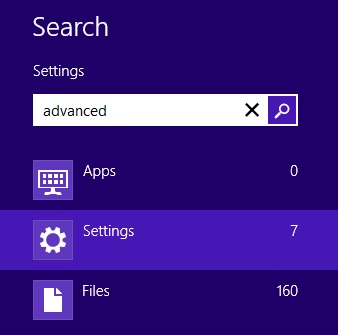
- select Settings
- in the search box type Advanced
- On the left the following should appear
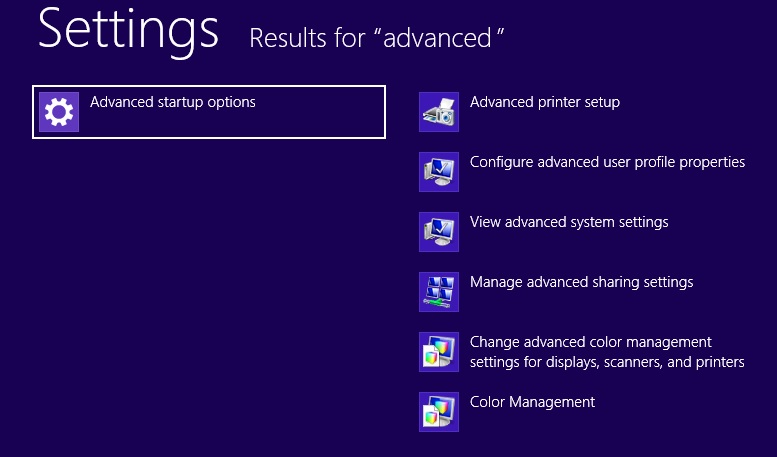
- Click on Advanced Startup Options
- Scroll down a little bit and click on Restart Now
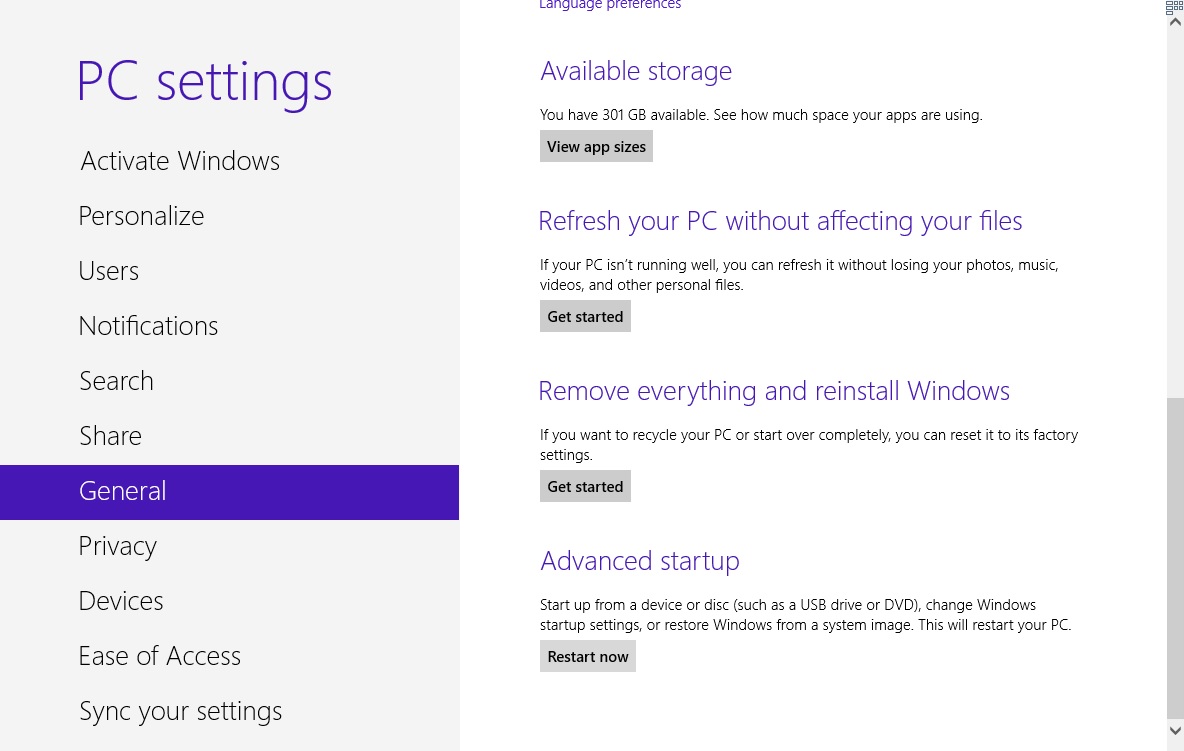
- Click on Troubleshoot
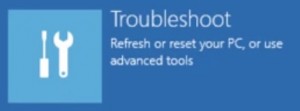
- Then Advanced options

