Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove HELLO Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
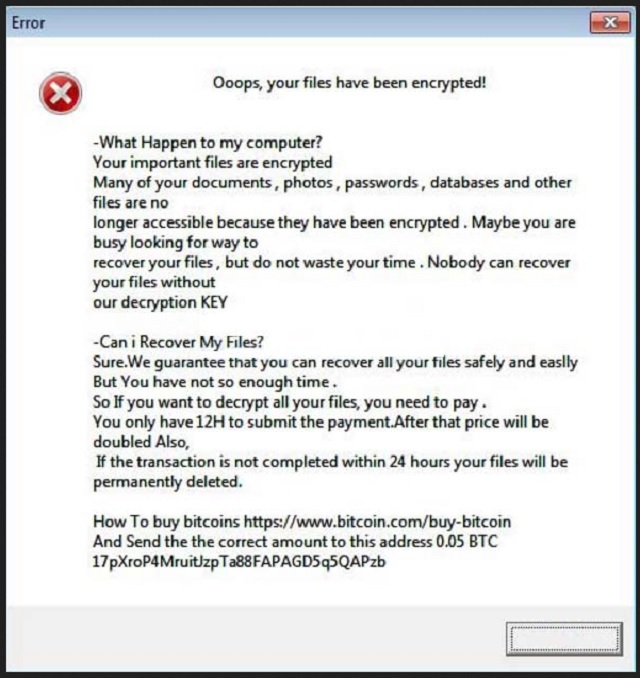
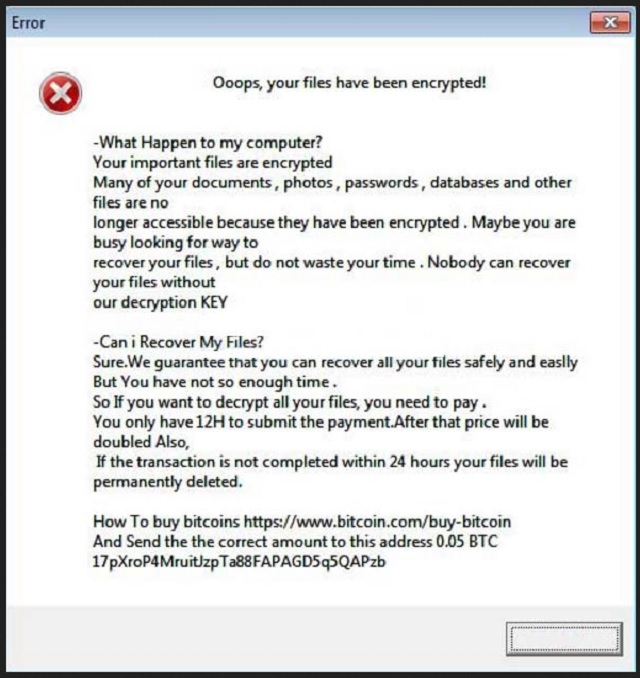
Ooops, your files have been encrypted!
-What Happen to my computer?
Your important files are encrypted
Many of your documents , photos , passwords , databases and other files are no
longer accessible because they have been encrypted . Maybe you are busy looking for way to
recover your files , but do not waste your time . Nobody can recover your files without
our decryption KEY
-Can i Recover My Files?
Sure.We guarantee that you can recover all your files safely and easily
But You have not so enough time .
So If you want to decrypt all your files, you need to pay .
You only have 12H to submit the payment.After that price will be doubled Also,
If the transaction is not completed within 24 hours your files will be permanently deleted.
