Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Srpx Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
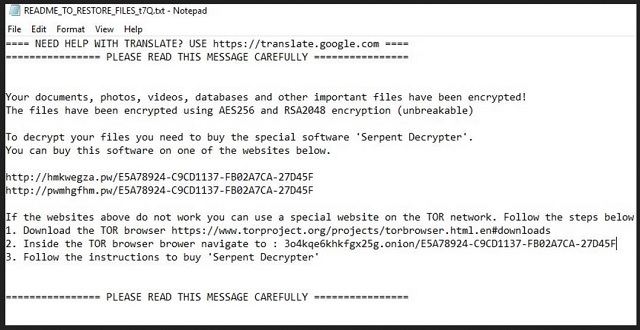
==== NEED HELP WITH TRANSLATE? USE https://translate.google.com ====
================ PLEASE READ THIS MESSAGE CAREFULLY ================
Your documents, photos, videos, databases and other important files have been encrypted!
The files have been encrypted using AES256 and RSA2048 encryption (unbreakable)
To decrypt your files you need to buy the special software ‘Serpent Decrypter’.
You can buy this software on one of the websites below.
xxxx://hmkwegza.pw/E5A78924-C9CD1137-FB02A7CA-27D45F
xxxx://hnxrvobhgm.pw/E5A78924-C9CD1137-FB02A7CA-27D45F
If the websites above do not work you can use a special website on the TOR network. Follow the steps below
1. Download the TOR browser https://www.torproject.org/projects/torbrowser.html.en#downloads
2. Inside the TOR browser brower navigate to : 3o4kqe6khkfgx25g.onion/ E5A78924-C9CD1137-FB02A7CA-27D45F
3. Follow the instructions to buy ‘Serpent Decrypter’
================ PLEASE READ THIS MESSAGE CAREFULLY ================
The Serpent Ransomware has been harassing PC users since February. And, you’re currently dealing with the latest version of this parasite. Just the fact that it’s a ransomware-type infection should be enough to make you take action ASAP. There is a reason why these viruses are considered to be among the most troublesome types of malware. Ransomware is no threat to be taken lightly. In fact, it aims straight at your bank account in attempts to steal your Bitcoins. How does the scheme work? As soon as the virus gets downloaded, it scans your PC. By doing so, this program locates all your private files. It then uses the AES-256 and RSA-2048 cipher to encrypt your data. That includes photos, music files, videos, documents. Ransomware targets all the private information you’ve stored on your computer. If that sounds terrifying, that’s because it is. Nothing is safe now that the ransomware is present. You probably keep some very personal, important files on board. They all fall victims to the parasite’s trickery. Did you already spot that your files are now renamed? This infection adds the .srpx extension. It renames all your information which indicates that the encryption process is complete. There’s no more using the files on your computer. Ransomware uses a complicated encrypting algorithm to make your data unreadable. Needless to say that it successfully turns the target files into unusable gibberish. Your very own files get locked and are then being held hostage. Do you see the scam already? Hackers hit where they know they will make the biggest impact. By going after your personal files, crooks are trying to catch your attention. With all your personal information being renamed and locked, you will inevitably notice the parasite. What you notice next is the ransom note this program drops. Once your data gets encrypted, the virus creates the “README_TO_RESTORE_FILES_.html” files. Those are your payment instructions. The ransom notes get added to all files that contain encrypted files. Your desktop wallpaper might get modified as well. As you could imagine, hackers’ goal is to force their messages on you all the time. The more often you see the instructions, the more likely it is that you follow them. Ultimately, crooks are trying to trick you into buying a special decryption key. Keep in mind that making a deal with hackers could only cause you further trouble, though.
How did I get infected with?
Ransomware usually gets presented as a perfectly harmless email or message. This way, your curiosity helps hackers get the job done. If you receive some random email-attachment, know there might be a virus hiding behind it. Don’t hesitate to delete the spam messages and emails you might come across. This may save you quite the headache later on. Remember, preventing malware infiltration is much easier than deleting viruses. Unless you pay attention, you’ll have to deal with the consequences of your own negligence. Hence, keep an eye out for potential intruders and make sure you device remains virus-free. Now that you know exactly how dangerous ransomware is, are you going to allow such a virus to get downloaded again? Stay away from the questionable job applications and emails from shipping companies you may receive. Those could turn out to be filled with malware and cause you serious harm. Another popular infiltration method involves fake torrents or bogus program updates. Restrain yourself from installing unreliable software and avoid unverified websites. Last but not least, ransomware could often use some help from Trojan horses to get installed. That means you should check out your device for other infections.
Why is Srpx dangerous?
The virus encrypts all your precious, favorite data. It leaves you unable to use any of your files and even attempts to blackmail you. As we mentioned already, this program drops ransom messages. According to these notes, you have to make a payment in order to receive a decryptor. The only problem is that agreeing to this deal leads you directly into hackers’ trap. Don’t let crooks fool you into thinking paying could restore your encrypted data. If anything, it would make matters worse as hackers will get access to your bank account details that way. Before you know it, things may go from bad to terrible. Keep your Bitcoins and ignore hackers’ stubborn attempts to involve you in a fraud. You should know better than to allow cyber criminals to scam you. To delete the ransomware manually, please follow our removal guide down below.
Srpx Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Srpx Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Srpx encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Srpx encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



