Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
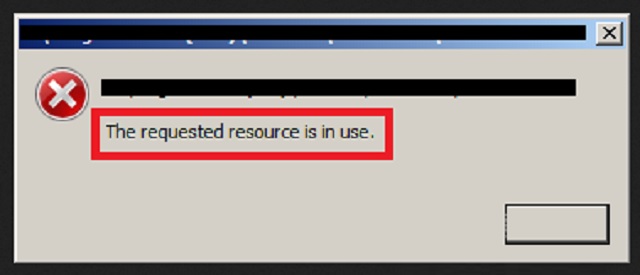
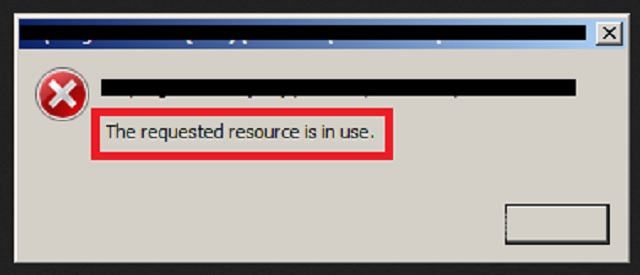
“The requested resource is in use” just keeps popping up and you cannot remove it?
The only reason why you’re now dealing with these errors is a Trojan horse. Unfortunately, Trojans are among the most dangerous types of malware online. You’ve downloaded quite a problematic infection. And the sooner you take measures, the better. Trojans are rightfully dreaded programs. Not only do the wreak havoc but they also do so in complete and utter silence. That means the virus may spend a good while on your machine with you having no idea about it. As you could imagine, the Trojan will use all that time to cause you problems. Eventually, this infection could bring along some irreversible damage. Are you willing to allow this nuisance to harass you? You’re playing a game that you simply cannot win. As soon as you encounter the parasite’s presence, you have to uninstall it. What makes this parasite so dangerous? For starters, it gets installed behind your back. The virus relies on stealthy techniques and leaves you oblivious to its malicious presence. After installation, this program goes after your default computer settings. Your system registry gets modified and, once again, your authorization remains irrelevant. After all, you have an infection on your computer system. It isn’t on board to help you browse the Internet. The Trojan is only part of your life to help its developers gain profit. Some important system files may get altered. Others may get damaged. Therefore, don’t be surprised when you end up unable to run several programs. Thank the Trojan for that. In addition, this infection could make changes in your browser settings. In this scenario, you will be bombarded with a never-ending parade of sponsored pop-up ads. By injecting your browsers with commercials, the Trojan helps hackers gain even more revenue at your expense. The question is, are you really trying to help cyber criminals make money? Every single cent they gain will be used to create more parasites. Also, their profit ultimately comes at your expense. Due to the Trojan horse’s presence, you’re one click away from more infections. The pop-ups, commercials and other ads this program displays are all unsafe. Some of them lead straight to harmful websites full of malware. And no, that’s not all. This program leads to a poor PC performance. It causes your machine to often freeze/crash and makes your Internet connection unstable. Apart from that, the Trojan serves as a back door to more viruses and even spies on your private information. That means you’re practically jeopardizing both your safety and privacy by keeping this pest on board.
How did I get infected with?
The virus is more than capable of causing you serious issues. Next time you browse the Internet, be careful in advance. There are plenty of similar infections out there so watch out for potential threats. It is much easier to prevent infiltration than to remove malware. To protect your PC in the future, stay away from illegitimate websites and unverified pages. More often than not, those hide numerous infections. You only need one single moment of negligence to download viruses. Remember to pay attention online instead of rushing. Avoid opening spam messages or email-attachments. This is actually one of the most popular malware infiltration techniques at the moment. The Trojan could pretend to be a legitimate email from a shipping company or a job application. Instead of rushing to click such a questionable email open, delete it. Note that infections mainly rely on stealthy, secretive methods to get spread on the Web. It is entirely your responsibility to prevent virus installation. Trojans also use fake third-party ads, fake torrents and fake software updates to get installed. Long story short, you have to be very cautious online.
Why is this dangerous?
The Trojan makes modifications behind your back. It sneakily changes your PC settings and exposes you to threats. As mentioned already, this program serves hackers’ purposes. It might inject your browsers with sponsored pop-up ads. It could also redirect you to dangerous websites thus destroying your whole online experience. What’s much worse than that is the fact this pest steals private data. It collects IP addresses, usernames, usernames, passwords, email addresses. In addition, the Trojan horse may go one step further. Apart from your browsing-related data, this infection may get to some personally identifiable details. Bank account information, for instance. You can see for yourself how dangerous such a trick is. To top it all, hackers could gain remote control over your computer. Please follow our detailed manual removal guide down below.
