Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Goldeneye Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
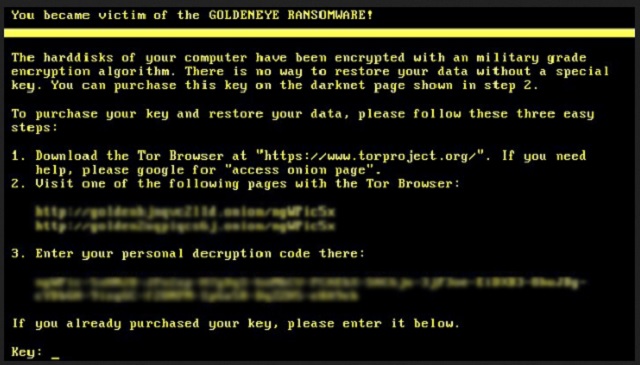
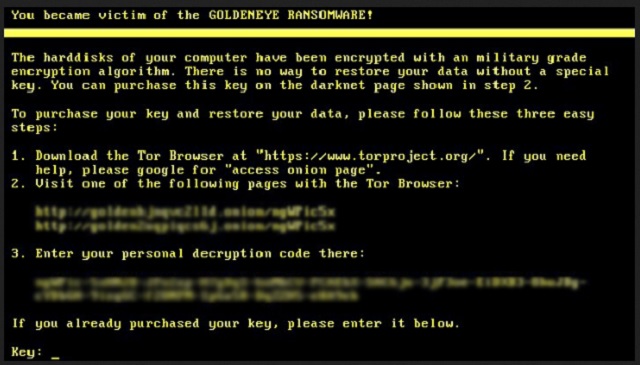
The hardisks of your computer have been encrypted with an military grade encryption algorithm. There is no way to restore your data without a special key. You can purchase this key on the darknet page shown in step 2.
To purchase your key and restore your data, please follow these three easy steps:
1. Download Tor Browser . If you need help please google for “access onion page”.
2. Visit one of the following pages with the Tor browser :
[page link] [page link] 3. Enter your personal decryption code there:
[address]
If you already purchased your key, please enter it below.
Key:
No, we’re not talking about the James Bond movie. Thanks to hackers, the name GoldenEye now means something entirely different. This infection has been brought to you by the developers of Petya and Mischa Ransomware. Obviously, the three parasites share some great similarities. So far it seems Goldeneye’s main target are German PC users. The parasite was firstly detected on December 6, 2016. You see, ransomware is on the rise right now. We come across new infections or new versions of old ones practically every day. Hence, the appearance of Goldeneye isn’t particularly surprising. What’s surprising, though, is how dangerous this virus is. You’re dealing with ransomware. That sentence alone should make it very clear for you how bad things are. The Goldeneye Virus gets activated as soon as it lands on board. Its shenanigans start with a throughout scan of your computer. Just like all other ransomware-type infections, this one is searching for your files. Once it finds them, encryption begins. Goldeneye uses a complicated algorithm to lock all your data. This pest takes down pictures, videos, music, documents. Anything of value it locates, the parasite encrypts. How does the encryption process work? The ransomware copies your files and deletes the originals. What it leaves you with are the encrypted, unusable copies. Goldeneye adds a random combination of 8 symbols at the end of your files’ names. Seeing this malicious extension means the virus has already locked your files. You might be able to stop the process if you notice that your PC is getting sluggish. This could be a sign a ransomware-type infection is encrypting your information. Unfortunately, most people see the threat when it’s too late. While locking your data, Goldeneye creates .txt, .bmp or .html files. Those are your payment instructions. The virus creates them in all folders which contain encrypted information. As we mentioned, Goldeneye modifies a huge variety of formats. Therefore, you’ll find a ransom message in almost every folder you have. According to crooks’ instructions, you have to make a payment. They demand 1.3 Bitcoins which equals 983 USD at the moment. In exchange for your money, you’re supposed to receive a decryptor and free your data. However, you will not. This is all part of a clever cyber scam which aims at your bank account. Unless you’re willing to make a bad situation worse, tackle the intruder now.
How did I get infected with?
This parasite travels the Web in spam emails. If you stumble across a bizarre email-attachment named Bewerbung, beware. That’s Goldeneye. Clicking a corrupted email or message open lets the parasite loose. You end up jeopardizing your own security. Keep in mind that infections often pretend to be job applications or resumes. Malare could also be disguised as legitimate emails from some shipping company. Be very careful what you click open as it might contain a virus. Now that you know how devastating ransomware is, do you want to deal with it again? Having this experience once is enough. Watch out for malicious torrents, websites, fake software updates, third-party pop-ups. In addition, Goldeneye might have sneaked in with the help of a Trojan horse. Check out the PC for more parasites. Last but not least, stay away from unverified freeware and shareware bundles. You must be completely aware what enters your machine and what does not. Take care of your device and save yourself a headache. Prevention is a lot easier than having to remove malware afterwards.
Why is Goldeneye dangerous?
The Goldeneye Ransomware is extremely problematic. This nasty piece of malware keeps your files hostage. You can no longer view or open or use your own data in any way. It goes without saying how much damage such a trick could cause you. It is highly recommended to have backups of your precious files in case ransomware gets to you. As we mentioned, Goldeneye utilizes a strong encrypting algorithm to lock your data. It adds a random extension which is a clear sign the computer has been compromised. Furthermore, hackers are impudent enough to ask for almost 1000 dollars. Think about it. Those are the people who encrypted your files in the first place. Every single cent they gain will be used to develop more infections. Paying the money wouldn’t guarantee you a decryption key. It would only guarantee that you’d become a sponsor of greedy cyber criminals. Hesitate no more; Goldeneye is trying to involve you in a fraud. To delete the virus manually, please follow our detailed removal guide down below.
Goldeneye Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Goldeneye Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Goldeneye encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Goldeneye encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.