How To buy bitcoins hxxps://www.bitcoin.com/buy-bitcoin
And Send the the correct amount to this address 0.05 BTC [redacted]
HELLO is the name, given to a dangerous cyber threat. An infection, part of the ransomware family. The HELLO tool is an updated version of the Xorist program. It finds a way to slither into your system undetected, then takes over. The program corrupts your data, and encrypts everything you keep on your PC. It targets your files. Pictures, videos, music, documents, everything. It locks them, using AES-265 and RSA encryption method. You find everything with a new appended ‘hello’ extension. For example, a photo named ‘me.jpg’ gets changed to ‘me.jpg.hello.‘ Once your files are under lock down, you can no longer access them. The only way to change that, is with a special decryption key. But, to get it, you have to pay a ransom. The HELLO program explain your situation, and what it expects of you, in a ransom note. It’s a TXT file, called HOW TO DECRYPT FILES.txt. You find it on your Desktop, as well as in each affected folder. It’s pretty standard. It contains information on what you’re dealing with. And, how to escape your current predicament. The ransomware gives you a choice. Pay up of lose your data. It states that if you wish to free your files, you must pay 0.05 Bitcoins. As a little extra incentive to pay up, the infection gives you a deadline. You have to send the money within the first 12 hours, or the ransom amount doubles. And, if you delay beyond 24 hours, your decryption key gets deleted. As soon as the transfer is complete, you’ll receive the decryption key you need. But, there’s the thing. There’s an entire myriad of ways, the exchange can go wrong. And, you know what? You lose in every one of them.
How did I get infected with?
The HELLO infection is quite sneaky when it comes to invasion. It’s so masterful in its deceit, that it invades undetected. Yes, you don’t realize it’s there until it clues you in. And, by that time, it’s too late as the damage is already done. Its successful infiltration relies on a few crucial elements. The infection’s sneakiness and your carelessness. Cyber threats use the old but gold means of invasion to slither in without detection. But, above all else, their success rests on your carelessness. Let’s explain. The most common methods, it turns to, include the following. Spam email attachments, freeware, corrupted links, fake updates. Take freeware, for example. Users often throw caution to the wind when installing freeware. As they come to realize, it’s a colossal mistake. This is the most preferred means of invasion, infections use. They lurk behind the freeware, and use it as a shield to conceal their presence. Here’s where your attention is a considerable asset. Apply enough caution to spot the sneaky infection, attempting infiltration. And, prevent it! To give into naivety and distraction, and rush, is to ease the tool’s invasion. Don’t make it easier for a ransomware threat to slither into your system. Carelessness opens your computer to threats. Caution helps to keep them out.
Why is HELLO dangerous?
Ransomware tools are a dread to deal with. They’re hard to detect before they strike. So, by the time you realize you have one, your files are already taken hostage. But their malice isn’t what makes them such a hazard. Yes, these programs are malicious. But, so are most cyber threats, roaming the web. What makes ransomware programs special is the fact, you can’t beat them. Once they take over, the best course of action, is to accept defeat and move on. It’s a tough call to make. But it’s the better alternative. Here’s why. The application targets the data, you have on your computer. Nothing escapes its clutches. It seizes control of your files, and extorts you. Even, with nothing else in mind, do you deem these cyber criminals reliable? Are they trustworthy? Cyber kidnappers, who seek to exploit you for monetary gain? These are hardly people, you can trust to keep their word. They will NOT hold their end of the bargain. What they will do, is double-cross you. The individuals behind the HELLO tool don’t care about you. They care about profit. Even if you follow their demands, and comply, it guarantees you nothing. They can choose not to send you the decryption key, they promised. Or, send the wrong one. And, even if they send the proper one, what then? You may remove the encryption, but the infection remains. And, it’s free to strike once more. Then, you’re back to square one. Don’t be naive. Don’t fool yourself. You cannot trust the cyber criminals behind the HELLO threat. You can’t. As harsh as it seems, say goodbye to your data. It’s better to lose your files than your privacy. Oh, yes. If you pay the ransom, you expose your private details. You give these strangers access to your personal and financial information. That won’t end well. Cut your losses. Files are replaceable. Privacy is not.
HELLO Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover HELLO Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with HELLO encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate HELLO encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.