Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Perfc.dat Ransomware?
DO NOT PAY THE RANSOM! – read more to find out why.
Perfc.dat is a sneaky Trojan horse. It’s associated with the Petya Ransomware which should make it very clear for you how bad things are. As soon as you come across this program on your machine, know you have to take action. The more time a Trojan horse spends on board, the more dangerous it becomes. We’d recommend that you locate and delete the virus ASAP. Perfc.dat gets spread online in silence. It is hiding somewhere on your device as we speak causing you harm. Does the thought that a nasty infection has been downloaded on your PC make you feel safe? It definitely shouldn’t. The Perfc.dat virus goes after your default settings. For starters, this program modifies your system registry. Of course, that happens behind your back as no virus will seek the victim’s permission. Hackers did not create the parasite to help you surf the Web, nor to be beneficial for you. Perfc.dat serves crooks’ malicious purposes and exposes you to malware. As mentioned, this nuisance has a lot to do with Petya. For those of you unfamiliar with the file-encrypting virus, Petya is a devastating parasite. It managed to scam many gullible PC users in Europe and the USA. That means you shouldn’t take any chances when it comes to your security. If Perfc.dat is present on your computer, you’re in trouble. This pest serves as a back door to malware and makes unauthorized changes in your device. Due to its shenanigans, you won’t be able to use some of your programs. Perfc.dat makes numerous modifications without bothering to ask for permission. The parasite messes with some important system files – it modifies some and damages others. And that’s not even the whole story. Trojans could cause you some privacy issues as well. Keep in mind that the virus is monitoring your browsing history and other details at this very moment. It collects about as much data as it could get to. For instance, IP addresses, email addresses, usernames/passwords. However, the parasite could get to some personally identifiable information too. Consider your back account details threatened. Trojans provide all your sensitive data to their developers. It goes without saying how dangerous that is. Hackers are definitely not the people who should be having access to such information. They will inevitably find a way to sell your details to third parties. As a result, you could fall victim to some financial fraud or even identity theft.
How did I get infected with?
The most plausible scenario involves fake emails. Unfortunately, many people rush to open all email-attachments they receive. That is what hackers are hoping for. Every single time you come across some random email/message, be careful. Unless you personally know the sender, stay away from the emails. They might turn out to be infested with parasites and, ultimately, cause you trouble. Delete anything you find unreliable and make sure you prevent virus infiltration. It is your job and yours only to protect your PC. If you fail to do so, you will have to remove some nasty PC parasite afterwards. Do the right thing and watch out for parasites. In addition, avoid unverified websites. The Web is full of questionable pages that help malware get spread. When installing programs, go for legitimate software only. Also, stay away from suspicious-looking torrents and third-party pop-ups. Your caution will pay off so don’t be negligent online. Some parasites use exploit kits and freeware/shareware bundles to travel the Web. Last but not least, watch out for fake program updates as those are usually harmful as well.

Why is Perfc.dat dangerous?
Before you know it, you may find yourself stuck with ransomware. It’s key for your further security to remove the Perfc.dat virus on the spot. Not only does this program use stealth to get downloaded but it causes serious damage. Perfc.dat messes with your default, preferred PC settings. It could also modify your browsers and inject them with sponsored pop-up ads. Yes, you may end up bombarded with deceptive commercials, deals and coupons. You might also get redirected to unknown, potentially malicious websites. The Trojan jeopardizes your privacy by stealing sensitive data. It could grant its developers remote control over your device as well. You can clearly see that keeping the parasite on board would be a terrible mistake. Locate the pesky Trojan and regain control over your device. To do so manually, please follow our detailed removal guide down below.
Perfc.dat Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Perfc.dat Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Perfc.dat encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Perfc.dat encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.
The German e-mail provider Posteo has shut down the e-mail address that victims were supposed to use to contact the hackers in order to recover their files.
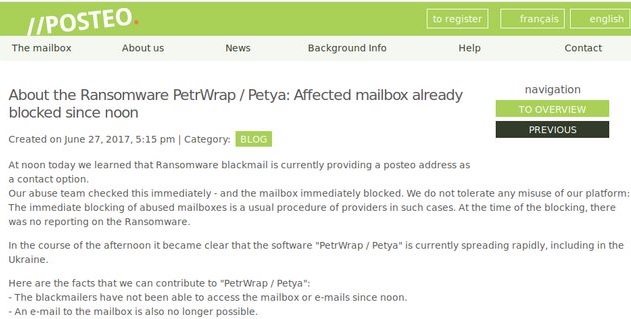
Because the e-mail address is blocked, even if you pay the ransom – there is no way you will receive a response how to get your files back. What is lost is lost. In order to avoid this from happening again it is advisable to use a reputable antimalware program which updates accordingly.
OR you can booby trap the potential vulnerable computers by tricking the ransomware that it has been already activated. Here is how to do that:
You need simply to create a bogus file called perfc in your windows directory and make it read only – that’s it. If you are hit by the virus – it will think that it has been already activate and will not encrypt your files.