Manual “The requested resource is in use” Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 2: Windows 7/XP/Vista Removal
STEP 1: Start Your Computer into Safe Mode with Networking in Windows 8
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Move the mouse to the upper right corner until the windows 8 charm menu appears
- Click on the magnifying glass
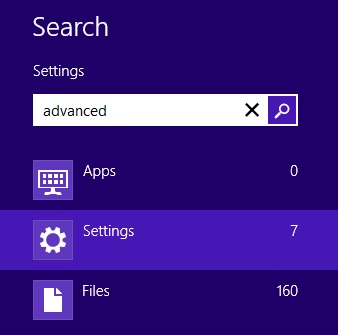
- select Settings
- in the search box type Advanced
- On the left the following should appear
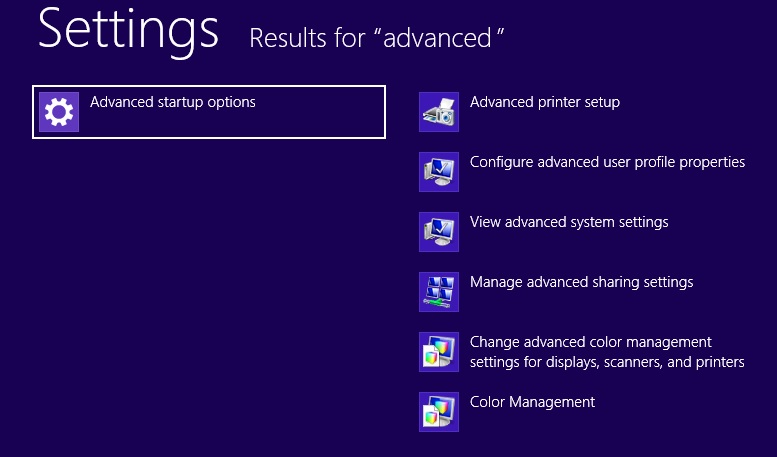
- Click on Advanced Startup Options
- Scroll down a little bit and click on Restart Now
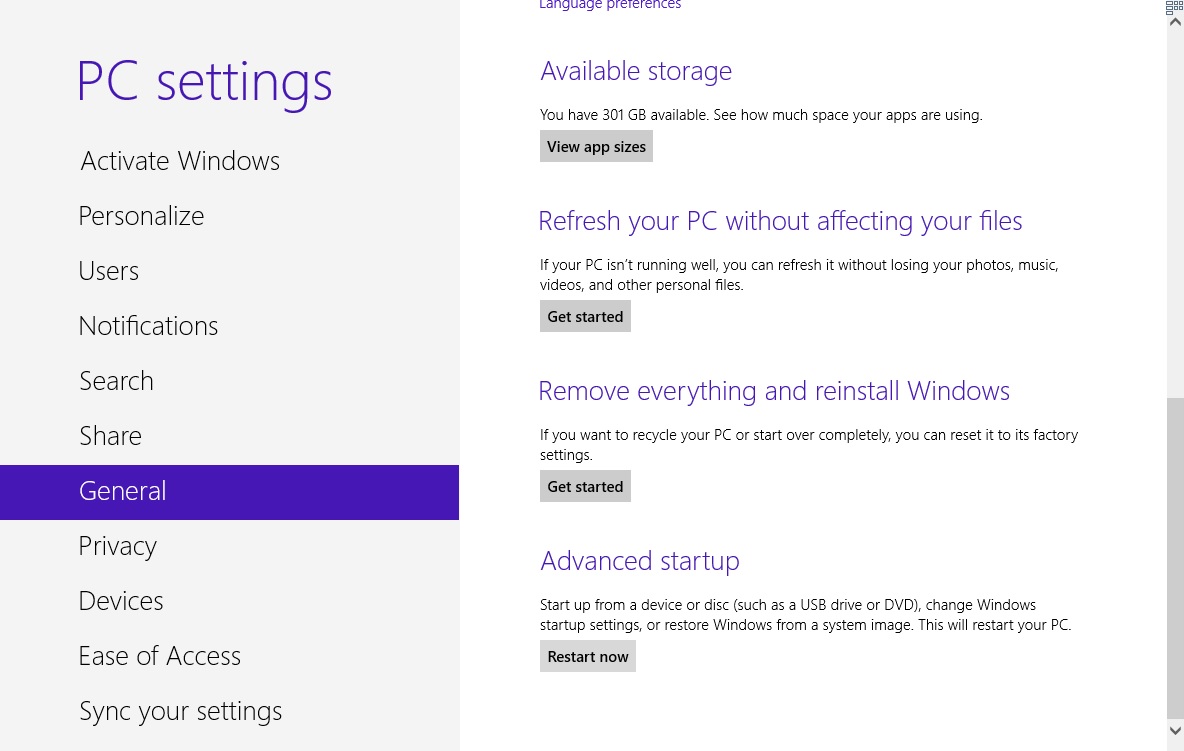
- Click on Troubleshoot
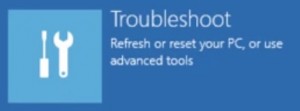
- Then Advanced options

