Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove XTBL File Extension Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
“All files including videos, photos and documents, etc on your computer are encrypted.
Encryptions was produced using a unique public key generated for this computer. To decrypt files, you need to obtain the private key.
The single copy of the private key, which will allow you to decrypt the files. Located on a secret server on the Internet; the server will destroy they key after a time specified in this window. After that nobody and never will be able to restore files.”
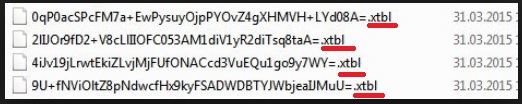
Ransomware falls under the umbrella of ‘worst cyber infections you can catch.’ And, it has earned that reputation. It’s truly one of the most dreaded tools, roaming the web. If you do get stuck with one such application, you’re in big trouble. All ransomware tend to follow the same pattern. They slither into your system undetected and reveal their presence later. They do that by taking all of your data hostages and demand you to pay a ransom to release them from the infection’s captivity. It sounds simple enough, doesn’t it? Well, few things are as simple as they seem. And, such is the case with the ransomware we’re about to discuss right now. If you suddenly find each one of your files inaccessible and renamed with an unknown file extension, you’re one of the unlucky ones, who’ve managed to get stuck with ransomware. The extension, in particular, is XTBL file extension. Let’s say you have a video named ‘awesome,’ and one day you find it as ‘awesome.xtbl.’ That’s a clear sign you’ve fallen victim to a ransomware tool. And, in turn, that means that soon you’ll be asked to pay a ransom so as to regain your files, extension-free. The ransom note is displayed as a txt file with the self-explanatory name README. It’s placed on your desktop, and sometimes it’s not just one such file. The amount varies, and it can go up to ten README.txt files. It’s usually written in both English and Russian and contains all of the ransomware’s requirements. Regardless what the tool requires of you, do NOT comply! Ransomware applications tend to double-cross users. A lot. These infections are not to be trusted. So, don’t make the mistake of placing your faith in an utterly untrustworthy tool. And, most certainly, don’t underestimate them. They’re quite capable of throwing you into a whirlwind of troubles and headaches, and altogether unpleasantness. Do yourself a favor, and throw the towel. It’s a fight you can’t win. Accept your files are lost and move on. It’s a hard pill to swallow, but the alternatives are far worse than the loss of your data. Remember, files can be replaced. Your privacy cannot.
How did I get infected with?
Ransomware cannot magically appear on your computer one day. It belongs to the group of infections, whose installation has to be approved. Yes, you have to allow the nasty tool’s install or it cannot enter. It’s bound to ask for permission before it installs itself, but make no mistake. It’s not required to do so openly. Oh, no. It does it quite covertly, and via various tricks and deception. Ransomware applications tend to resort to slyness and subtlety to dupe you into approving them into your PC. For example, some of the most commonly used methods of infiltration include hiding behind freeware, corrupted sites or links. Also, the infection can pretend to b a fake update, like Java or Adobe Flash Player. However, its usual means of invasion is through fake updates. Let’s elaborate. The ransomware tool pretends to be a bogus update, like Java or Adobe Flash Player, and while you’re convinced you’re installing updates, you’re wrong. In actuality, you’re giving the green flag to a dangerous and harmful infection. So, unless you wish to get stuck ransomware, which will add the XTBL file extension to your files and take them hostage, be more careful! Don’t give into naivety and haste, and don’t throw caution to the wind! Remember that such infections prey on carelessness, so don’t provide it.
Why is XTBL File Extension dangerous?
Once the ransomware kicks in, each one of the files you have stored on your computer will have an added XTBL extension. That includes all of your pictures, videos, music, documents, etc. The tool encrypts everything, files with any format – doc, .docx, .docm, .wps, .xls, .xlsx, .ppt, .pptx, .pptm, .pdd, .pdf, .eps, .ai, .indd, .cdr, .dng, .mp3, .lnk, .jpg, .png, .jfif, .jpeg, .gif, .bmp, .exif, .txt. Nothing is safe from its reach. After the encryption is complete, and you find them in the changed file format to .xtbl, you will no longer be able to open them. That’s right. They’ll be inaccessible. And, no matter how many times you rename them and remove the extension, they’ll remain so. The only way to open them again is to apply the decryption key. And, here’s the kicker. To get it, you have to comply with the infection’s requirements. Once you go through with its demands, it will supply you with the key, which will, supposedly, decrypt your files. But, here’s a question you have to ask yourself: “Can a ransomware infection be trusted?” And, as was already established several times over, the answer is ‘No.’ The odds are not in your favor as the game is rigged from the start. Consider this. What do you believe to be your best-case scenario? You pay the ransom, the infection hand over the decryption key, you apply it, it works, and your files are free. But then what? What’s to stop the tool from kicking back again the very next day and taking your data hostage once more? Nothing. And, you’ll be back to square one. Only this time, you’ve lost money and, what’s worse, you’ve opened the door to your private life to wicked strangers with agendas. Oh, yes. By paying up, you’ve given access to your personal and financial details to the individuals that published the infection. Don’t allow unknown third parties into your privacy! And, furthermore, we’re not talking about chump change. The ransomware behind the XTBL extension tends to ask around $400 for the decryption key. So, ask yourself: Are my files worth $400 and my privacy? Figure out your priorities before you answer.
XTBL File Extension Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover XTBL File Extension Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with XTBL File Extension encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate XTBL File Extension encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.