Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Cerber Ransomware?
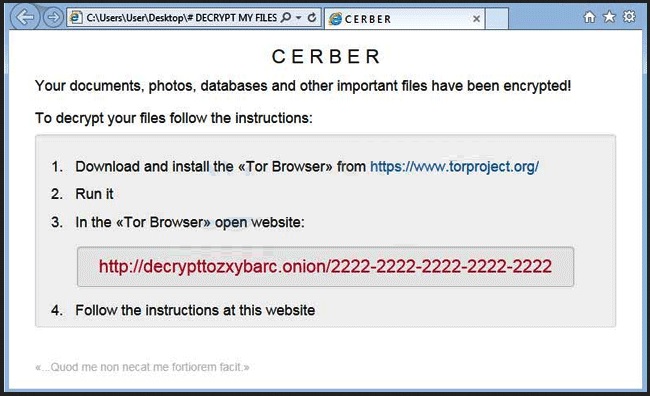
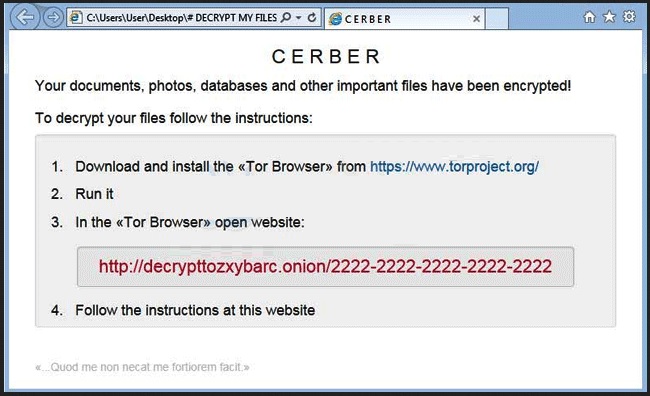
Reader recently start to report the following message being displayed when they boot their computer:
“Attention! Attention! Attention! Your documents, photos, databases and other important files have been encrypted!”
Not many PC users would remain calm and collected after seeing this message. However, the Cerber virus goes one step further by including an audio file as well. That means you’re now dealing with a particularly original, tricky and problematic ransomware parasite. Now, what is ransomware? It’s (rightfully) considered to be among the most virulent types of infections that you could possibly stumble across online. And it’s quite an unpleasant thing to have on board. As its name implies, ransomware’s ultimate goal is to trick gullible people into paying a ransom. Unfortunately, this scheme is very effective which explains the rising number of ransomware programs online. For the most part, Cerber follows the classic pattern. It invades your computer completely behind your back. Then it scans the machine thoroughly. The scan is necessary so the virus could locate your personal files (pictures, music, videos, Microsoft documents, presentations, etc.). Keep in mind that this pest is immensely resourceful so it infects a huge percentage of your data. Once the scan is complete, Cerber uses the complicated AES encrypting algorithm in order to lock your files. You will notice that a random .CERBER extension has replaced the original one. That is it. Your private information is now inaccessible. The computer cannot recognize the new file format so the PC cannot read your data. That leads us to the aggravating conclusion that you can’t use your very own files. It goes without saying that there might be some extremely important or valuable files stored on your device which are now unreadable. Yes, due to the parasite’s trickery, your own files are practically useless. While Cerber is encrypting your data, the virus also creates #DECRYPT MY FILES#.txt, #DECRYPT MY FILES#.html and #DECRYPT MY FILES#.vbs. You will find these files in every single folder that contains infected data. Why do hackers force them on you so aggressively? Because these files contain payment instructions. As you can clearly see, the entire ransomware scheme is strictly money-oriented. In addition, the Cerber parasite includes one rather rare trick – it plays the ransom message through the computer speakers as well. According to this ransom note, you only have one option if you wish to regain access to your encrypted files. And it involves money. 1.24 Bitcoin (about 500 USD), to be exact. Most ransomware parasites demand quite a hefty sum of money and Cerber is not an exception. You’re supposed to use a Tor browser and, on theory, paying the ransom will guarantee you a special decryption key. This is a unique combination of symbols which allows you to get your files back. Unfortunately, this is a scam. As we already mentioned, the one purpose that ransomware has is to blackmail PC users and, ultimately, help hackers gain illegal revenue. There is no guarantee whatsoever that crooks will keep their end of the bargain. In the absolute worst case scenario, you end up with your computer still compromised, your private files still unusable and 500 USD of your money gone. If that idea doesn’t sound too good to you, then keep on reading.