- Then Startup settings

- Then Restart
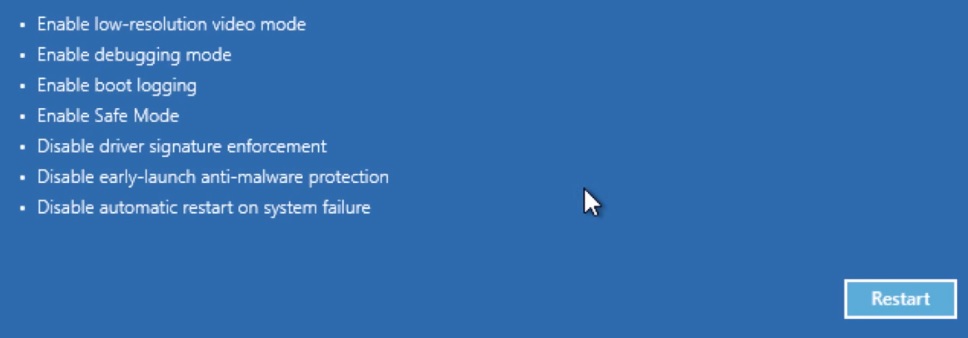
- When you see this screen press F5 – Enable Safe Mode with Networking

STEP 2: Start Your Computer into Safe Mode with Networking in Windows 7/XP/Vista
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
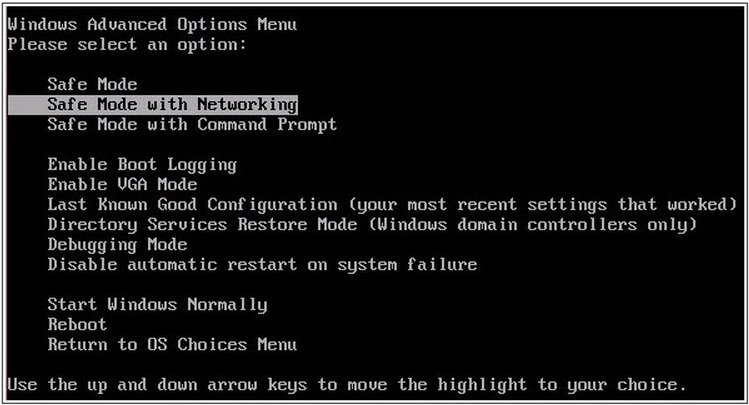
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.
STEP 3: Locate the startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: backgroundcontainer

- Then open your explorer and navigate to:
%LocalAppData%\uqgtmedia
where %LocalAppData% refers to:
C:\Users\{username}\AppData\Local
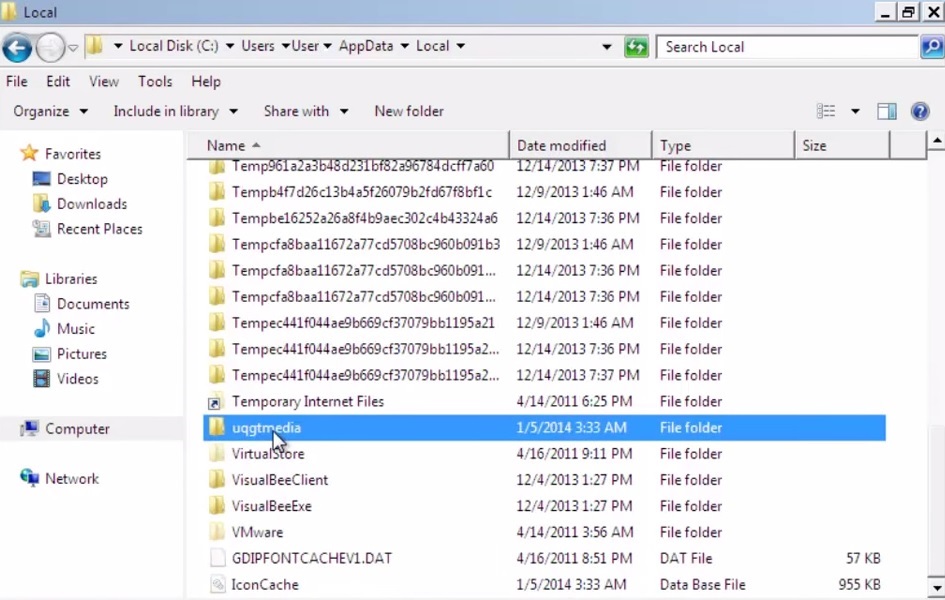
- delete the whole folder
Double check with any antimalware program for any leftovers. Keep your software up-to date.