Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Locky file extension Ransomware?
Ransomware is quite possibly the worst type of cyber infection you can catch. Sure, some people can argue that it’s not, but those, who’ve had the displeasure of dealing with one such tool know better. Granted, there are many other malicious applications, which mess up your system much worse than ransomware, but it still takes the cake. Why? Because it targets your data. The infection is programmed to attack every single file, you have stored on your PC, and take it hostage. It ‘kidnaps’ your pictures, videos, documents, music, etc., and demands you to pay ransom if you wish to liberate them. The particular ransomware, you’re currently plagued by, will encrypt everything by adding the .locky file extension at the end of each one of your files. Once that’s done, you can no longer open your files or access them in any way. Also, renaming them won’t work. Once the encryption process is complete, the only way to release your data of the infection’s captivity is to apply the proper decryption key. And, yes, you’ve guessed it. To receive said key, you have to pay. Regardless what type of ransom, the application demands, do NOT go through with it! Even if it only asks $1, which it doesn’t, do NOT pay it! It’s not worth it! To pay is only to bring yourself further into the abyss of troubles. So, don’t. Protect yourself, and don’t play by the kidnappers’ rules. To play their game is to fall deeper into the rabbit hole, and worsen your situation. Forsake your files in the name of your privacy. Every file can be replaced, but can you risk losing your personal and financial information to wicked strangers with unclear intentions, hiding behind a nasty cyber infection? Think twice before you answer for your future rests on your response.
How did I get infected with?
This particular infection has been spreading trough email containing a fishing Microsoft Word Document. The email message will contain something like ATTN: Invoice J-98225326 and a message such as “Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice”.
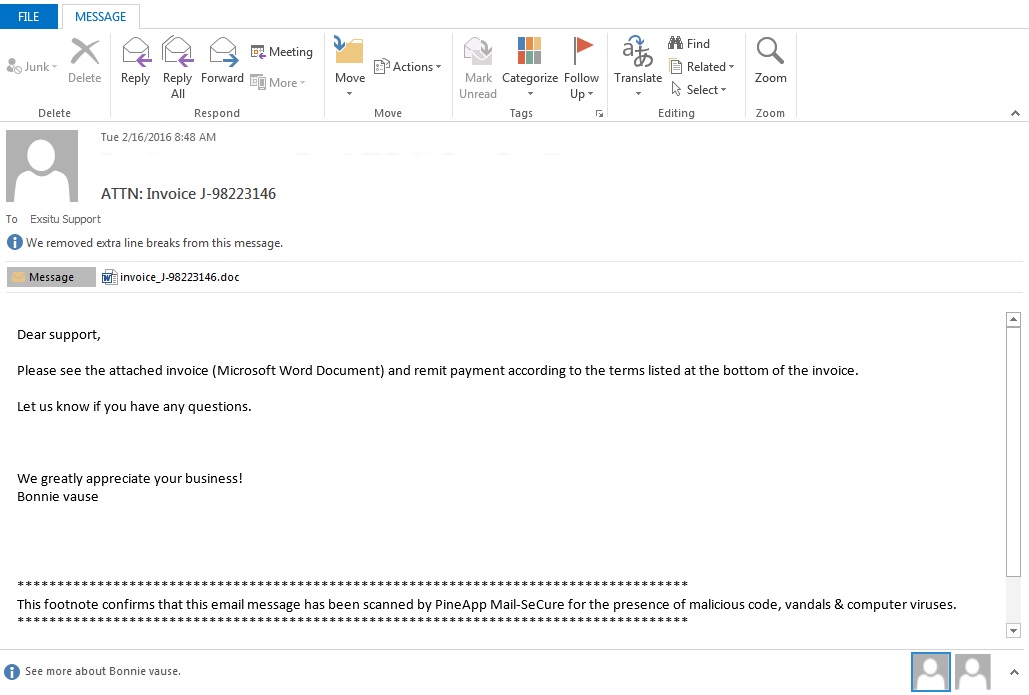
When the document is opened, you’ll see scrambled text and a message stating that you should enable the macros if the text is unreadable.
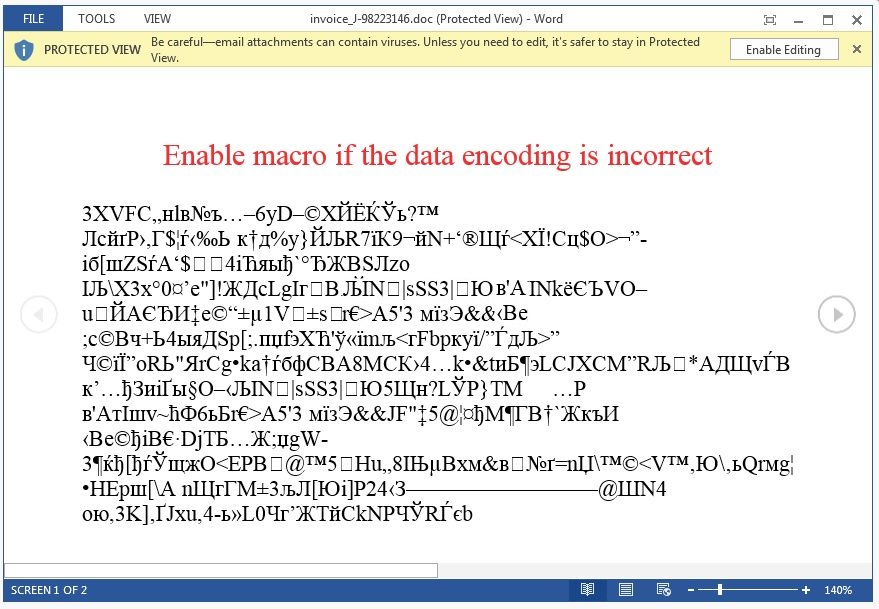
Once you are not careful and enable the macros, it will download an executable from a remote server and execute it.
