Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Revenge Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
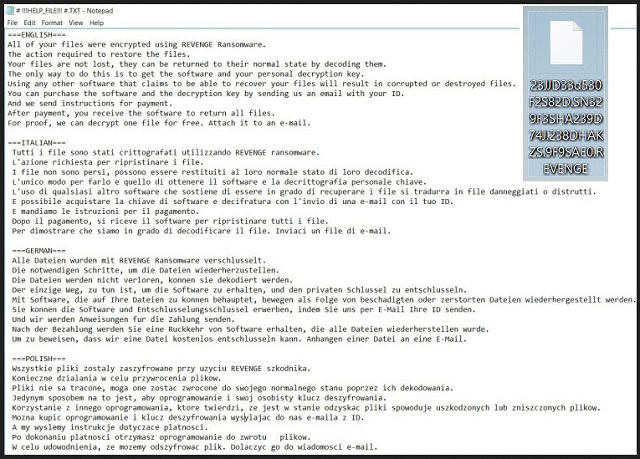
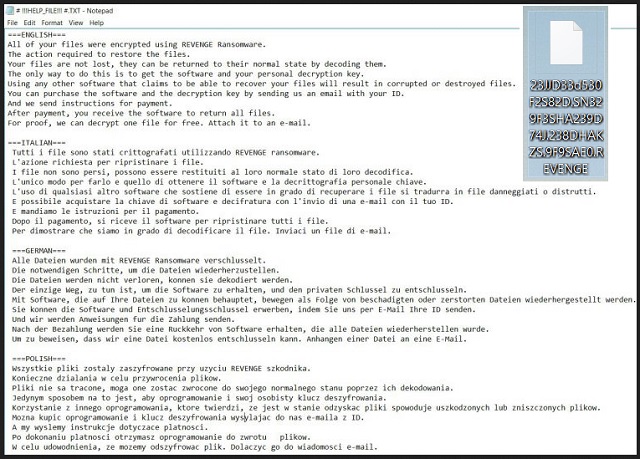
===ENGLISH===
All of your files were encrypted using REVENGE Ransomware.
The action required to restore the files.
Your files are not lost, they can be returned to their normal state by decoding them.
The only way to do this is to get the software and your personal decryption key.
Using any other software that claims to be able to recover your files will result in corrupted or destroyed files.
You can purchase the software and the decryption key by sending us an email with your ID.
And we send instructions for payment .
After payment, you receive the software to return all files.
For proof, we can decrypt one file for free. Attach it to an e-mail.
Revenge is the astonishing name of a new ransomware infection. The tool may be a new-found member of the ransomware family, but it represents an old threat. Revenge is an updated version of the CryptoMix tool. Its programming is rather standard. The infection slithers into your PC, and takes control of your data. It encrypts every single file you have, using AES-256 cryptography. The tool attaches a special extension at the end of each file. Thus, solidifying its grip over your files. Imagine turning on your PC, and getting greeted with a ransom message on your Desktop. Then, seeing your files encrypted, and that you cannot open them. Revenge tends to lock them via the “[32_random_characters].REVENGE”pattern. It’s quite startling to come to that one day. And, that’s the point. The ransomware wants you startled. It wants you to panic. When you get into a panicked state, it’s easier to act without thinking it through. And, you may act against your best interests. That’s the end-goal of all ransomware, including the Revenge tool. It wants you to fear you’ll lose your files, and do whatever it asks of you for the prospect of getting them back. The program leaves a ransom note. It explains your predicament, and provides instructions. It’s a TXT file, called “# !!!HELP_FILE!!! #.txt” And, it’s multilingual. It has the same text, written in Korean, Italian, German, Polish, and English. The infection expects you to contact the people behind it via email. It even provides you with three addresses. Once you get a hold of them, they’ll send you further instructions on how you must proceed. That is, if you want to free your files from Revenge’s keep. And, here’s the thing. Experts advise against compliance. Do NOT pay the ransom, these people ask of you. Do NOT even contact them. Do nothing. Do NOT follow a single demand, it lays out. To comply is to set yourself up for an even worse experience. So, make the right but difficult choice, and discard your data. It’s a tough decision to make, but you’ll be glad you made it in the future.
How did I get infected with?
Revenge turns to the usual antics to slither into your system. The tool uses the old but gold means of infiltration. There’s an entire array of methods, it can choose from. But do you know what? Although, they are different from one another, they have one thing in common. They all need a crucial ingredient to succeed. Neither one can work without your carelessness. For the infection to access to your PC, you have to be careless enough to allow it. It needs you to throw caution to the wind, and give into naivety. It needs you in a rush. Why make it easy for a cyber plague to access your PC? Do yourself a favor, and choose caution over carelessness. One keeps infections away, while the other invites them in. Make the smart choice. Always take the time to read the terms and conditions when installing updates. Or, when you’re dealing with freeware. Understand that due diligence goes a long way. Sometimes even a little extra attention today can save you a ton of troubles tomorrow. Be smart, and be thorough. Choose vigilance.
Why is Revenge dangerous?
We said it once, and we’ll say it again. Do NOT comply with the ransomware’s demands. Compliance only worsens your predicament. And, here’s why. Let’s go over the possible scenarios of how the situation can unfold. So, Revenge creeps into your system, and takes over. It encrypts your data, and demands payment for their release. The question is, do you go through with it? Do you pay these people for the decryption key that unlocks your files. Supposedly, upon receiving your transfer, they send you the needed key. The most important word here being ‘supposedly.’ What if they don’t send you one? Or, do send it, but it doesn’t work? And, even if it works and frees your files, what then? Think about it. The decryption key decrypts your data. It does nothing for the infection itself. The Revenge tool still remains. What’s to stop the program from acting up again, and locking your files once more? The answer is nothing. Nothing is stopping you. You have zero guarantees that after paying up the ransom, it will be the last time you have to deal with Revenge. It can strike at any given moment. An hour after decryption. A day, a week, ten minutes. Revenge takes over, and then what? You’re back to square one. Only this time, you have less money. And, what’s worse, an exposed private life. Oh, yes. The cyber kidnappers behind Revenge, have access to your privacy. Think about it. When you pay the ransom, they request, you provide private information. Information, which these strangers can then use as they see fit. Ask yourself. Are you okay with extortionists getting a hold of your personal and financial data? Especially, when you have zero to little actual prospects of getting back your data. Cut your losses, and pick the lesser evil. Forsake your files in the name of your privacy. It’s a tough choice to make. But it’s the right one.
Revenge Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Revenge Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Revenge encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Revenge encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.