Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Globe Ransomware?
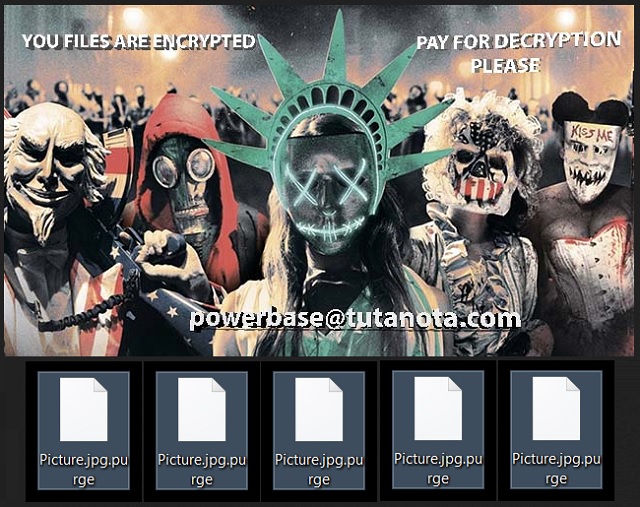
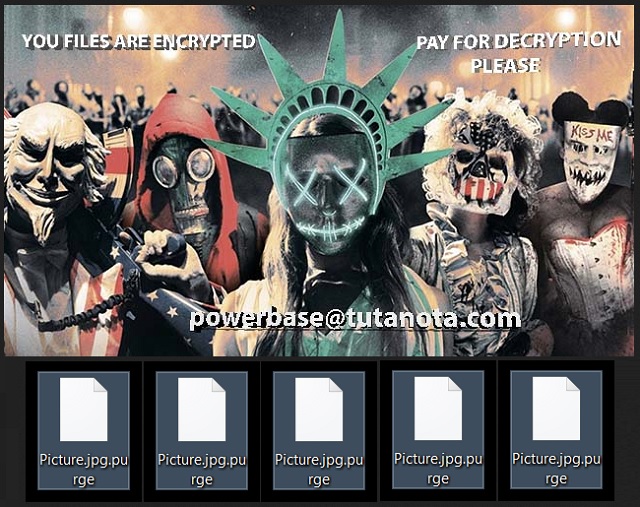
Readers recently started to report the following message being displayed when they boot their computer:
You personal ID
Your files have been encrypted with a powerfull strain of a virus called ransomware.
Your files are encrypted using rsa encryption, the same standard used by the military and banks. It is currently impossible to decrypt files encrypted with rsa encryption..
Lucky for you, wecan help. We are wiling to sell you a decryptor UNIQUELY made for your computer (meaning someone else’s decryptor will not work for you). Once you pay a small fee, we will instantly send you the software/info neccessary to decrypt all your files, quickly and easilly.
In order to get in touch with us email us at powerbase@tutanota.com. In your email write your personal ID (its located at the up of the page, it is a string of random characters). Once we receive your personal ID, we will send you payment instructions.
As proff we can decrypt you file we may decrypt 1 small file for test.
There’s a new ransomware program, plaguing users. It goes by the name Globe but is also associated with the name Purge. That’s due to the file extension it adds, as well as the picture it uses. Once the tool encrypts your data, it replaces your Desktop photo. It places one used for the movie Purge: Election Year, in its stead. More on the specifics later. How do you suppose you got stuck with such a dreadful infection in the first place? Well, it was to your own design. You were careless when you shouldn’t have been, and now you’re paying for it. Globe tends sneak into your system undetected, and when it does, you’re in trouble. All ransomware tools are malicious, meddling, and make a mess. Globe is no exception. It puts you through cyber hell. The infection locks everything you keep on your PC. All your data gets encrypted. And, you get extorted for the needed decryption key to release it. That’s how all ransomware programs work. They invade, encrypt, and extort. And, do you know what? The fourth step is that they double-cross you. Do NOT believe them! Don’t fall for their promises! It’s all a lie. If you make that mistake, you only bury yourself deeper into the abyss of disaster. So, don’t. Make the tougher but wiser choice. Cut your losses, and forsake your files. They’re not worth the risks that follow your compliance.
How did I get infected with?
It’s not quite clear which exact method the tool uses to slither in. But it’s more than likely that it sticks to the classics. The old but gold means of infiltration are preferred by most, if not all, cyber threats. So, it’s safe to assume that Globe turned to one of them for its successful invasion. The usual antics involve corrupted links or sites, or spam email attachments. The most common one, however, is freeware. It provides quite possibly the easiest access point to your system. Why? Well, for reasons unknown, users throw caution to the wind when installing freeware. They blindly agree to everything. And, don’t even bother to read the terms and conditions. That’s what you do if you WANT to get stuck with infections. But if you wish to keep your system free of cyber threats, be wary! Remember, they prey on carelessness. So, don’t grant it. Go the opposite direction! Be extra attentive and thorough. Take your time to read what you agree to before agreeing to it. Choose vigilance over distraction.
Why is Globe dangerous?
Globe turns to the not-so-common Blowfish encryption algorithm to lock your files. When it’s done, everything you have on your computer is beyond your reached. All your videos, pictures, music, documents, etc. All gets locked. The ‘purge’ extension gets added at the end of each file you have, thus, making it no longer accessible. For example, if you had a video named ‘November,’ you’ll find it as ‘November.purge.’ The extension further solidifies the ransomware’s grip over your data. Renaming or moving them won’t work. The only way to rid them, and access them again, is a decryption key. And, that will cost you. It’s all explained in the ransom note the tool leaves upon the encryption’s completion. But it’s not the usual TXT file. Globe uses a HTA, or HTML application, file to display its note. The extortionists leave you an email address to contact them. Do NOT! Do NOT contact these people! That just sends you down the path of regret. Think about how the ransom exchange goes down. Let’s examine your best-case scenario, shall we? You pay the requested sum, and receive a key. It works and decrypts your data. And, it’s free! But then what? The only thing you succeeded at is remove the current encryption. Yes, we said ‘current.’ That’s because, while you do free your files of the tool’s clutches, the tool is still there. Yes, the Globe infection still lurks somewhere on your computer. And, it can strike again at any given time. Then, you’re back to square one. Not to mention, if you comply and pay up, you open a door you shouldn’t ever open. By completing the transfer, you give access to your private life to the extortionists. They get their hands on your personal and financial information. Do you think that’s a good idea? Do you think it ends well for you? Don’t be naive. Act in your best interest. It may be hard, but say goodbye to your data. Choose privacy over pictures.
Globe Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Globe Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Globe encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Globe encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.