Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Petrwrap Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
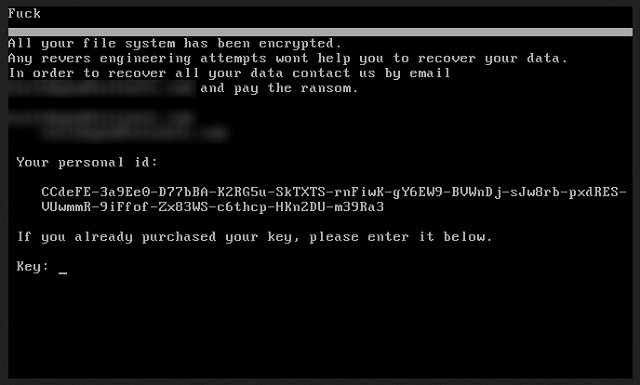
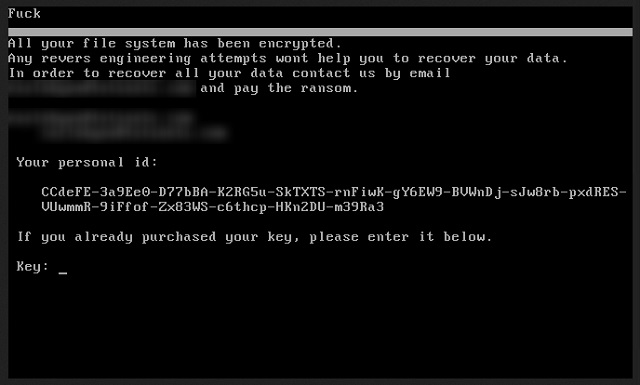
F***
All your file system has been encrypted.
Any reverse engineering attempts wont help you to recover your data.
In order to recover all your data contact us by email
XXXXXXXXXXXXXXXXX and pay the ransom.
Your personal id:
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
If you already purchased your key, please enter it below.
Key: ….
Remember the Petya ransomware scare? Well, get ready for an encore! There’s a new player on the field, going by the name Petrwrap. And, it’s pretty much a revamped version of Petya. Ransomware infections are considered the worst. That’s a notoriety, they’ve earned. Not only do they wreck your system, and place your privacy in jeopardy. As is the case with most cyber threats. But they take it up a notch, and also keep your data hostage. And, in all likelihood, you never see your files again. That’s right. Once Petrwrap invades your system, it corrupts it. The tool locks every single file you have. Say goodbye to photos, documents, music, videos. All falls under its grip. And, once the infection has control over your data, it makes demands. It leaves you a ransom note that states a pretty standard threat. “Pay us or lose your data.” And, put like that, of course, you lean towards paying. But, hear us out when we say, do NOT do that! To pay these people is to put yourself in even more danger. Don’t do it. It’s tough, but the best course of action, you can take in that situation, is to let go of your files. Forsake them, and move on. Files are replaceable. Losing them is a far better alternative to what awaits you if you choose to comply. Following cyber criminals’ commands is never a good thing. You won’t enjoy the outcome.
How did I get infected with?
Petrwrap is not particularly innovative when it comes to infiltrating your system. The tool turns to the old but gold methods. Above all others, it most often uses freeware. It provides the perfect opportunity for a sly and sneaky invasion. How come? Well, most users aren’t cautious when installing freeware. They rush, and rely on luck. Instead of being thorough, they give into naivety. Most, don’t even bother to read the terms and conditions. They prefer to head straight for the YES, and hope for the best. Well, hope does not bring you “the best.” It brings infections. Understand that carelessness opens your system to cyber threats. Caution, on the other hands, helps to keep them out. Always choose vigilance. Take the time to do your due diligence. You’ll see it goes a long way.
Why is Petrwrap dangerous?
As stated, Petrwrap is the polished version of Petya. And, it’s as untrustworthy and unreliable. You cannot hold the cyber extortionists to their word. So, don’t expect them to keep it. They will not. What they will do, is double-cross you. There are a dozen different ways they can dupe you. Let’s examine how your best-case scenario unfolds, when stuck with a ransomware. So, you find your data locked, encrypted with a special algorithm. You find the ransom note, and discover you can unlock them if you pay up. So, you decide to do it. You transfer the requested amount. Then, you wait for what was promised to you. The decryption key to apply and free your files. You receive it, and it works. Your files get decrypted. But, then what? The key, that you gave money for, removes the encryption. It does nothing for the infection itself. Petrwrap still lurks somewhere in the corners of your system. Ask yourself. What stops it from striking again? The answer is nothing. The ransomware can act up 5 minutes after you decrypted your data. An hour, a day, a week, a month, whenever it so chooses. Then, you’re back to square one. Only this time, you have less money. And, what’s worse, an exposed privacy. Oh, yes. When you pay the ransom, you provide private information. You leave personal and financial details. The cyber kidnappers can then access and exploit that information for their benefits. Do you think that ends well for you? Don’t be naive. Protect yourself. Forsake your files in the name of your private life. And, remember. That’s your BEST-case scenario. The extortionists can decide to break their promise, and not send you a decryption key. Or, send a wrong one. The most important thing is, these are people, who WILL not go through on their end of the deal. The fight against ransomware is one, you cannot win. So, don’t play. Discard your data.
Petrwrap Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Petrwrap Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Petrwrap encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Petrwrap encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.