How did I get infected with?
Long story short, you’ve probably clicked something open when you should have ignored it. At the end of the day, ransomware-type viruses are still PC programs which need to be properly installed before they begin to wreak havoc. For example, the virus might have been attached to illegitimate freeware/shareware bundles that you were careless enough to download off of the Web. Another possibility is that you opened some spam email message from a known/unknown sender or some spam email-attachment. According to some researchers, Cerber gets spread online via an underground Russian forum. To avoid such nasty infections in the future, avoid suspicious-looking websites. Also, make sure you stay away from third-party commercials and questionable executables. Keep in mind that the Web is infested with malware; it’s your responsibility and yours only to take care of your PC on time. It goes without saying that it’s much easier to prevent virus infiltration that to uninstall a parasite later on. Also, keep in mind that your caution online always pays off.
Why is Cerber dangerous?
Ransomware in general and the Cerber virus in particular are indeed very troublesome. Once this program manages to slither itself onto your machine, consider your personal files gone. As if that wasn’t enough, its greedy developers then start playing mind games with you.
Cerber will configure itself to start automatically when start your Computer, it will also execute itself as a screensaver when your computer is idle, and set a task to execute itself once every minute. In this phase, when the ransomware is executed it will show a fake system alert and begin a restart process. Until this restart is allowed to occur, it will continue to display fake system alerts. Examples of alerts you may see include:
- you are about to be logged off – This directory server is shutting down, and cannot take ownership of new floating single-master operation roles
- you are about to be logged off – It is not permitted for an alias to refer to another alias
To become even more annoying the Cerber Virus talks to you: Attention! Attention! Attention! – Your documents, photos, databases and other important files have been encrypted!
This is why it’s extremely important that you ignore Cerber’s nasty ransom demand. Don’t fall victim to such a trickery and don’t become a sponsor of cyber criminals. Keep in mind that they have no reason to actually provide you the Cerber Decryptor they originally promised. Frankly speaking, hackers were never really famous for following the rules, were they? Paying the money is not an option. Furthermore, according to the ransom message, if you don’t pay within 7 days, the ransom doubles. As you can see, this parasite puts you in an incredibly vulnerable position so restrain yourself from giving away your money. Unfortunately, Cerber is a relatively new kind of ransomware so there are still no decryption tools developed. That means at this point it’s impossible to restore your files. What you could do is get rid of the virus and make sure you never have to deal with ransomware again. To delete this pest manually, please follow the detailed removal guide that you will find down below.
Cerber Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Cerber Encrypted Files
WARNING! Stopping the wrong file or deleting the wrong registry key may damage your system irreversibly.
If you are feeling not technical enough you may use Spyhunter professional Cerber Removal Tool. However, only the Scanner is FREE, in order to remove the CERBER Files virus completely you need to purchase full version. >>Download SpyHunter – a professional .Cerber scanner and remover.
>>Download SpyHunter – a professional .Cerber scanner and remover.
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware.
- This particular infection will be located in %AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\ folder and name itself with a random Windows executable.
- Before you kill the process, type the name on a text document for later reference and to be able to delete it.

- Locate any suspicious processes associated with Cerber encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Cerber encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
HKCU\Control Panel\Desktop\SCRNSAVE.EXE “%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe” HKCU\Software\Microsoft\Command Processor\AutoRun “%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe” HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run “%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe” HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random] “%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe” HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\[random] “%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe”
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
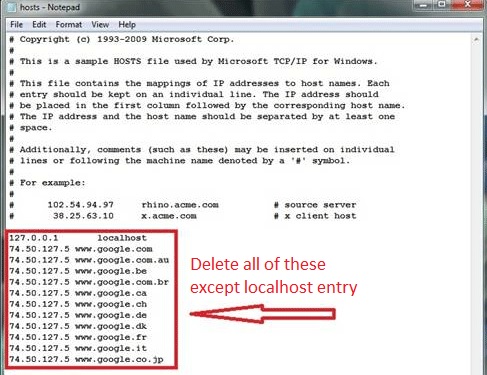
If you are uncertain about the IPs below “Localhost” contact us in out google+ profile and we will try to help you.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.