The ransomware, hiding behind the Locky extension, didn’t just show up on your computer by magic. Oh, no. Infections like it require your approval before they get into your system. They’re bound to seek your permission for their installment. And, if you don’t explicitly allow it, they cannot enter. Sounds simple enough, doesn’t it? But if it is, how did it manage to slither past you undetected? Well, it’s rather straightforward. The tool didn’t openly ask for you to permit it in but, instead, did it covertly and sneakily. Ransomware applications are notoriously masterful when it comes to fooling you and, more often than not, they turn to the old but gold means of infiltration to do so. Their favorite method is through spam email attachments. Don’t open emails from suspicious, unknown senders! And, most of all, do NOT open or download the attachments they carry! It’s not safe, and it’s far from wise. It’s a gamble. One, which you should avoid at all costs. If you wish to keep your PC infection-free, be more attentive and vigilant. Don’t give into naivety and haste, and don’t be careless for infections prey on carelessness. Understand this. Even a little extra caution can save you a ton of troubles.
Why is this dangerous?
After the ransomware makes its way to your computer, you’re in for a pretty bad time. All of a sudden, you’ll find each one of your files inaccessible. Why? Because it was encrypted. How? Well, the pesky infection wastes no time, and immediately after infiltration begins the encryption process, using RSA-2048 and AES-128 ciphers. When it’s finished, you’ll find you cannot open any of your files. What’s more, they’ll be renamed. Each file, you have stored on your PC, will now appear with an additional meaningless sequence of no less than thirty-two numbers and characters, followed by the .locky extension at the end. Don’t bother changing their name for it won’t work. The only way to decrypt them, and be able to open them, is to apply the decryption key. And, lo and behold, you can! The infection offers to grant you the key, if you comply with its requirements, and pay its ransom demands. But how do you find out exactly what the ransomware wants? Well, once the malicious application has taken your data hostage, it takes over your desktop wallpaper, as well. It changes it to a warning message, which can also be found as a txt file, containing the same statement, in every one of your folders. The text is simple enough: “!!! Important information !!!! All of your files are encrypted with RSA-2048 and AES-128 ciphers. Decrypting of your files is only possible with the private key and decrypt program, which is on our secret server.” And, what now? Do you pay? Do you refuse? What? And, here’s your answer: DO NOT COMPLY! Do not pay. Just don’t. To go through with the ransom is to open the door to unknown third parties into your private life. You’ll give strangers access to your personal and financial information, and that’s something you can’t take back once you’ve done it. So, don’t do it. Make the wiser choice and say goodbye to your data. After all, it’s not worth your privacy.
Locky file extension Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Remove Locky file extension malware Manually
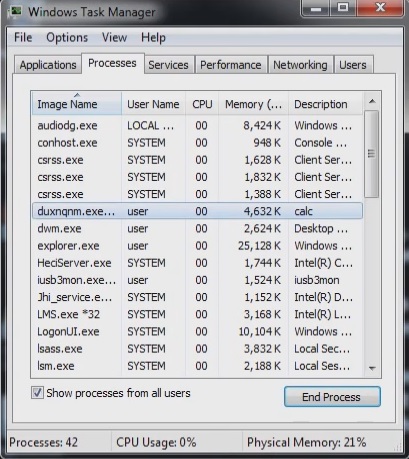
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process %Temp%\[svchost].exe
- Before you kill the process, type the name on a text document for later reference.
- Navigate to your %UserpProfile%\Desktop\ folder and delete the following files
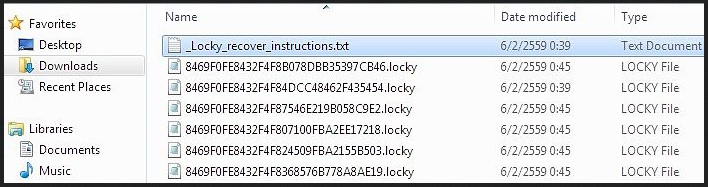
%UserpProfile%\Desktop\_Locky_recover_instructions.bmp
%UserpProfile%\Desktop\_Locky_recover_instructions.txt
%Temp%\[random].exe
- Open your Windows Registry Editor and navigate and delete the following registry keys
HKCU\Software\Locky
HKCU\Software\Locky\id
HKCU\Software\Locky\pubkey
HKCU\Software\Locky\paytext
HKCU\Software\Locky\completed 1
HKCU\Control Panel\Desktop\Wallpaper “%UserProfile%\Desktop\_Locky_recover_instructions.bmp”
Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you may wish to run a professional scanner to identify the files.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.