Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove CERBER 4.0.3 Ransomware?
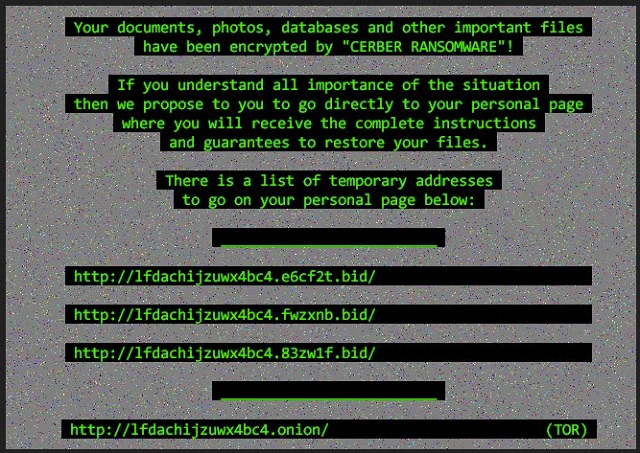
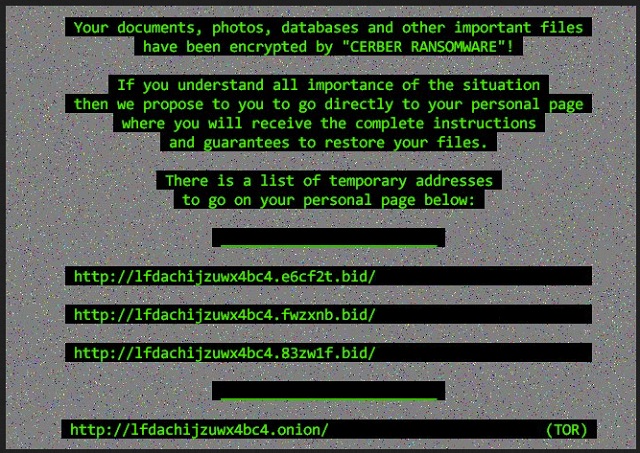
Readers recently started to report the following message being displayed when they boot their computer:
C_E_R_B_E_R R_A_N_S_O_M_W_A_R_E
#############################################################
C_E_R_B_E_R_R_A_N_S_O_M_W_A_R_E
Cannot you find the files you need?
Is the content of the files that you looked for not readable???
It is normal because the files’ names, as well as the data in your files
have been encrypted.
Great!
You have turned to be a part of a big community “#Cerb3r Ransomware”.
Cerber is known as one of the most virulent infections online. And, this is a well-deserved title. Today’s article is all about Cerber’s latest version. As you could imagine, the dreaded CERBER 4.0.3 is just as dangerous as its cyber ancestors. You’re currently attacked by a file-encrypting program. Ransomware is notoriously problematic so, to say the least, you’re in for trouble. As soon as the virus sneaks itself on board, it starts harassing you. CERBER 4.0.3 overall follows the classic ransomware pattern. Also, you should know the Web is full of ransomware parasites at the moment. Hackers seem to be quite interested in these infections. Do you know why? Because ransomware allows its developers to gain easy, illegal profit online. To become rich without any effort is every cyber criminal’s dream. Thus, ransomware’s popularity is steadily growing. We come across a brand new file-encrypting virus almost every day. Just like all programs of this kind, CERBER 4.0.3 firstly scans your machine. This way, it locates your personal data. The parasite goes after a huge number of formats including pictures, music, videos, documents. Long story short, all your valuable information falls victim to the virus. By using a complicated algorithm, this pest locks your files. It actually renames the target data and adds a malicious file extension. After CERBER 4.0.3 finds your pictures, music, etc., it copies them. Then the originals get deleted. You see, you’re left with the renamed, modified, encrypted files. Those are inaccessible. Your computer won’t recognize the file format so you won’t be able to open your data. Simple as that. CERBER 4.0.3 encrypts your personal files for one single reason. Most people would panic when they see such sudden, unauthorized changes. You probably got quite anxious yourself. Now, this is exactly what crooks are aiming for. Once you give into despair, you stop thinking logically. That’s an incredibly convenient time for you to get scammed. Therefore, keep in mind that ransomware is nothing but hackers’ nasty attempt to steal your money. They are messing with you. After encryption is complete, the parasite displays a ransom message. It usually gets added to all folders that contain locked files. According to that note, the only way to restore your files is by paying a sum of money in Bitcoin. The ransom varies between 0.5 Bitcoin (about 340 USD) and 1.5 Bitcoin (1020 USD). Don’t ever consider paying. Get rid of the parasite instead and don’t sponsor crooks’ illegitimate business.
How did I get infected with?
Exploit kits are among the most popular virus distribution techniques. Take for instance Neutrino, Magnitude and the RIG Exploit kit. Keep your programs up-to-date and be careful when installing updates. Infections are sneaky. Another effective technique involves spam messages and spam email-attachments. That’s right, hackers sometimes send malware straight to your inbox. All you have to do is click it open. This is how you could infect your own device with all types of malware imaginable. Take no chances. When you stumble across a suspicious-looking email, delete it. You’d save yourself quite the headache this way. Also, ransomware gets spread online with the help of Trojans. Check out your PC system for more parasites because CERBER 4.0.3 may have company. Last but not least, avoid illegitimate websites/torrents/software bundles. You should always keep in mind how tricky infections are. Pay attention to what you download and make sure you protect your safety.
Why is CERBER 4.0.3 dangerous?
You’ve managed to install one notoriously harmful type of virus. It’s no secret ransomware causes thousands of gullible PC users damage every year. To prevent getting blackmailed, do not pay the ransom. In CERBER 4.0.3’s note, you will find a web link to a TOR browser. Stay away from it. If anything, paying the money would only worsen your situation. Hackers offer you a deal – they promise a special decryptor in exchange for your Bitcoins. However, they don’t deliver. Even if for some reason you pay the entire ransom, your files will remain locked. Crooks are focused on stealing your money, not freeing your information. Hence, don’t believe their empty promises and bogus threats. This whole thing is a cyber fraud so don’t be naive. To delete the ransomware manually, please follow our removal guide down below.
CERBER 4.0.3 Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover CERBER 4.0.3 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with CERBER 4.0.3 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate CERBER 4.0.3 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.