Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Red CERBER Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
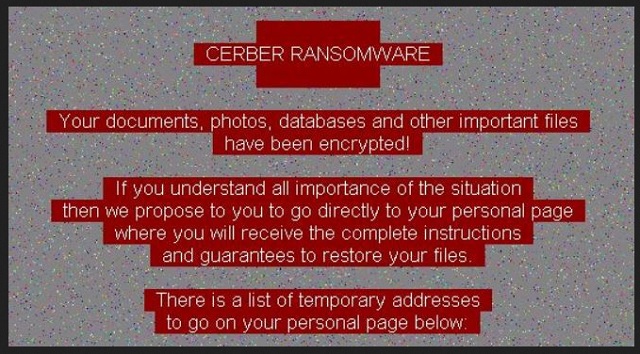
CERBER RANSOMWARE
YOUR DOCUMENTS, PHOTOS, DATABASES AND OTHER IMPORTANT FILES HAVE BEEN ENCRYPTED1
The only way to decrypt your files is to receive
the private key and decryption program.
To receive the private key and decryption program
go to any decrypted folder – inside there is the special file (*README*)
with complete instructions how to decrypt your files.
If you cannot find any (*README*) file at your PC,
follow the instructions below:
1. Download “Tor Browser” from https://www.torproject.org/ and install it.
2. In the “Tor Browser” open your personal page:
http://p27dokhpz2n2nvgr.onion/DC91-E730-12F8-0095-7496
Note! This page is available via “Tor browser” only.
It’s safe to say that 2016 was the year of Cerber. Meet its latest addition. Unfortunately, 2017 is just getting started and yet here we go again. The Red CERBER Virus is just as devastating and destructive as all the other Cerber variants. So far, we’ve tackled Cerber, Cerber2, Cerber3, Cerber4 and Cerber5. Quite a malicious company, don’t you think? It seems hackers aren’t willing to neglect this program anytime soon. Cerber is just getting more problematic so, to put it mildly, your situation is bad. The virus you’re now stuck with is notoriously dreaded. To begin with, this is ransomware. Also known as the most harmful type of parasite currently on the Web. There is a reason nobody wants to be dealing with ransomware-type infections. These programs lock your private files and demand a ransom afterwards. You see, that’s is actually a clever attempt for a cyber fraud. It’s no secret hackers are trying to gain illegitimate revenue online. This is where ransomware in general and Red CERBER in particular come in handy. Red CERBER follows the classic ransomware pattern. It also shares many similarities with the other members of the Cerber family. Apart from the red color, its ransom notes are almost the same. There is one big difference that’s worth mentioning, though. While the previous Cerber versions delete shadow volume copies, Red CERBER keeps them. That means it leaves you a chance to get your files back. This chance is highly theoretical as the parasite’s encrypting cipher is beyond complicated. However, researchers are constantly working on decrypting tools. Keep in mind you should never negotiate with hackers despite what their ransom notes say. As soon as the ransomware gets activated, it scans your PC system. By doing so, Red CERBER finds all the data that it will encrypt. Pictures, music, videos, presentations, MS Office documents, etc. The information you’ve stored on your device gets locked and turned into gibberish. Red CERBER adds a random extension to the target data thus messing with its format. If you come across a brand new file appendix, this is a clear sign you won’t be able to use your data anymore. Now that your data is modified, your PC won’t be able to open it. As a result, the ransomware effectively denies you access to all your precious, important files. It then attempts to trick you into paying a certain sum of money. Long story short, the very LAST thing you should do is follow hackers’ instructions.
How did I get infected with?
There are several particularly popular techniques. Number one involves spam messages and email-attachments. You see, crooks often send parasites directly to your inbox. You end up compromising your own PC by opening a malicious email. Hence, you must pay attention to what you receive. Unless you personally know the sender, you better restrain yourself from opening that email. Same thing goes for the messages in your social media. Infections may pretend to be sent from a shipping company. They might also get disguised as job applications so be careful. One single wrong click is more than enough to cause you a serious headache. Ransomware also gets spread via exploit kits, illegitimate torrents and fake software updates. Avoid unverified websites/programs and always be cautious online. The parasite might have sneaked itself onto your device with the help of a Trojan horse. Therefore, check out the machine for more parasites. Red CERBER could be having company on your system. Last but not least, ransomware travels the Web via freeware and shareware bundles. Now that you know how harmful viruses could be, protect your PC from malware. You won’t regret it.
Why is Red CERBER dangerous?
The ransomware modifies your personal files. It encrypts all the private data on your PC and makes it inaccessible. As you could imagine, many people would give into their despair and anxiety seeing these sudden changes. This is precisely what hackers aim for. Once you panic, you stop thinking logically. And once you stop thinking logically, you forget that making a deal with crooks is a terribly bad idea. The parasite’s developers do promise you a decryptor. In exchange for your Bitcoins, you’re supposed to receive this unique combination of symbols. However, paying the ransom guarantees you absolutely nothing. Do not download any Tor browser and do not let hackers scam you. Ransomware is just a nasty way for cyber criminals to blackmail gullible PC users. Remember, hackers are not to be trusted despite what they claim. To delete the ransomware manually, please follow our detailed removal guide down below.
Red CERBER Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Red CERBER Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Red CERBER encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Red CERBER encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.