- Then Startup settings

- Then Restart
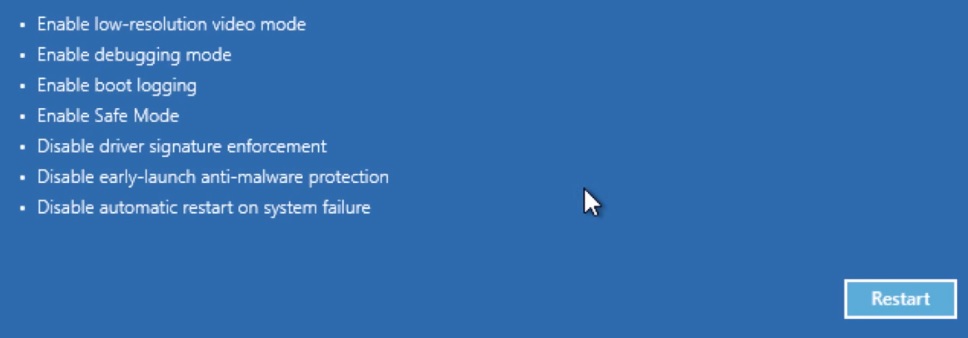
- When you see this screen press F5 – Enable Safe Mode with Networking

STEP 2: Start Your Computer into Safe Mode with Networking in Windows 7/XP/Vista
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.
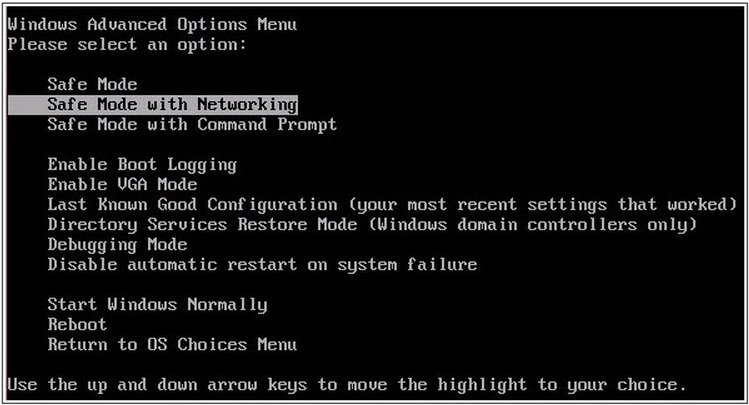
STEP 3: Locate the startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: backgroundcontainer

- Then open your explorer and navigate to:
%LocalAppData%\uqgtmedia
where %LocalAppData% refers to:
C:\Users\{username}\AppData\Local
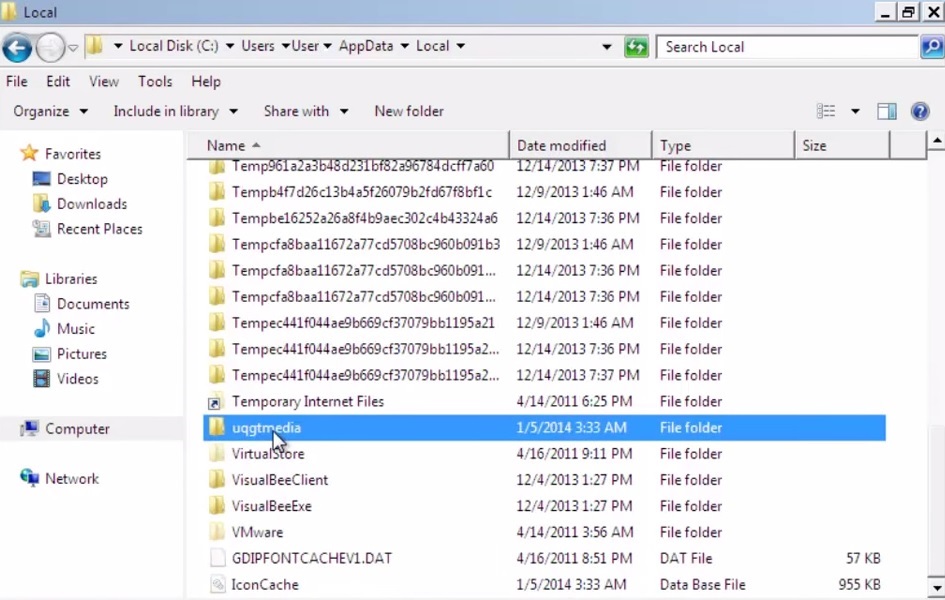
- delete the whole folder
Double check with any antimalware program for any leftovers. Keep your software up-to date.