Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Johnycryptor@aol.com Ransomware?
“What is the worst type of cyber infection, roaming the Internet?” If you had to answer that question, what would be your response? We dare argue that most Internet users will share the same reply: ransomware. There are, undoubtedly, many other infections, which cause far worse damages, but ransomware takes the title since it targets your files. These hazardous applications are designed to attack every single file you have stored on your computer. They take it hostage by encrypting it and, thus, render it inaccessible, and then demand ransom. It’s quite the diabolical scheme, and since it’s so close to heart, it’s hardly surprising that most users consider ransomware to be the worst kind of danger, lurking on the web. When the nasty tool slithers into your system, you’re in for a pretty bad experience. As was already mentioned, the pesky program encrypts your data and requires ransom. Supposedly, if you comply and pay up, it will grant you a decryption key, which will set you files free. But there are NO guarantees this is how the exchange will go down. There are several ways it can play out and, unfortunately, they all end quite unpleasant for you. That’s why experts strongly advise towards making the hard choice NOT to comply with the demands and forsake your files. It’s a tough decision to make, but it’s the right one. If you’re reading this, you’re currently plagued by ransomware, associated with the Johnycryptor@aol.com email address.
How did I get infected with?
Ransomware tends to resort to the old but gold means of infiltration to sneak into your system. And, it’s not only successful in its advances and manages to invade your PC, but also does it without you realizing it. That’s right. The tool enters undetected, and you only become aware of its existence when it goes to work and encrypts your data. Until that time comes, you’re clueless. The program’s usual trickery includes hitching a ride with corrupted links or sites, or freeware. It can also pretend to be a fake system or program update. For example, while you’re convinced you’re updating your Java or Adobe Flash Player, you’ll be installing a dreadful infection. However, the ransomware’s most commonly used method of invasion is through spam email attachments. To prevent the infection from entering your system and making a colossal mess, be more cautious! Know that cyber infections prey on carelessness, so do your best NOT to provide it. Even a little extra attention can go a long, long way. Be more vigilant, do your due diligence, and don’t give into distraction, naivety, and haste. If you follow that advice, you increase your chances of NOT waking up to find your system overtaken by ransomware, affiliated with the Johnycryptor@aol.com address.
Why is Johnycryptor@aol.com dangerous?
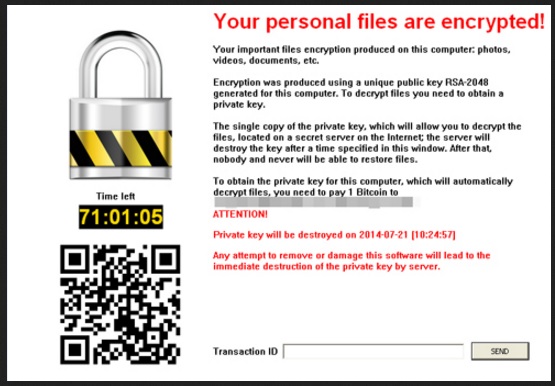
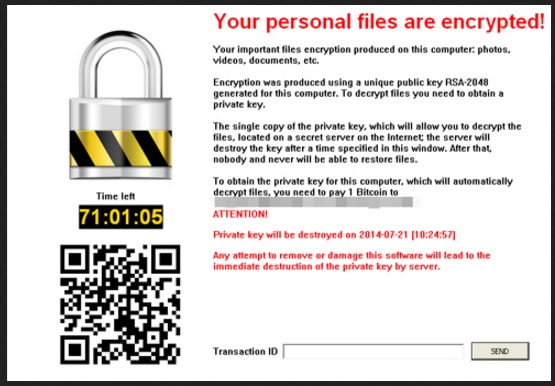
After the infection, connected to Johnycryptor@aol.com, slithers into your system, it hardly wastes time. Soon after infiltration, you are greeted by the unfortunate sight of finding your files encrypted. Everything falls victim to the encryption process, files of every type: jpeg, .pptm, .pptx, .jpg, .png, doc, .docx, .xls, .xlsx, .ppt, .odt, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .xml, .psd, .java, .xlsb, .xlsm, .db, .docm, .sql, .pdf. The ransomware adds some extension at the end of each one, thus, rendering it inaccessible. Yes, after the infection is done and the extension is added, you can no longer open a single one of your files. Then the tool presents you with a choice: pay up and get back your data or lose it. To some of you, it may seem like a no-brainer – do everything you have to so as to save your data. To these people, we say ‘wrong choice.’ Do NOT comply with the infection’s demands! Even if it asks you to pay a single dollar, deny it! You’ll only fall deeper into the rabbit hole if you do. And, in any case, the tool asks more than a dollar, $500 to be exact. The warning it displays after it’s done with the encryption, states that you are required to pay in bitcoin, a sum between $400 and $500, and you have 48 or 96 hours to do it. After that time limit passes, you lose your data. The infection backs you up into a corner and hopes that you panic and fear of losing your files gets the better of you. We say it again: do NOT comply with the demands! Every scenario ends with you, filled with regrets, and stuck in an even worse situation. And, consider this. If you pay the ransom, you’ll allow wicked strangers with questionable intentions into your private life. You’ll grant them access to your personal and financial information. Do you think that’s wise? Do you think it will end well for yourself? Hardly. In the dilemma between your data and your privacy, your choice should be quite clear. Figure out your priorities, and act accordingly. But remember, files can be replaced. While, if you open the door to your private life to unknown individuals, you can no longer close it.
Johnycryptor@aol.com Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Johnycryptor@aol.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Johnycryptor@aol.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Johnycryptor@aol.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.